Month: June 2024
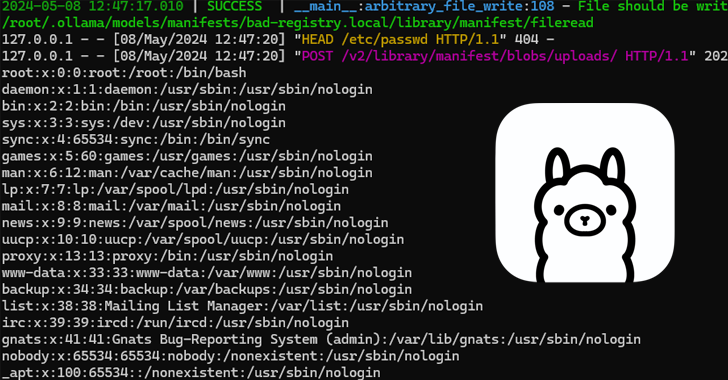
Jun 24, 2024NewsroomArtificial Intelligence / Cloud Security Cybersecurity researchers have detailed a now-patch security flaw affecting the Ollama open-source artificial intelligence (AI) infrastructure platform that could be exploited to achieve remote code execution. Tracked as CVE-2024-37032, the vulnerability has been codenamed Probllama by cloud security firm Wiz. Following responsible disclosure on May 5, 2024, the…
Read MoreFrom Amazon Q Business and AI Agents to new cloud storage and Amazon Bedrock tools, here are the 10 coolest new AWS products launched in 2024 so far. From its new Amazon Q Developer and Business products to new cloud storage and Amazon Bedrock offerings, Amazon Web Services’ product innovation engine has been on fire…
Read MoreOrganized Cybercrime Groups There are different categories of cybercriminals that can come together to form organized cybercrime groups. These include bored teenagers getting involved in petty online crimes, individual actors primarily motivated by financial gain, politically or ideologically motivated hackers, and fully fledged organized crime syndicates. However, the most sophisticated and damaging cybercrime operations tend…
Read MoreCar dealerships across North America are facing ongoing disruptions as software provider CDK Global grapples with the aftermath of a cyberattack Wednesday. The company began restoring its systems Sunday, but the process is expected to take “several days,” reported Bloomberg citing a company statement. “We are continuing to actively engage with our customers and provide…
Read MoreJun 24, 2024The Hacker NewsThreat Intelligence / Cybersecurity Learn about critical threats that can impact your organization and the bad actors behind them from Cybersixgill’s threat experts. Each story shines a light on underground activities, the threat actors involved, and why you should care, along with what you can do to mitigate risk. Cybersecurity professionals…
Read MoreHowever, over time, the malware has been used for evolved campaigns such as requesting permissions for notifications, device admin rights, or even stealthily seeking minimal sensitive permissions such as SMS, Call Logs, and Contacts. The malware, as observed till now, configures a C2 (command and control) panel which allows a set of invasive operations including…
Read MorePaul Nakasone Joins OpenAI’s Board of Directors Former NSA Director Paul Nakasone has joined the board of OpenAI. Tags: artificial intelligence, NSA Posted on June 24, 2024 at 7:04 AM • 1 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/business-email-compromise-bec-tracking-a-threat-actors-funny-business” on this server. Reference #18.c6d7ce17.1719223471.fcf0449 https://errors.edgesuite.net/18.c6d7ce17.1719223471.fcf0449 Source link lol
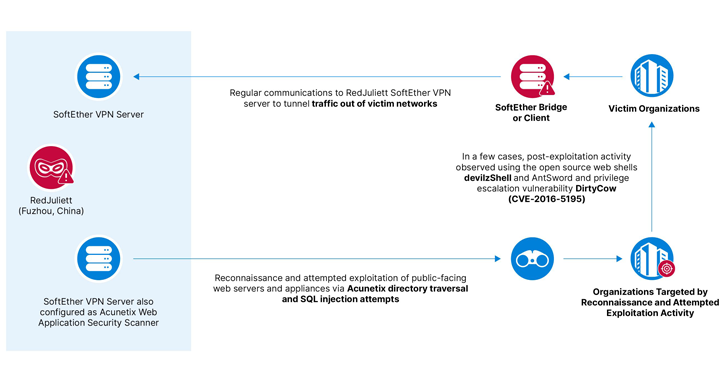
Read MoreJun 24, 2024NewsroomCyber Espionage / Hacking A likely China-linked state-sponsored threat actor has been linked to a cyber espionage campaign targeting government, academic, technology, and diplomatic organizations in Taiwan between November 2023 and April 2024. Recorded Future’s Insikt Group is tracking the activity under the name RedJuliett, describing it as a cluster that operates Fuzhou,…
Read MoreHow can the 76% (including Labbé) fill the gaps in their business knowledge? And how can the remaining 24% of CISOs — those who came into the role from non-tech backgrounds such as the military, law enforcement, compliance, or risk management — fill key gaps in their technical knowledge? Upskilling isn’t just for cyber workers,…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA