Los Angeles Unified confirms student data stolen in Snowflake account hack
by nlqip

The Los Angeles Unified School District has confirmed a data breach after threat actors stole student and employee data by breaching the company’s Snowflake account.
SnowFlake is a cloud database platform used by some of the largest companies worldwide to store their data.
Earlier this month, a threat actor began to sell data from numerous companies, including TicketMaster, Satandar Bank, Advance Auto Parts, and Pure Storage, with the hacker stating it was stolen from SnowFlake.
A joint investigation by SnowFlake, Mandiant, and CrowdStrike revealed that a threat actor, tracked as UNC5537, used stolen customer credentials to target at least 165 organizations that had not configured multi-factor authentication protection on their accounts.
Once they accessed the accounts, they downloaded all the data and attempted to extort the company in exchange for not selling or leaking the data to other cybercriminals.
LAUSD sold on a hacker forum
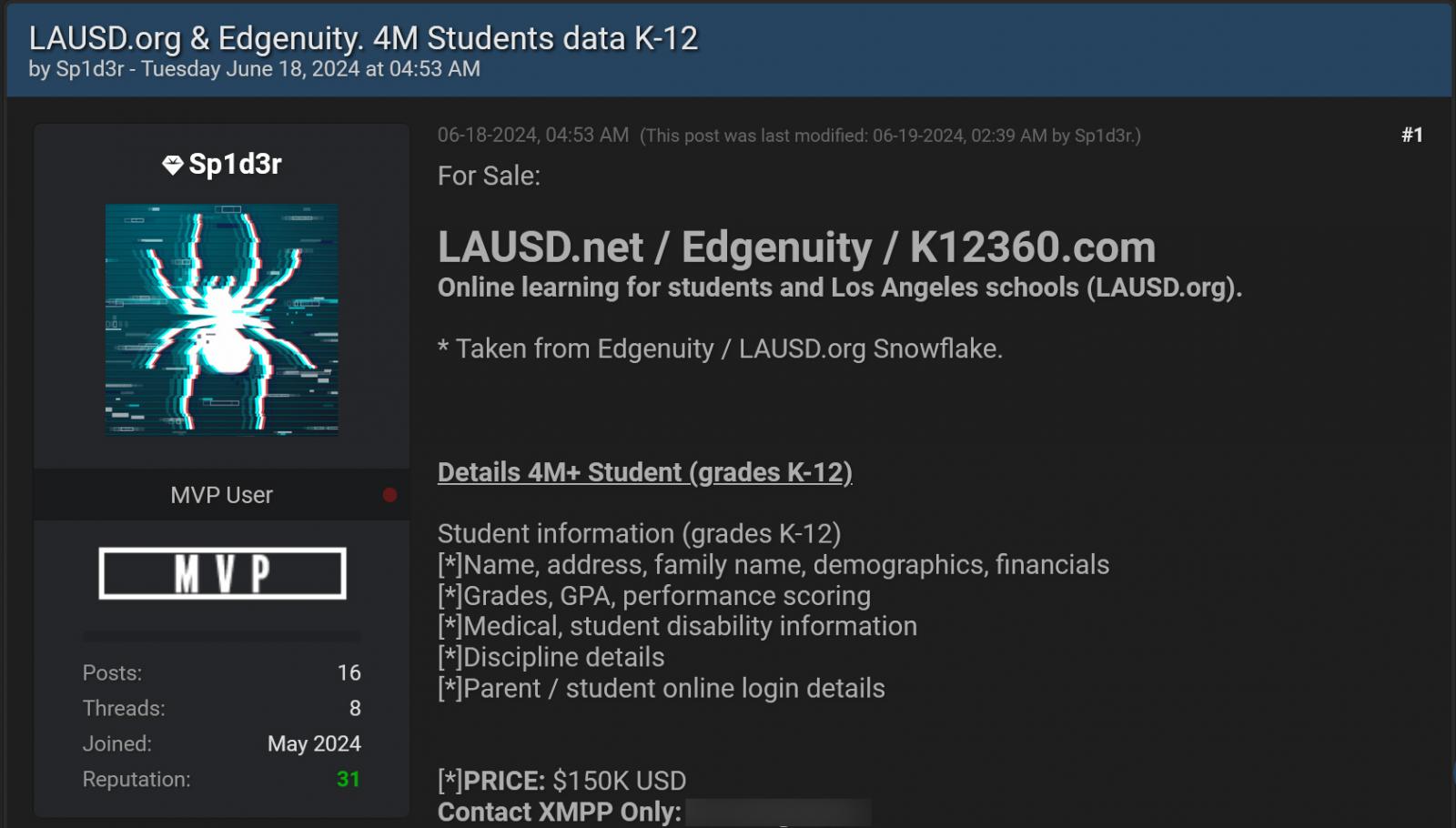
On June 18, the threat actor known as ‘Sp1d3r, who is selling data from previous SnowFlake attacks, also began selling the data of Los Angeles Unified for $150,000, claiming they stole it from SnowFlake.
Source: BleepingComputer
The threat actor states this data contains student names, addresses, family names, demographics, financials, grades, performance scoring, disability information, discipline details, and parent information.
After reviewing a sample of the data, LAUSD confirmed to BleepingComputer that the data was stolen from its SnowFlake account.
“As previously stated, on June 6, 2024, Los Angeles Unified became aware of an account from a malicious actor purporting to offer certain student and employee data for sale,” a Los Angeles Unified spokesperson told BleepingComputer.
“Through its extensive and ongoing investigation, the District has determined that the data in question was maintained by one or more Los Angeles Unified external vendors on Snowflake, a cloud-based platform used for mass data storage, and appears to have been stolen in a manner consistent with recently publicized thefts involving numerous Snowflake accounts.”
“So far, the District’s ongoing investigation has revealed no evidence of any compromise to our systems or networks; however the investigation into the scope and extent of the data impacted is ongoing.”
Los Angeles Unified says they are working with the FBI, CISA, and its vendors to investigate the incident further.
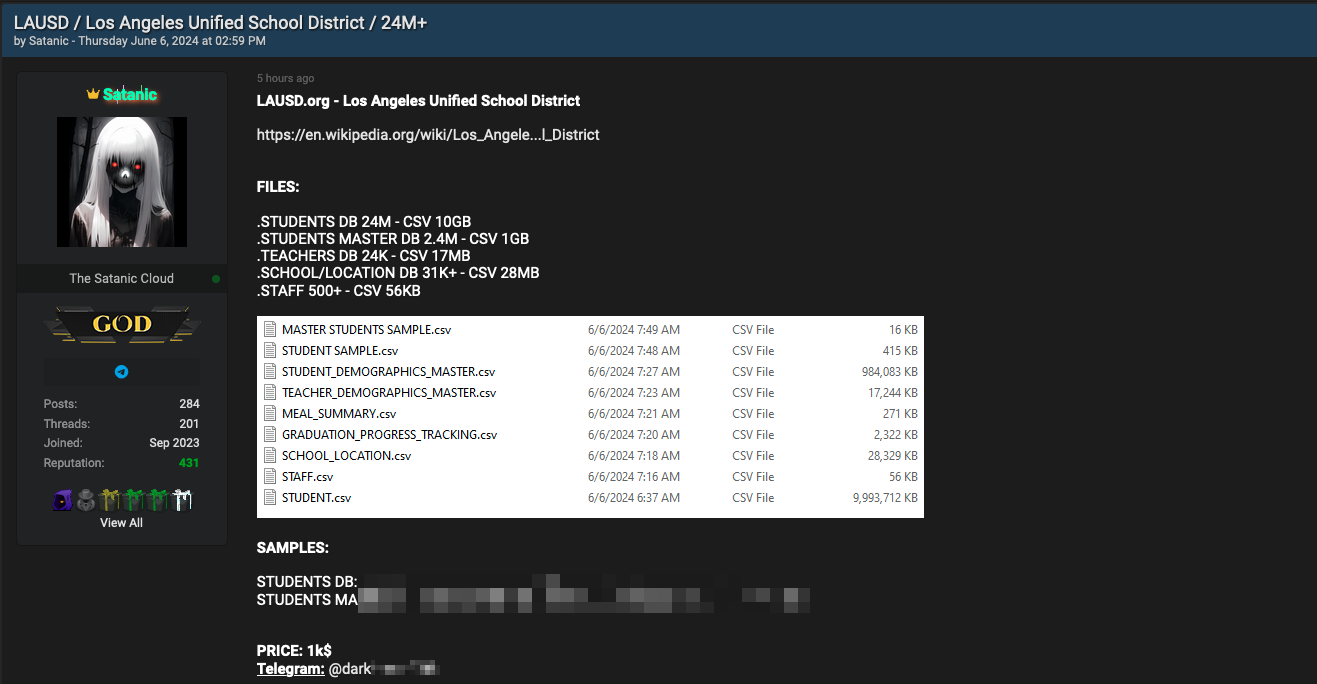
More than one threat actor apparently gained access to Los Angeles Unified’s data, as a different threat actor named ‘Satanic’ began selling the district’s data almost two weeks earlier, on June 6, for $1,000.
However, this data appears to be different than the data stolen from SnowFlake, with the threat actor claiming it contains 26 million records with current and former student information, more than 24,000 teacher records, and around 500 containing staff information.
Source: BleepingComputer
This threat actor has now released it for free, allowing any cybercriminal to download and use it in their own attacks.
However, it is unclear where this data originated from, as it does not appear to have come from SnowFlake.
BleepingComputer contacted LAUSD last night to confirm the origins of the data leaked by ‘Satanic’ but did not receive a response.
At this point, with the massive amount of data from LAUSD now shared on hacking forums, all of its students, teachers, and staff members should consider their data exposed.
As it is not uncommon for other threat actors to use leaked data in their campaigns, it is crucial to stay vigilant against unsolicited emails, texts, and phone calls attempting to steal additional data, such as passwords.
Source link
lol
The Los Angeles Unified School District has confirmed a data breach after threat actors stole student and employee data by breaching the company’s Snowflake account. SnowFlake is a cloud database platform used by some of the largest companies worldwide to store their data. Earlier this month, a threat actor began to sell data from numerous…
Recent Posts
- QNAP addresses critical flaws across NAS, router software
- New Windows 10 0x80073CFA fix requires installing WinAppSDK 3 times
- Blue Yonder ransomware attack disrupts grocery store supply chain
- DOJ: Man hacked networks to pitch cybersecurity services
- Microsoft blocks Windows 11 24H2 on some PCs with USB scanners
