Cloudflare: We never authorized polyfill.io to use our name
by nlqip

Cloudflare, a lead provider of content delivery network (CDN) services, cloud security, and DDoS protection has warned that it has not authorized the use of its name or logo on the Polyfill.io website, which has recently been caught injecting malware on more than 100,000 websites in a significant supply chain attack.
Further, to keep the internet safe, Cloudflare is automatically replacing polyfill.io links with a safe mirror on websites that use Cloudflare protection (including free plans).
Cloudflare: ‘Yet another warning’ Polyfill can’t be trusted
Cloudflare has criticized Polyfill.io’s unauthorized usage of its name and logo as it could mislead users into believing that the illicit website is endorsed by Cloudflare.
The cloud security leader further warned that this is yet another reason not to trust Polyfill.io.
“Contrary to what is stated on the polyfill.io website, Cloudflare has never recommended the polyfill.io service or authorized their use of Cloudflare’s name on their website,” the Cloudflare team wrote in a blog post published yesterday.
“We have asked them to remove the false statement and they have, so far, ignored our requests. This is yet another warning sign that they cannot be trusted.”
The caution follows the discovery of the Polyfill.io supply chain attack that hit more than 100,000 websites.
In February, a Chinese entity named ‘Funnull’ bought the polyfill.io domain and introduced malicious code in the scripts delivered by its CDN.
As discovered by Sansec researchers, the domain began injecting malware on mobile devices that would visit a website embedding code from cdn.polyfill[.]io.
Yesterday, BleepingComputer observed that the DNS entries for cdn.polyfill[.]io were mysteriously set to Cloudflare’s servers, but that is not a definitive sign of the attack being contained as the (new) domain owners could easily switch back DNS to malicious servers.
Moreover, it’s entirely possible that Polyfill.io’s owners were—like any other website, using Cloudflare’s DDoS protection services, but that does not imply Cloudflare’s endorsement of the domain.
BleepingComputer had earlier contacted Cloudflare to see if they were involved in the change of DNS records but did not hear back. As of today, polyfill.io is no longer online.
Automatic URL replacement offered for free
Over the last 24 hours, Cloudflare has released an automatic URL rewriting service to replace any polyfill.io links on the websites of Cloudflare customers with a safe mirror CDN setup by Cloudflare.
“We have, over the last 24 hours, released an automatic JavaScript URL rewriting service that will rewrite any link to polyfill.io found in a website proxied by Cloudflare to a link to our mirror under cdnjs,” announced the Cloudflare team in the same blog post.
“This will avoid breaking site functionality while mitigating the risk of a supply chain attack.”
“Any website on the free plan has this feature automatically activated now. Websites on any paid plan can turn on this feature with a single click.”
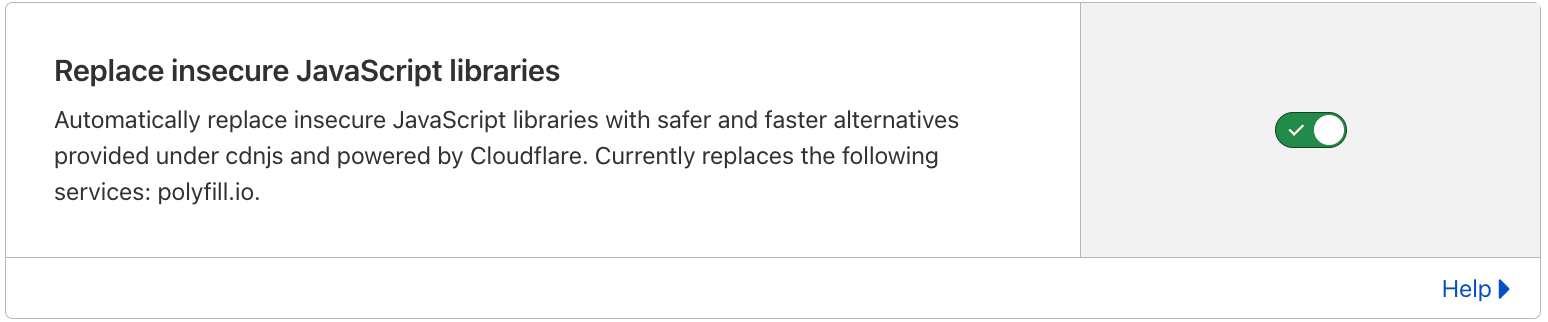
Cloudflare users can find this new setting under Security ⇒ Settings on any zone using Cloudflare.
For those not using Cloudflare, the company still suggests removing any uses of polyfill.io and identifying an alternative solution.
“While the automatic replacement function will handle most cases, the best practice is to remove polyfill.io from your projects and replace it with a secure alternative mirror like Cloudflare’s even if you are a customer,” states the company.
“You can do this by searching your code repositories for instances of polyfill.io and replacing it with cdnjs.cloudflare.com/polyfill/ (Cloudflare’s mirror). This is a non-breaking change as the two URLs will serve the same polyfill content. All website owners, regardless of the website using Cloudflare, should do this now.”
Another cybersecurity firm Leak Signal has also created a website, Polykill.io that lets you search for sites using cdn.polyfill.io and provides information on switching to alternatives.
Source link
lol
Cloudflare, a lead provider of content delivery network (CDN) services, cloud security, and DDoS protection has warned that it has not authorized the use of its name or logo on the Polyfill.io website, which has recently been caught injecting malware on more than 100,000 websites in a significant supply chain attack. Further, to keep the internet safe,…
Recent Posts
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
