Month: June 2024
Generative AI (GenAI) is being hailed as the most transformative innovation since the rise of the internet in the 1990s. For security, GenAI can revolutionize the field if applied correctly, especially when it comes to threat detection and response. It enhances efficiency and productivity by swiftly processing and delivering critical information when it matters most.…
Read MoreJun 17, 2024NewsroomCyber Espionage / Vulnerability A suspected China-nexus cyber espionage actor has been attributed as behind a prolonged attack against an unnamed organization located in East Asia for a period of about three years, with the adversary establishing persistence using legacy F5 BIG-IP appliances and using it as an internal command-and-control (C&C) for defense…
Read MoreTraditional application security practices are not effective in the modern DevOps world. When security scans are run only at the end of the software delivery lifecycle (either right before or after a service is deployed), the ensuing process of compiling and fixing vulnerabilities creates massive overhead for developers. The overhead that degrades velocity and puts…
Read MoreThe UPX-packed ELF, apart from DSOP.pdf, has the DISGOMOJI malware payload which, upon execution, reads and exfiltrates system information including IP address, username, hostname, operating system, and the current working directory. Apart from the main functions, DISGOMOJI also downloads a shell script uevent_seqnum.sh, to check for connected USB devices and copy the content of those…
Read MoreUsing LLMs to Exploit Vulnerabilities Interesting research: “Teams of LLM Agents can Exploit Zero-Day Vulnerabilities.” Abstract: LLM agents have become increasingly sophisticated, especially in the realm of cybersecurity. Researchers have shown that LLM agents can exploit real-world vulnerabilities when given a description of the vulnerability and toy capture-the-flag problems. However, these agents still perform poorly…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Summer is a time for relaxation, travel, and spending quality moments with family and friends. However, it is also peak season for cybercriminals…
Read MoreWest Burton Energy Leverages Tenable OT Security To Improve Security, Safety and Efficiency
by nlqip
Tenable®, the Exposure Management company, today announced West Burton Energy is using Tenable OT Security to deliver operational technology (OT) asset visibility, OT vulnerability management, and threat detection – use cases that have proven challenging for so many companies in the power industry. This has enabled West Burton Energy to reduce threat-detection alerts by 98% and improve…
Read MoreOn the morning of August 30, 2023, a fire broke out at a data center operated by Belgian telecom giant Proximus. Soon, emergency numbers 112, 101, and 100, which are used to call the ambulance, the firefighters, and the police, became unreachable. The situation lasted for almost half an hour before these essential services were…
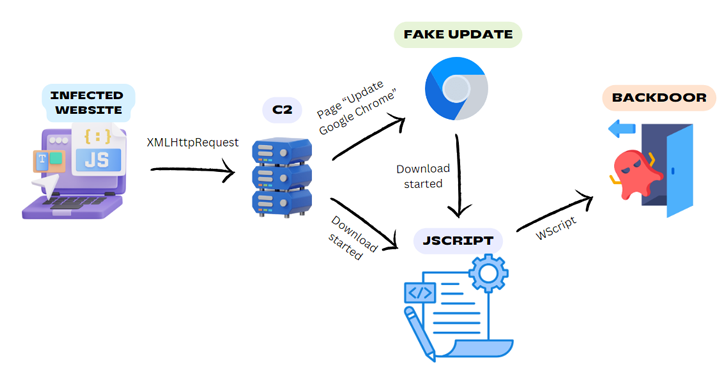
Read MoreJun 17, 2024NewsroomWeb Security / Malware Legitimate-but-compromised websites are being used as a conduit to deliver a Windows backdoor dubbed BadSpace under the guise of fake browser updates. “The threat actor employs a multi-stage attack chain involving an infected website, a command-and-control (C2) server, in some cases a fake browser update, and a JScript downloader…
Read MorePerhaps the best way to understand the approach is with an analogy about childhood learning. When we tell toddlers about numbers, they have no idea about how they drive complex human activities (statistical analysis, for instance). Instead, numbers are words learned perhaps by memorizing a song that uses them ( “One, Two, Buckle My Shoe”).…
Read MoreRecent Posts
- Red Hat Updates Present ‘Huge’ Partner Opportunities in OpenShift, Edge
- US govt officials’ communications compromised in recent telecom hack
- Microsoft patches Windows zero-day exploited in attacks on Ukraine
- Leaked info of 122 million linked to B2B data aggregator breach
- Dell NativeEdge Platform Brings AI To Edge Operations