New Medusa malware variants target Android users in seven countries
by nlqip

The Medusa banking trojan for Android has re-emerged after almost a year of keeping a lower profile in campaigns targeting France, Italy, the United States, Canada, Spain, the United Kingdom, and Turkey.
The new activity has been tracked since May and relies on more compact variants that require fewer permissions and come with fresh features in an attempt to initiate transactions directly from the compromised device
Also known as TangleBot, Medusa banking trojan is an Android malware-as-a-service (MaaS) operation discovered in 2020. The malware provides keylogging, screen controls, and SMS manipulation.
Although it has the same name, the operation is different from the ransomware gang and the Mirai-based botnet for distributed denial-of-service (DDoS) attacks.
The recent campaigns were discovered by the threat intelligence team at online fraud management company Cleafy, who says that the malware variants are lighter, need fewer persmissions on the device, and include full-screen overlaying and screenshot capturing.
Latest campaigns
The first evidence of the recent Medusa variants is from July 2023, the researchers say. Cleafy observed them in campaigns that rely on SMS phishing (‘smishing’) to side-load the malware through dropper applications.
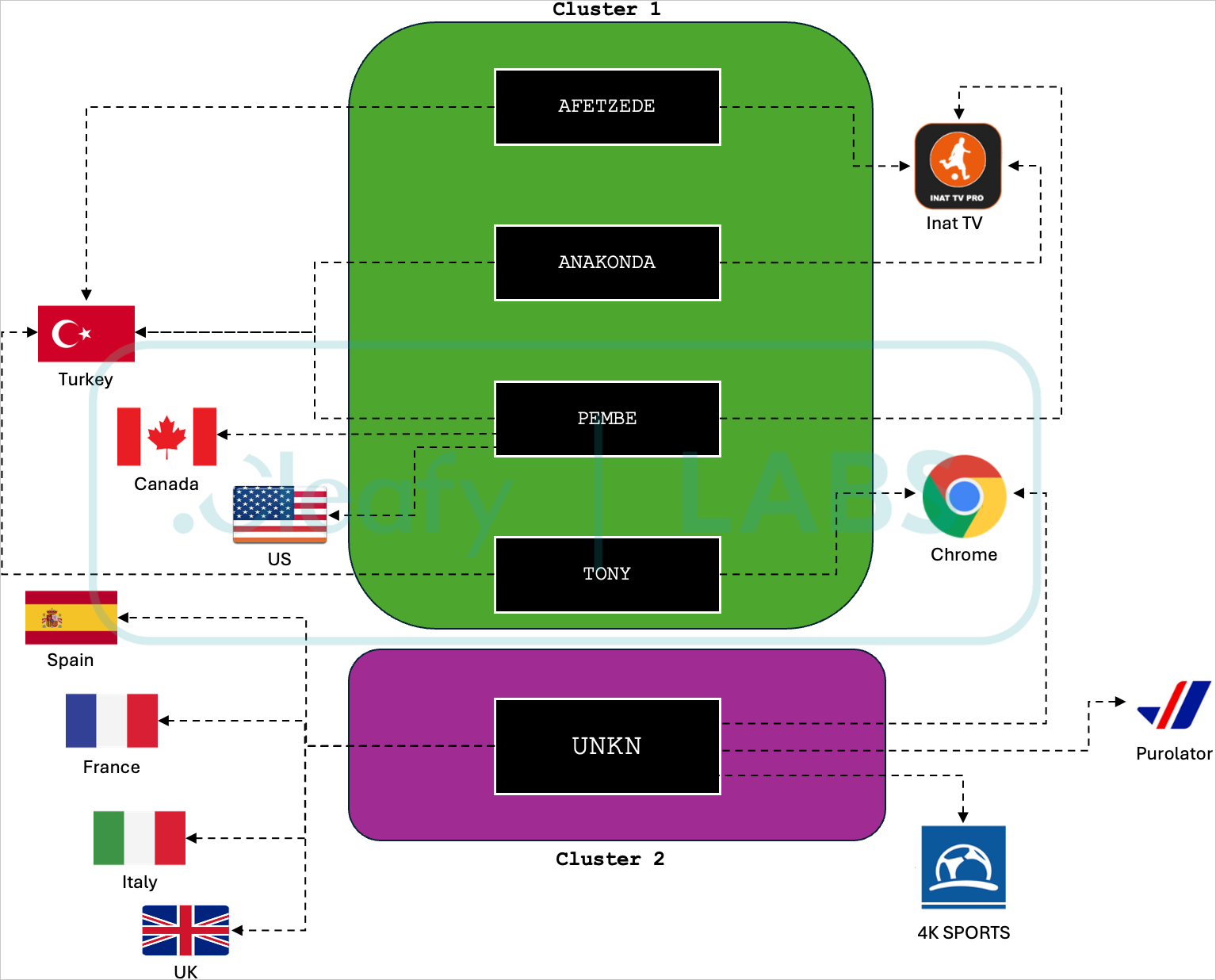
The researchers discovered 24 campaigns using the malware and attributed them to five separate botnets (UNKN, AFETZEDE, ANAKONDA, PEMBE, and TONY) that delivered malicious apps.
The UNKN botnet is operated by a distinct cluster of threat actors, which focus on targeting countries in Europe, particularly France, Italy, Spain, and the UK.
Source: Cleafy
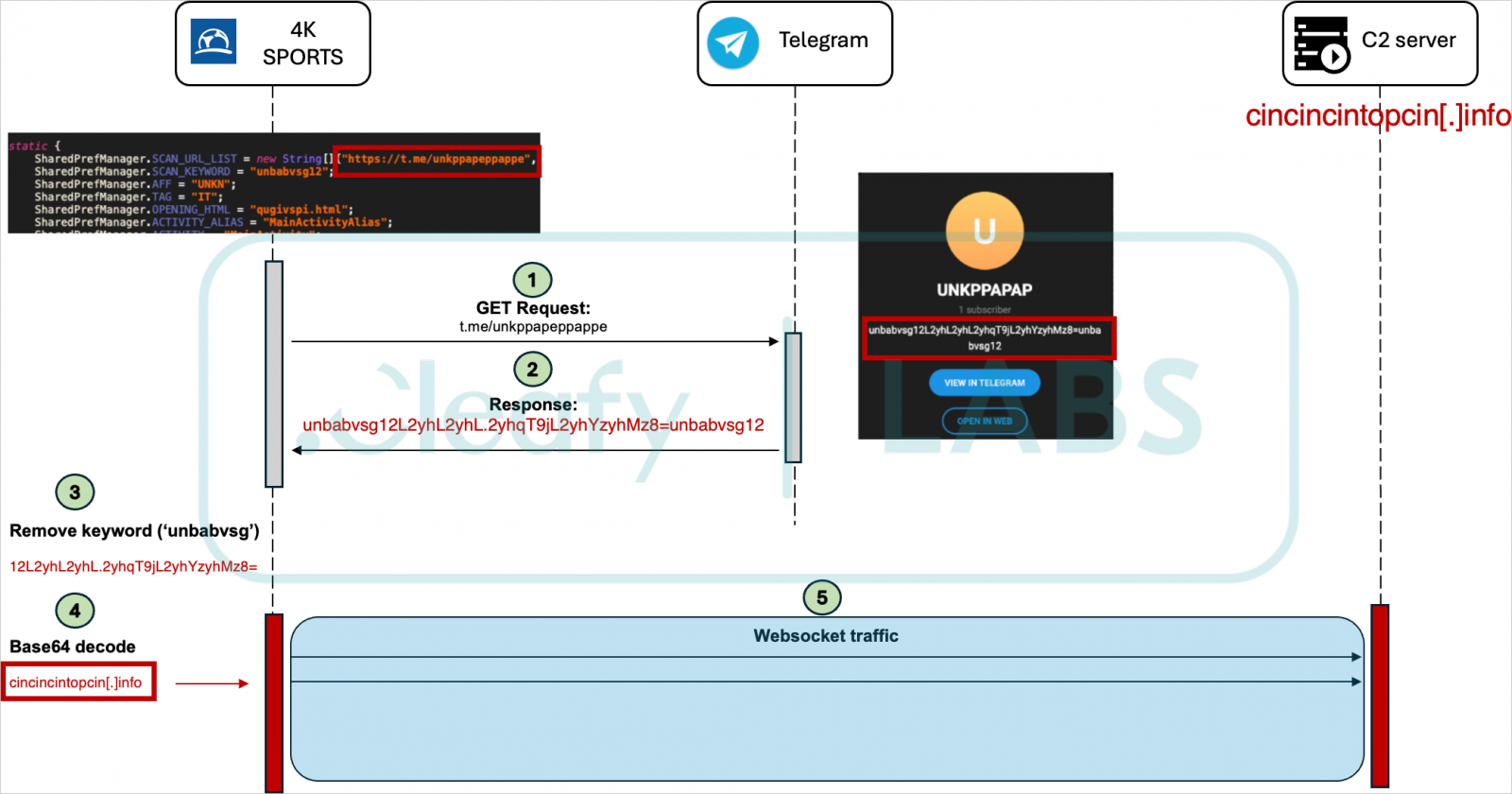
Recent dropper apps used in those attacks include a fake Chrome browser, a 5G connectivity app, and a fake streaming app called 4K Sports.
Given that the UEFA EURO 2024 champhionship is currently underway, the choice of the 4K Sports streaming app as a bait seems timely.
Cleafy comments that all campaigns and botnets are handled by Medusa’s central infrastructure, which dynamically fetches the URLs for the command and control (C2) server from public social media profiles.
Source: Cleafy
New Medusa variant
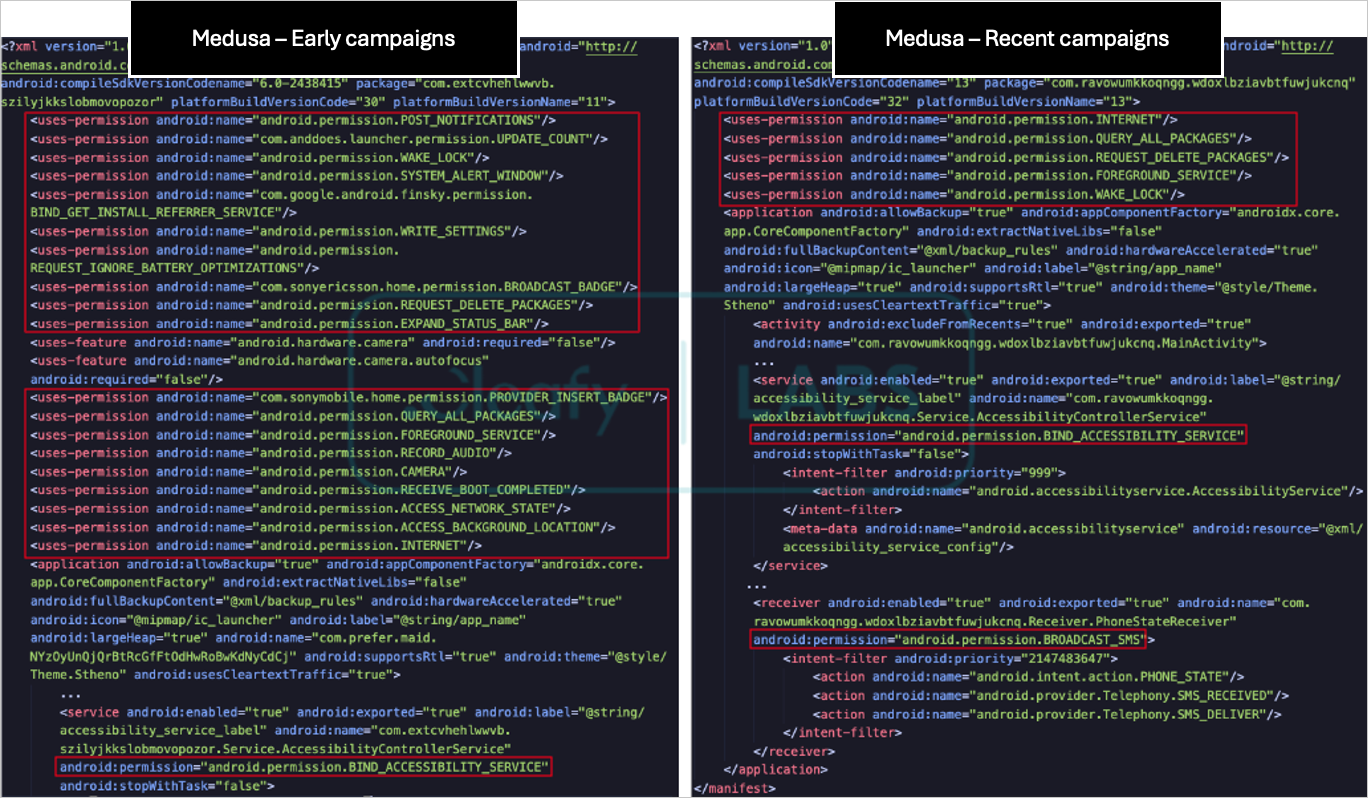
The authors of the Medusa malware have opted to reduce its footprint on compromised devices, now requesting only a small set of permissions but still require Android’s Accessibility Services.
Also, the malware retains its capability to access the victim’s contact list and send SMS, a key distribution method.
Source: Cleafy
Cleafy’s analysis shows that the malware authors removed 17 commands from the previous version of the malware and added five new ones:
- destroyo: uninstall a specific application
- permdrawover: request ‘Drawing Over’ permission
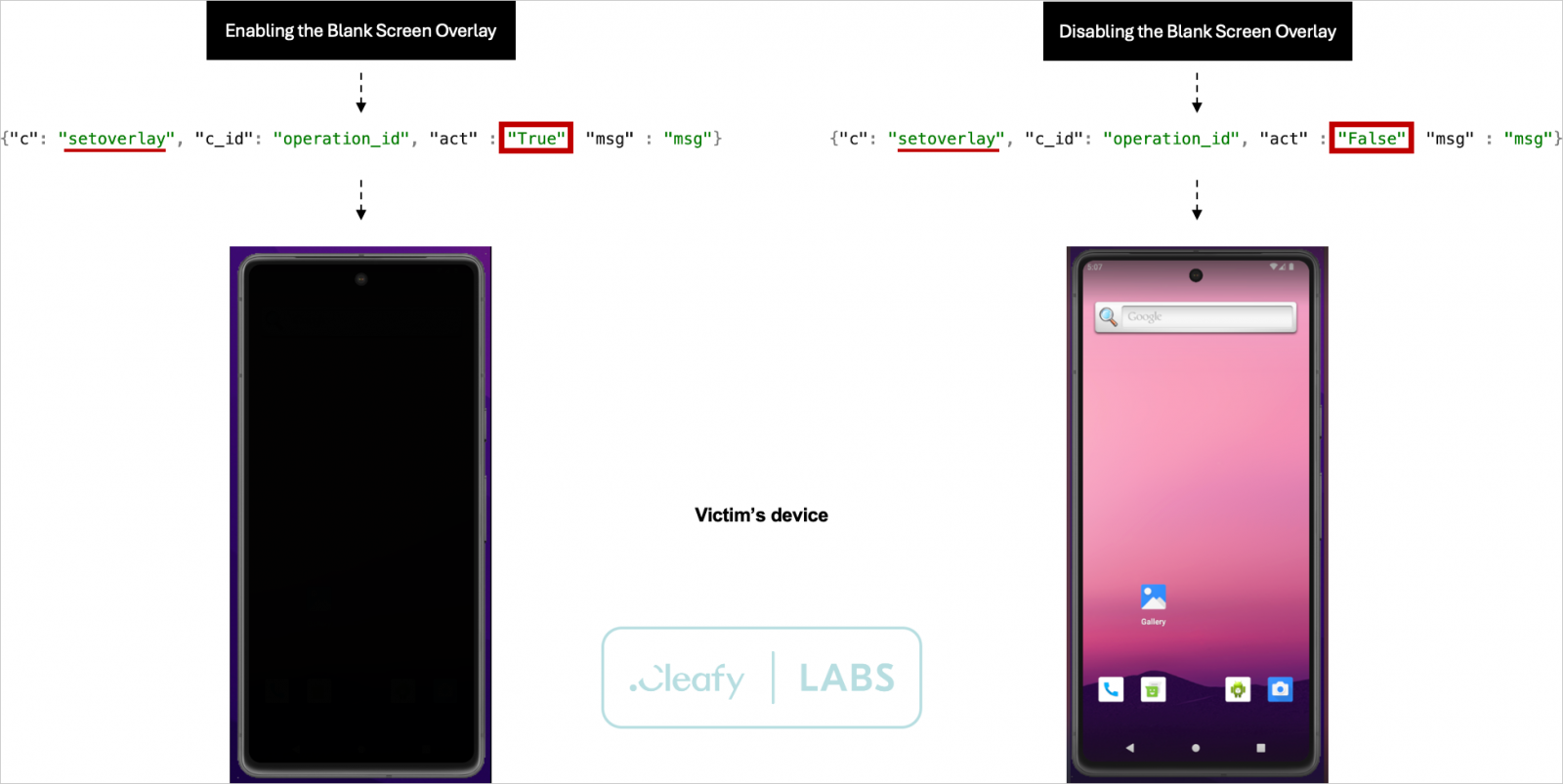
- setoverlay: set a black screen overlay
- take_scr: take a screenshot
- update_sec: update user secret
The ‘setoverlay’ command is noteworthy as it allows remote attackers to perform deceptive actions such as making the device appear locked/shut off to mask malicious ODF activities occurring in the background.
Source: Cleafy
The new capability to capture screenshots is also an important addition, giving threat actors a new way to steal sensitive information from infected devices.
Overall, the Medusa mobile banking trojan operation appears to expand its targeting scope and be getting stealthier, laying the ground for more massive deployment and higher number of victim counts.
Although Cleafy has not observed any of the dropper apps on Google Play yet, as the number of cybercriminals joining the MaaS increases, distribution strategies are bound to diversify and become more sophisticated.
Source link
lol
The Medusa banking trojan for Android has re-emerged after almost a year of keeping a lower profile in campaigns targeting France, Italy, the United States, Canada, Spain, the United Kingdom, and Turkey. The new activity has been tracked since May and relies on more compact variants that require fewer permissions and come with fresh features…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
