Month: June 2024
Image: Midjourney UnitedHealth has confirmed for the first time what types of medical and patient data were stolen in the massive Change Healthcare ransomware attack, stating that data breach notifications will be mailed in July. On Thursday, the company published a data breach notification warning that the ransomware attack exposed a “substantial quantity of data”…
Read MoreFor the week ending June 21, CRN takes a look at the companies that brought their ‘A’ game to the channel including Nvidia, Hewlett Packard Enterprise, Huntress, Digital Ocean and Riverbed. The Week Ending June 21 Topping this week’s Came to Win is Nvidia which – for a short time, at least – became the…
Read MoreCISA Releases Guidance on Single Sign-On (SSO) Adoption for Small and Medium-Sized Businesses: (SMBs) | CISA
by nlqip
Today, CISA released Barriers to Single Sign-On (SSO) Adoption for Small and Medium-Sized Businesses: Identifying Challenges and Opportunities, a detailed report exploring challenges to SSO adoption by small and medium-sized businesses (SMBs). The report also identifies potential ways to overcome these challenges and improve an SMB’s level of security. CISA also released a related blog…
Read MoreJuniper Networks released a security bulletin to address multiple vulnerabilities affecting Juniper Secure Analytics optional applications. A cyber threat actor could exploit one of these vulnerabilities to take control of an affected system. Users and administrators are encouraged to review the following and apply the necessary updates: Source link lol
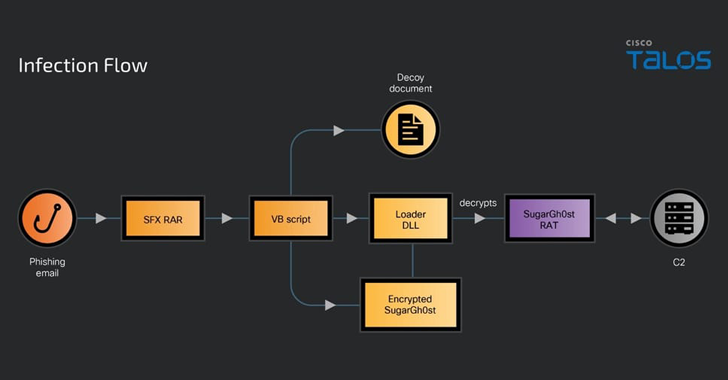
Read MoreJun 21, 2024NewsroomMalware / Threat Intelligence A previously undocumented Chinese-speaking threat actor codenamed SneakyChef has been linked to an espionage campaign primarily targeting government entities across Asia and EMEA (Europe, Middle East, and Africa) with SugarGh0st malware since at least August 2023. “SneakyChef uses lures that are scanned documents of government agencies, most of which…
Read MoreThe Tor Project has released Tor Browser 13.5, bringing several improvements and enhancements for Android and desktop versions. The Tor Browser is a specialized open-source web browser designed for anonymous browsing by routing the user’s traffic through thousands of volunteer-run servers called nodes/relays, which constitute the Tor network. Tor also provides access to “.onion” websites, which…
Read MoreGenAI has remained a top focus for cybersecurity vendors recently during the first half of the year, but plenty of other new products—including in SIEM, SASE and XDR—have debuted during the first half of the year. The list of cybersecurity tools utilizing generative AI continued to balloon during the first half of the year, including…
Read MoreJun 21, 2024NewsroomPhishing Attack / Email Security Cybersecurity researchers have shed light on a new phishing campaign that has been identified as targeting people in Pakistan using a custom backdoor. Dubbed PHANTOM#SPIKE by Securonix, the unknown threat actors behind the activity have leveraged military-related phishing documents to activate the infection sequence. “While there are many…
Read MoreACMA’s proceedings against Optus On 20 May 2024, ACMA filed proceedings in the Federal Court against Optus alleging that during the data breach between 17 to 20 September 2022, Optus failed to protect the confidentiality of its customers’ personal information from unauthorised interference or unauthorised access as required under the Telecommunications (Interception and Access) Act 1979. The…
Read MoreSlalom’s Chris Thomas explains the growing artificial intelligence use cases for its AI-powered robotic dog named Spot. The use cases for Slalom’s AI-powered robotic dog, Spot, are growing at a rapid pace thanks to Google’s Gemini AI and edge computing innovation. At Google Cloud Next 2024, Spot could be seen walking around and in between…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict