Keytronic confirms data breach after ransomware gang leaks stolen files
by nlqip

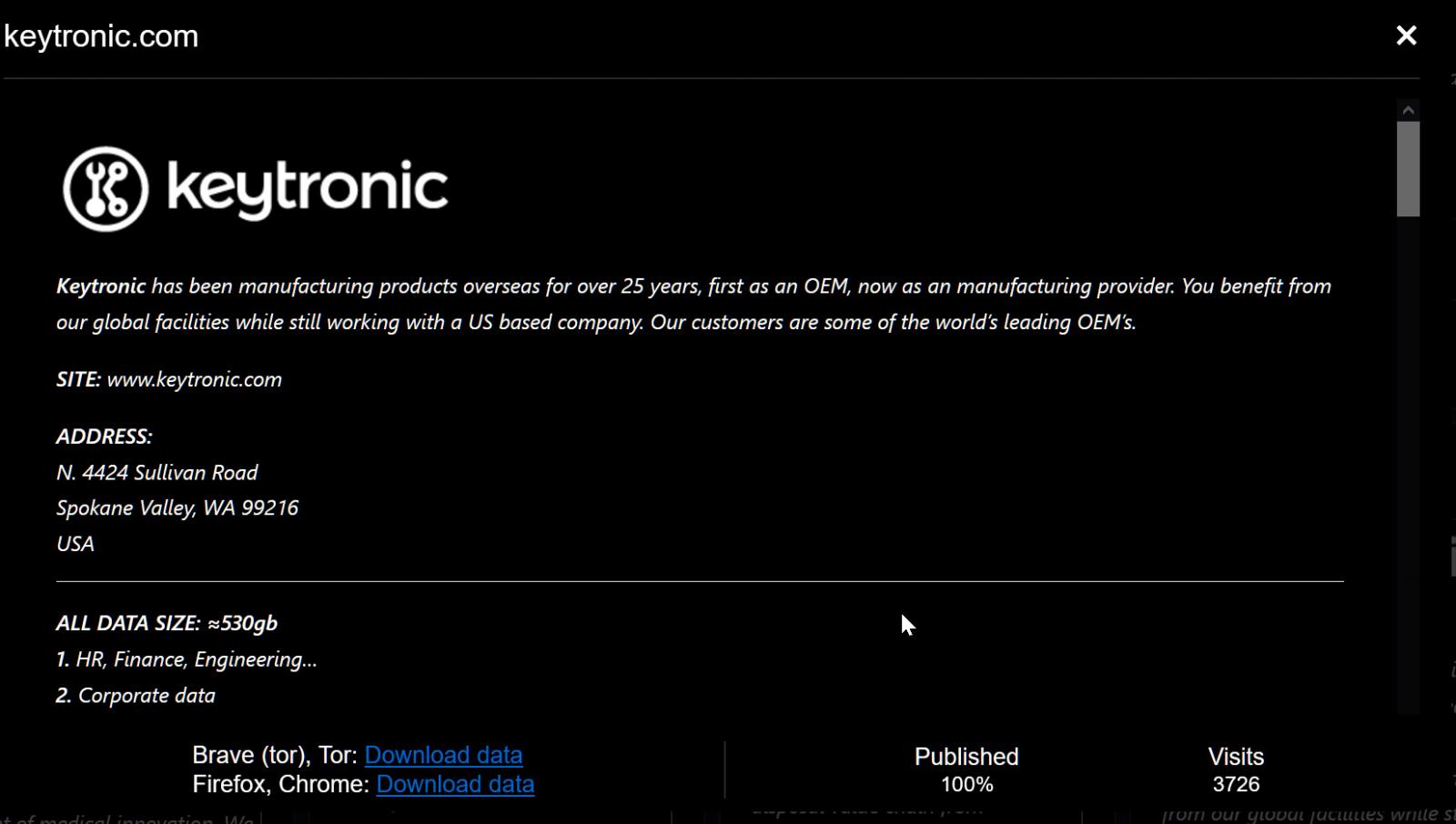
PCBA manufacturing giant Keytronic is warning it suffered a data breach after the Black Basta ransomware gang leaked 530GB of the company’s stolen data two weeks ago.
Key Tronic, better known as Keytronic, is an American technology company that initially started as an Original Equipment Manufacturer (OEM) of keyboards and mice but is now one of the largest manufacturers of printed circuit board assembly (PCBA).
Last month, Keytronic disclosed in an SEC filing that it had suffered a cyberattack on May 6 that disrupted its operations, limiting access to business applications that supported corporate activities.
In a late Friday afternoon filing with the SEC, the Company states that the attack also caused them to shut down domestic and Mexico operations for two weeks while they responded to the attack and that normal operations have now resumed.
The filing also states that their investigation confirmed the threat actors stole personal information during the attack.
“Since the date of the Original Report, the Company has determined that the threat actor accessed and exfiltrated limited data from the Company’s environment, which includes some personally identifiable information,” reads the FORM 8-K/A SEC filing.
“The Company is in the process of providing appropriate notifications to potentially affected parties and to regulatory agencies as required by applicable law.
As required by new SEC guidelines, the Company has also confirmed that the attack and loss of production will have a material impact on the Company’s financial condition during the fourth quarter ending June 29, 2024.
The Company says it has already incurred approximately $600,000 in expenses related to hiring external cybersecurity experts and that these expenses may continue.
While Keytronic didn’t attribute the attack to a specific threat group, the Black Basta ransomware operation claimed the attack two weeks ago, leaking what they claim is 100% of the stolen data.
Source: BleepingComputer
The threat actors claim that human resources, finance, engineering, and corporate data were stolen in the attack, sharing screenshots of employees’ passports and social security cards, customer presentations, and corporate documents.
BleepingComputer asked Keytronic how many people were impacted by the data breach but did not receive an answer before publication.
Black Basta
The Black Basta ransomware operation launched in April 2022 and is believed to consist of former members of the Conti ransomware operation, who splintered into smaller groups after they shut down.
Black Basta has since become one of the most significant ransomware operations, responsible for a large number of attacks, including those against Capita, Hyundai’s European division, the Toronto Public Library, the American Dental Association, and more recently, a ransomware attack that hit U.S. healthcare giant Ascension.
Last month, CISA and the FBI revealed that the ransomware operation was responsible for breaching 500 organizations between April 2022 and May 2024, stealing data from at least 12 out of 16 critical infrastructure sectors.
According to cybersecurity company Elliptic and cyber insurance firm Corvus Insurance research, Black Basta has extorted at least $100 million in ransom payments from over 90 victims through November 2023.
Source link
lol
Image: Keytronic PCBA manufacturing giant Keytronic is warning it suffered a data breach after the Black Basta ransomware gang leaked 530GB of the company’s stolen data two weeks ago. Key Tronic, better known as Keytronic, is an American technology company that initially started as an Original Equipment Manufacturer (OEM) of keyboards and mice but is now one of…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
