A likely China-linked state-sponsored threat actor has been linked to a cyber espionage campaign targeting government, academic, technology, and diplomatic organizations in Taiwan between November 2023 and April 2024.
Recorded Future’s Insikt Group is tracking the activity under the name RedJuliett, describing it as a cluster that operates Fuzhou, China, to support Beijing’s intelligence collection goals related to the East Asian country. It’s also tracked under the names Flax Typhoon and Ethereal Panda.
Among other countries targeted by the adversarial collective include Djibouti, Hong Kong, Kenya, Laos, Malaysia, the Philippines, Rwanda, South Korea, and the U.S.
In all, as many as 24 victim organizations have been observed communicating with the threat actor infrastructure, including government agencies in Taiwan, Laos, Kenya, and Rwanda. It’s also estimated to have targeted at least 75 Taiwanese entities for broader reconnaissance and follow-on exploitation.
“The group targets internet-facing appliances such as firewalls, load balancers, and enterprise virtual private network VPN products for initial access, as well as attempting structured query language SQL injection and directory traversal exploits against web and SQL applications,” the company said in a new report published today.
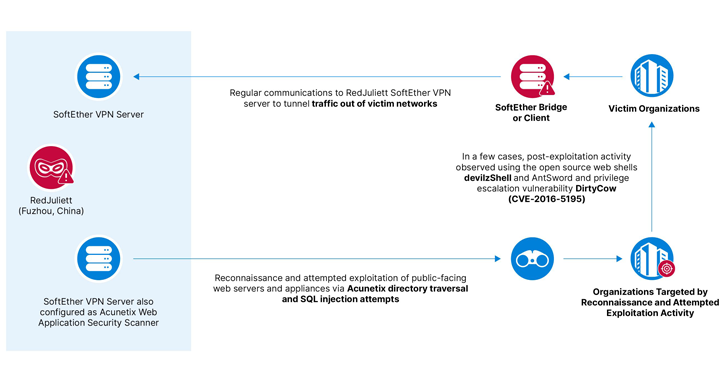
As previously documented by CrowdStrike and Microsoft, RedJuliett is known to employ the open-source software SoftEther to tunnel malicious traffic out of victim networks and leverage living-off-the-land (LotL) techniques to fly under the radar. The group is believed to be active since at least mid-2021.
“Additionally, RedJuliett used SoftEther to administer operational infrastructure consisting of both threat actor-controlled servers leased from virtual private server VPS providers and compromised infrastructure belonging to three Taiwanese universities,” Recorded Future noted.
A successful initial access is followed by the deployment of the China Chopper web shell to maintain persistence, alongside other open-source web shells like devilzShell, AntSword, and Godzilla. A few instances have also entailed the exploitation of a Linux privilege escalation vulnerability known as DirtyCow (CVE-2016-5195).

“RedJuliett is likely interested in collecting intelligence on Taiwan’s economic policy and trade and diplomatic relations with other countries,” it said.
“RedJuliett, like many other Chinese threat actors, is likely targeting vulnerabilities in internet-facing devices because these devices have limited visibility and security solutions available, and targeting them has proven to be an effective way to scale initial access.”