Polyfill.io, BootCDN, Bootcss, Staticfile attack traced to 1 operator
by nlqip

The recent large scale supply chain attack conducted via multiple CDNs, namely Polyfill.io, BootCDN, Bootcss, and Staticfile that affected anywhere from 100,000 to tens of millions of websites has been traced to a common operator, according to researchers.
Researchers discovered a public GitHub repository where the purported operators of Polyfill.io had accidentally exposed their Cloudflare secret keys.
By using these leaked API keys, which were still active, researchers were able to establish that a common operator was behind all four domains, and the wider supply chain attack.
Accidental exposure of Cloudflare keys
Security researchers and open source intel (OSINT) enthusiasts discovered a GitHub repository associated with the polyfill.io domain which was involved in a large scale supply chain attack that has now believed to have impacted tens of millions of websites.
The secrets leaked in the repository enabled researchers to attribute the supply chain attack involving all 4 CDN services, namely, Polyfill.io, BootCDN, Bootcss, and Staticfile, to a single entity.
The discovery was made as a result of the collaborative effort between researcher Ze-Zheng Wu, a pseudonymous user mdmck10, and the security research group, MalwareHunterTeam.
Ze-Zheng Wu, a developer and a PhD candidate based in Hangzhou, China, discovered a GitHub repository titled, “data.polyfill.com” that appeared to contain the backend source code of Polyfill.io and its relaunched version Polyfill.com.
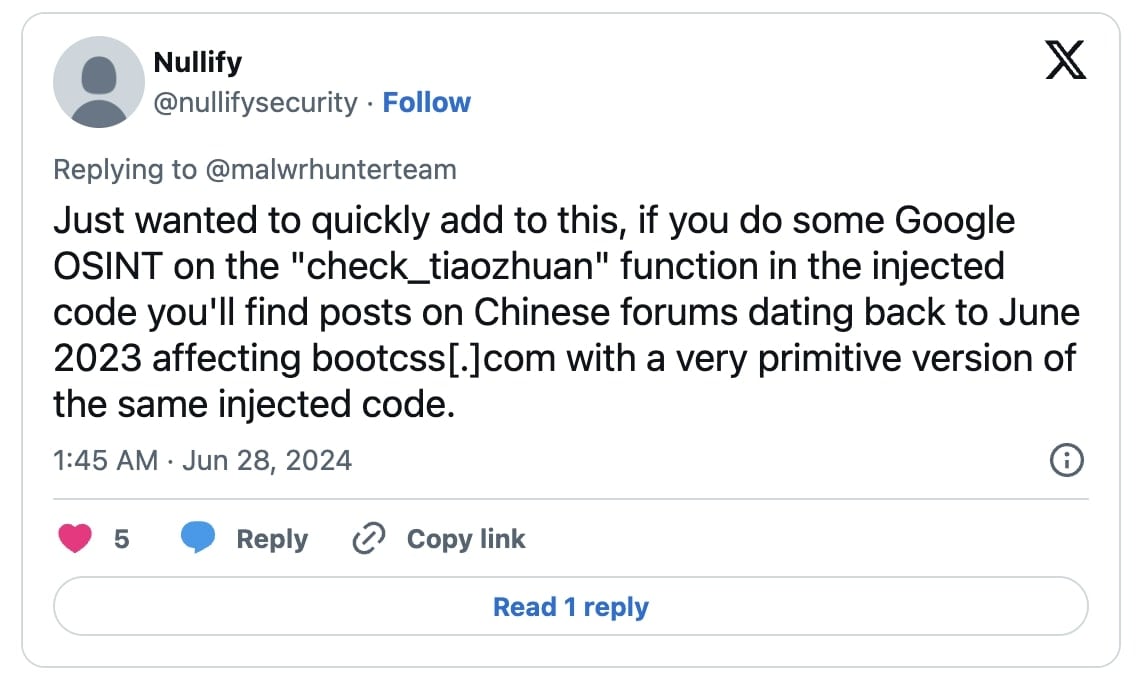
The researcher observed that that the repo owner had accidentally uploaded an .env file to the public repostiory:
Dot env (.env) files are used by developers and sysadmins to store secrets such as API keys and tokens, environment variables, and configuration settings. As such, these files should be secured with restrictive permissions and be heavily guarded from the public.
The exposed file, as also seen by BleepingComputer, contains a Cloudflare API token, Cloudflare Zone ID (of the Polyfill.io domain), Algolia API keys, among other values.
BleepingComputer also observed that earlier versions of the file had “production” MySQL credentials present.
The Cloudflare API key allowed researchers, in particular mdmck10 to query and obtain a list of active zones associated with the particular Cloudflare account.
A Cloudflare “zone” is a way for a website administrators to organize and manage domains in their Cloudflare account, and distinct settings for each domain.
Roughly speaking, each Cloudflare “zone” comprises a domain name, its DNS settings, dates of creation or modification of the zone, and metadata related to its owner.
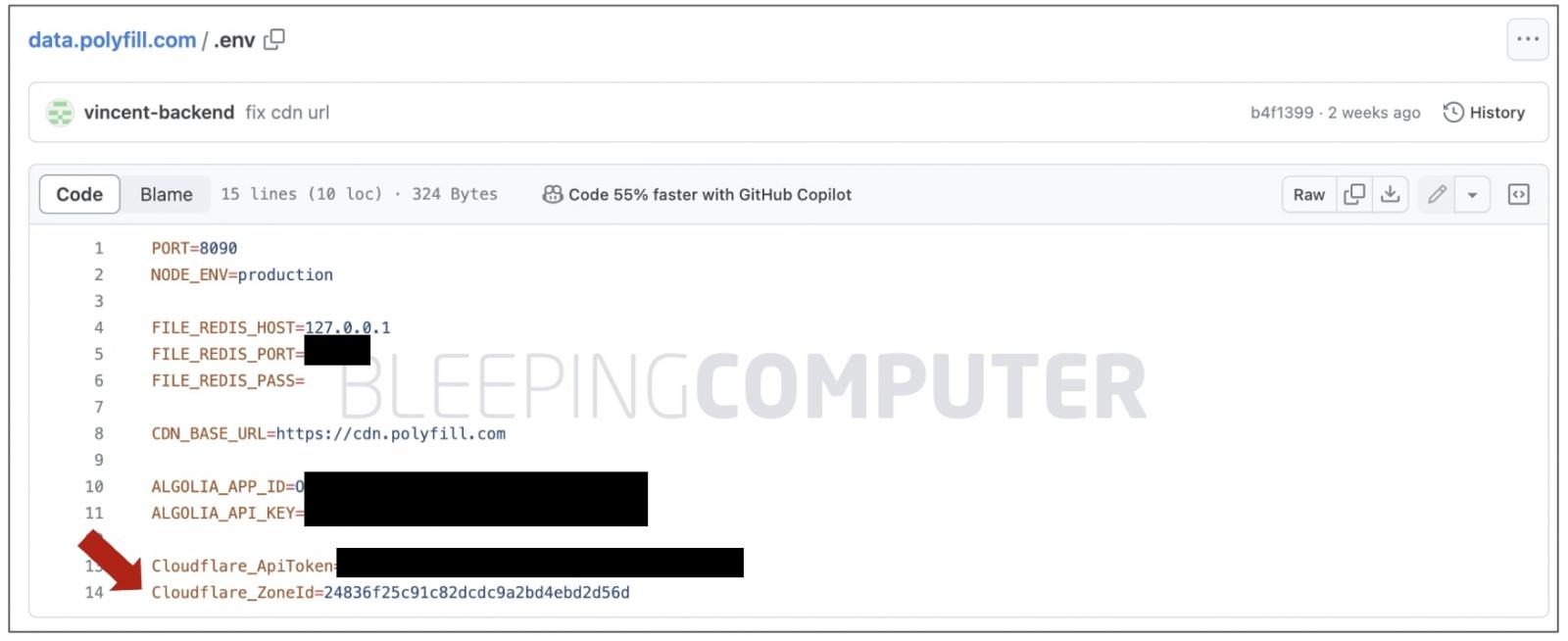
Among all domains (or zones) returned for the Cloudflare account, one was for cdn.polyfill.io. Notice how the zone “id” also matches the Zone ID listed in the .env file found on the GitHub repository above:
The 430-line JSON file, shared by mdmck10, additionally contained entries for domains, staticfile.net, bootcdn.net, bootcss.com, indicating that these were managed under the same Cloudflare user account, operated by a common entity.
While Cloudflare never authorized Polyfill.io to use its logo and name and never endorsed the service, on Wednesday, the DNS records for Polyfill.io were mysteriously switched to Cloudflare’s, indicating that Cloudflare’s service were at least partially in use by the domain owners.
We contacted Cloudflare at the time to understand if it was involved in the change in these DNS records, or in helping mitigate the attack, but did not hear back.

Wider attack likely ongoing since June 2023
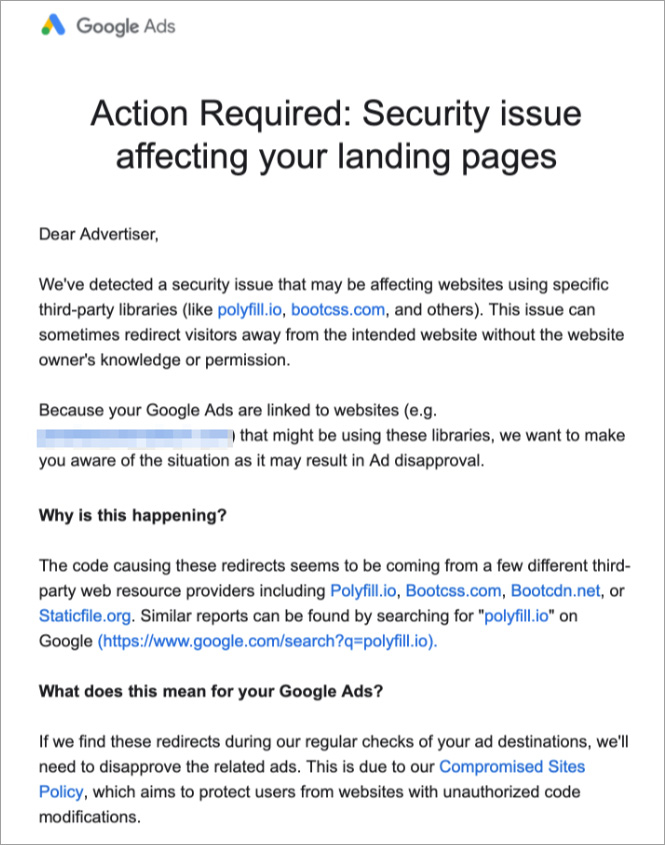
MalwareHunterTeam who has closely been monitoring the situation drew attention to the fact that Google’s warning to its advertisers regarding the supply chain attack was not limited to ad landing pages embedding polyfill.io, but three more services, Bootcss, BootCDN, and Staticfile.
“But somehow everyone skipped caring about that. Some of the first articles of the situation mentioned those domains in a way or another… and basically that’s it,” writes MalwareHunterTeam in a thread on X (formerly Twitter).
The security research group warned that the combined impact resulting from these other three services is likely to have a much wider impact than initially anticipated.
Just recently, Cloudflare’s co-founder and CEO, Matthew Prince stated that “tens of millions of websites (4% of the web)” used Polyfill.io, dubbing the incident “extremely concerning” as is.
Nullify, an Australia-based forensic investigator and security researcher has now made an even more worrisome observation.
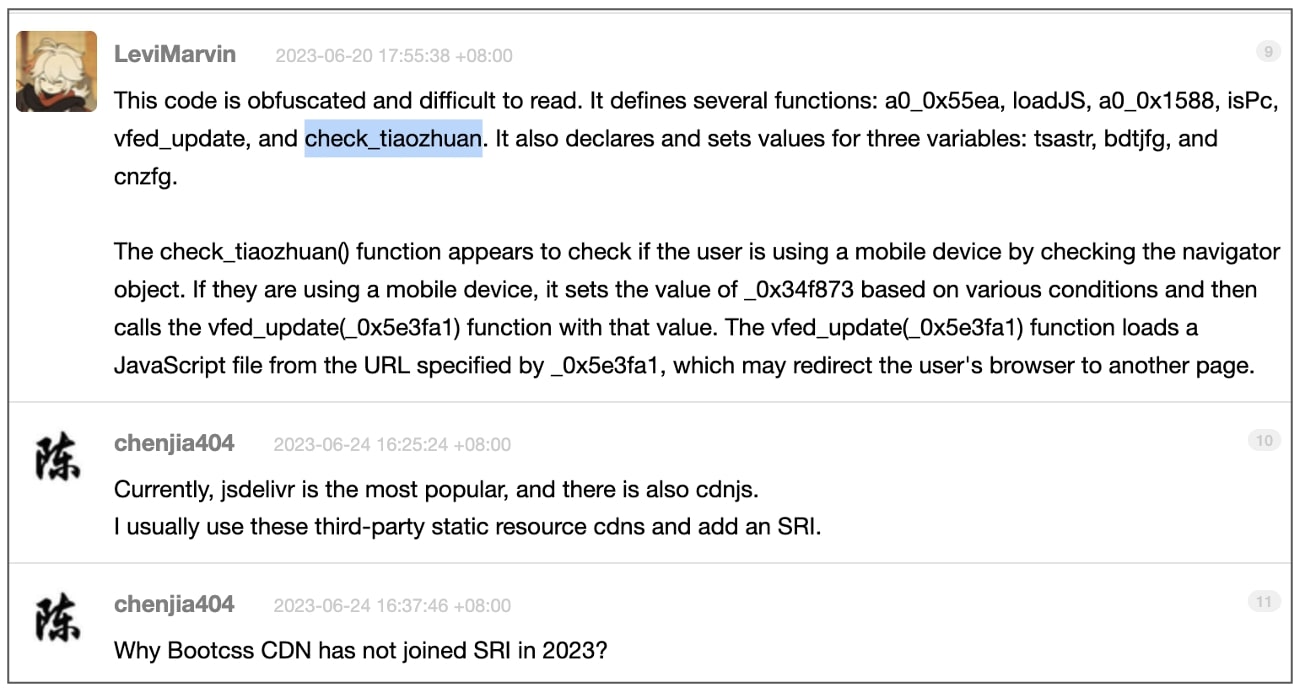
References to the ‘check_tiaozhuan’, a function that represents the injected malicious code exist on “Chinese forums dating back to June 2023.”
Since then, “a very primitive version of the same injected code” was in circulation via BootCSS, according to the researcher.
BleepingComputer has been able to independently confirm that multiple Chinese-language forum pages, dated as early as June 20th, 2023, have developers trying to decipher and comprehend the anomalous “obfuscated code” delivered by BootCSS.
The ‘check_tiaozhuan’ function, according to the developers, would survey if a visitor was running a mobile device and “redirect the user’s browser to another page”:
(BleepingComputer)
Sansec researchers who first raised alarms on the Polyfill.io attack, have updated their list of domains associated with the supply chain attack to include:
bootcdn.net
bootcss.com
staticfile.net
staticfile.org
unionadjs.com
xhsbpza.com
union.macoms.la
newcrbpc.com
“Whack-a-mole” situation: full impact yet to be assessed
Although the attack seems to have been contained for now, its wider impact will likely unfold in the upcoming weeks and its scope is yet to be fully grasped.
Shortly after Polyfill.io was shut down by Namecheap, it was relaunched on polyfill.com by its operators. As of this morning, polyfill.com is no longer responsive.
Threat intel analyst, Dominic Alvieri warns, however, that Polyfill.io operators could have potentially hoarded multiple domains in advance with different registrars, citing “polyfill.cloud” as one possible example. Active deployment of these domains could quickly turn this incident into a whack-a-mole situation.
Backup domains still registered with the current registrar include /polyfill[.]cloud
They’re going to keep going from one domain to the other.
The group still has the same registration on all of their known registered assets.@malwrhunterteam @1ZRR4H
— Dominic Alvieri (@AlvieriD) June 27, 2024
Detection ratios for domains associated with the attack remain low among leading antivirus engines and human forensic efforts may be necessary to audit your environments:
Detection ratios for the domains currently:
cdn.bootcdn[.]net
cdn.bootcss[.]com
cdn.staticfile[.]net
cdn.staticfile[.]org
Let’s see tomorrow… pic.twitter.com/m6EGEIyCwu— MalwareHunterTeam (@malwrhunterteam) June 27, 2024
Incident response handlers and SOC defender teams may benefit from searching their SIEM logs for network events that represent connections to the CDN domains associated with the incident:
KQL to hunt in MDE
###############DeviceNetworkEvents
| where TimeGenerated > ago(30d)
| where RemoteUrl has_any(“polyfill[.]io’,’cdn.bootcdn[.]net”,”cdn.bootcss[.]com”,”cdn.staticfile[.]net”,”cdn.staticfile[.]org”)
| sort by Timestamp desc###############
re-fang to execute! https://t.co/bj674ZKQ3r
— mRr3b00t (@UK_Daniel_Card) June 28, 2024
If you haven’t already, consider replacing existing usage of any of these services with safe alternatives set up by Cloudflare and Fastly.
Polykill.io from cybersecurity firm, Leak Signal, is another handy service that lets you identify websites using Polyfill.io and make the switch.
BleepingComputer attempted to contact the Polyfill Global X account for comment prior to publishing but they have disabled DMs. With both Polyfill .io and .com domains now down, the admin’s email addresses are no longer operational. We additionally approached Funnull for comment but our email bounced back. We have now approached them via Telegram and await a response.
Source link
lol
The recent large scale supply chain attack conducted via multiple CDNs, namely Polyfill.io, BootCDN, Bootcss, and Staticfile that affected anywhere from 100,000 to tens of millions of websites has been traced to a common operator, according to researchers. Researchers discovered a public GitHub repository where the purported operators of Polyfill.io had accidentally exposed their Cloudflare secret keys.…
Recent Posts
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners