Month: June 2024
The FBI is warning of cybercriminals posing as law firms and lawyers that offer cryptocurrency recovery services to victims of investment scams and steal funds and personal information. The latest alert is an update to similar warning from the agency’s Internet Crime Complaint Center (IC3) that alerted of an increase in scams involving fake services for…
Read MoreHere’s a look at 10 data science and machine learning tools that solution and service providers should be aware of. Deep Thoughts Data science and machine learning technologies have long been important for data analytics tasks and predictive analytical software. But with the wave of artificial intelligence and generative AI development in 2023, the importance…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/the-role-of-cybersecurity-in-modern-construction-and-manufacturing” on this server. Reference #18.cad7ce17.1719322963.1e8b3450 https://errors.edgesuite.net/18.cad7ce17.1719322963.1e8b3450 Source link lol
Read MoreUnderstanding Customer Managed Encryption Keys (CMKs) in AWS, Azure and GCP: A Comparative Insight
by nlqip
Explore critical differences in handling customer-managed encryption keys (CMKs) across AWS, Azure, and GCP to avoid security misconfigurations and protect your data effectively. Why are we here? A customer-managed encryption key (CMK) is an encryption key created, managed, and owned by the customer. This gives the customer control over its access management—that is, determining who…
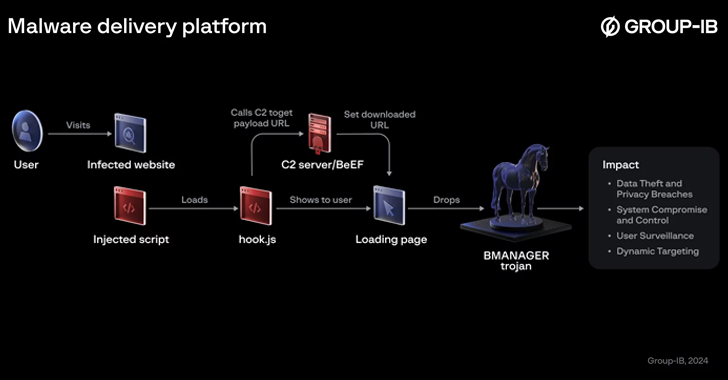
Read MoreJun 25, 2024NewsroomData Theft / Web Security A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER. “The threat actor behind this campaign has been carrying out opportunistic SQL injection attacks against websites in various countries since at least 2022,” Group-IB researchers Rustam…
Read MoreBiggest hack, if confirmed If confirmed, the Federal Reserve breach would turn into one of the biggest banking hacks in US history. Being the central banking system of the country, the Federal Reserve operates twelve banking districts, home to major cities like Boston, New York, Dallas, Chicago, and San Francisco. Although the Federal Reserve is…
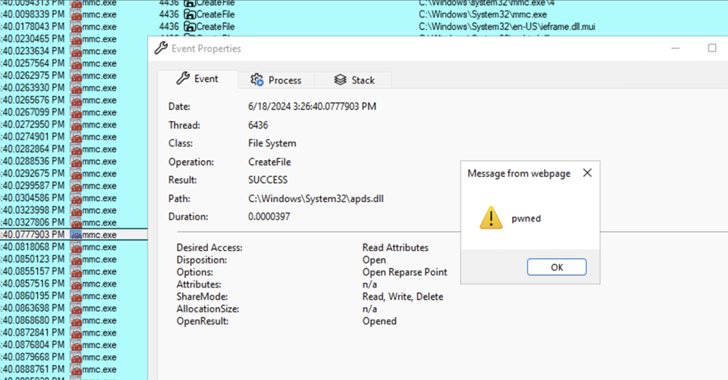
Read MoreJun 25, 2024NewsroomVulnerability / Threat Detection Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management Console (MMC) and evade security defenses. Elastic Security Labs has codenamed the approach GrimResource after identifying an artifact (“sccm-updater.msc“) that was…
Read MoreBreaking the M-209 Interesting paper about a German cryptanalysis machine that helped break the US M-209 mechanical ciphering machine. The paper contains a good description of how the M-209 works. Tags: academic papers, cryptanalysis, cryptography, history of cryptography Posted on June 25, 2024 at 7:02 AM • 0 Comments Sidebar photo of Bruce Schneier by…
Read MoreJun 25, 2024The Hacker NewsBrowser Security / Endpoint Security Browser security is becoming increasingly popular, as organizations understand the need to protect at the point of risk – the browser. Network and endpoint solutions are limited in their ability to protect from web-borne threats like phishing websites or malicious browser extensions. They also do not…
Read MoreP2PInfect, originally a dormant peer-to-peer malware botnet with unclear motives, has finally come alive to deploy a ransomware module and a cryptominer in attacks on Redis servers. According to Cado Security, which has been tracking P2PInfect for some time now, there is evidence the malware operates as a “botnet for hire,” although conflicting information prevents…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA