CISA warns of Windows bug exploited in ransomware attacks
by nlqip

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity Windows vulnerability abused in ransomware attacks as a zero-day to its catalog of actively exploited security bugs.
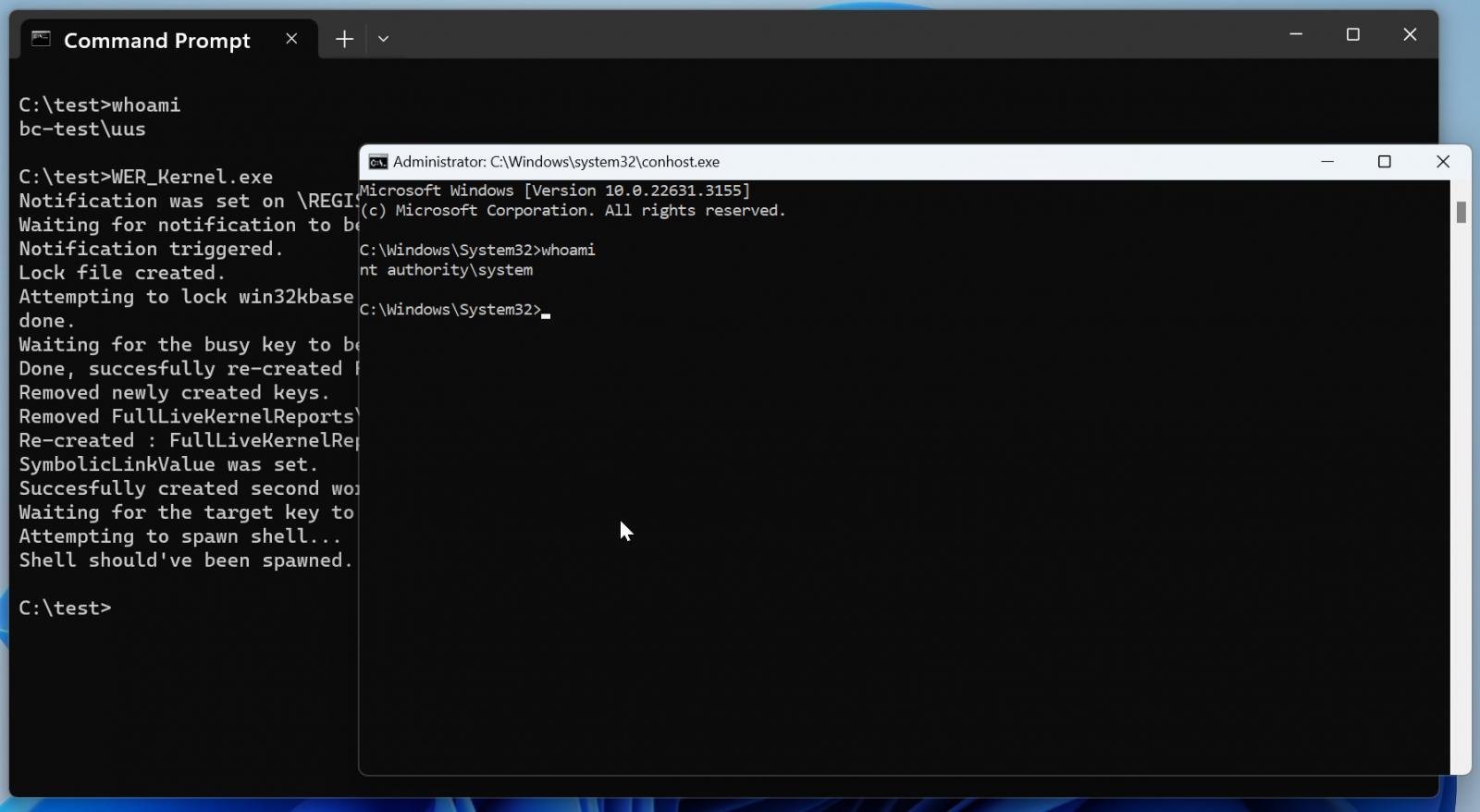
Tracked as CVE-2024-26169, this security flaw is caused by an improper privilege management weakness in the Windows Error Reporting service. Successful exploitation lets local attackers gain SYSTEM permissions in low-complexity attacks that don’t require user interaction.
Microsoft addressed the vulnerability on March 12, 2024, during its monthly Patch Tuesday updates. However, the company has yet to update its security advisory to tag the vulnerability as exploited in attacks.
As revealed in a report published earlier this week, Symantec security researchers found evidence that the operators of the Black Basta ransomware gang (the Cardinal cybercrime group, also tracked as UNC4394 and Storm-1811) were likely behind attacks abusing the flaw as a zero-day.
They discovered that one variant of the CVE-2024-26169 exploit tool deployed in these attacks had a February 27 compilation timestamp, while a second sample was built even earlier, on December 18, 2023.
As Symantec admitted in their report, such timestamps can easily be modified, rendering their zero-day exploitation findings inconclusive. However, there is little to no motivation for the attackers to do so, making this scenario unlikely.
This suggests that the ransomware group had a working exploit between 14 and 85 days before Microsoft released security updates to patch the local privilege elevation flaw.
Three weeks to secure vulnerable systems
Federal Civilian Executive Branch Agencies (FCEB) agencies must secure their systems against all vulnerabilities added to CISA’s catalog of Known Exploited Vulnerabilities, according to a November 2021 binding operational directive (BOD 22-01).
On Thursday, CISA gave FCEB agencies three weeks, until July 4, to patch the CVE-2024-26169 security and thwart ransomware attacks that could target their networks.
Although the directive only applies to federal agencies, the cybersecurity agency also strongly urged all organizations to prioritize fixing the flaw, warning that “These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.”
Black Basta emerged as a Ransomware-as-a-Service (RaaS) operation two years ago, in April 2022, after the Conti cybercrime gang split into multiple factions following a series of embarrassing data breaches.
Since then, the gang has breached many high-profile victims, including German defense contractor Rheinmetall, U.K. technology outsourcing company Capita, the Toronto Public Library, the American Dental Association, government contractor ABB, Hyundai’s European division, Yellow Pages Canada, and U.S. healthcare giant Ascension.
CISA and the FBI revealed that Black Basta ransomware affiliates have hacked over 500 organizations until May 2024, encrypting systems and stealing data from at least 12 U.S. critical infrastructure sectors.
According to research from Corvus Insurance and cybersecurity company Elliptic, Black Basta collected at least $100 million in ransom payments from over 90 victims until November 2023.
Source link
lol
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity Windows vulnerability abused in ransomware attacks as a zero-day to its catalog of actively exploited security bugs. Tracked as CVE-2024-26169, this security flaw is caused by an improper privilege management weakness in the Windows Error Reporting service. Successful exploitation lets local attackers gain…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
