Month: June 2024
Demo of AES GCM Misuse Problems This is really neat demo of the security problems arising from reusing nonces with a symmetric cipher in GCM mode. Tags: AES, algorithms, cryptanalysis, encryption Posted on June 14, 2024 at 7:05 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreJun 14, 2024NewsroomDevice Security / Authentication An analysis of a hybrid biometric access system from Chinese manufacturer ZKTeco has uncovered two dozen security flaws that could be used by attackers to defeat authentication, steal biometric data, and even deploy malicious backdoors. “By adding random user data to the database or using a fake QR code,…
Read MoreThreat actors linked to North Korea have accounted for one-third of all the phishing activity targeting Brazil since 2020, as the country’s emergence as an influential power has drawn the attention of cyber espionage groups. “North Korean government-backed actors have targeted the Brazilian government and Brazil’s aerospace, technology, and financial services sectors,” Google’s Mandiant and…
Read MoreESET researchers have identified five campaigns targeting Android users with trojanized apps. Most probably carried out by the Arid Viper APT group, these campaigns started in 2022 and three of them are still ongoing at the time of the publication of this blogpost. They deploy multistage Android spyware, which we named AridSpy, that downloads first-…
Read MoreDeepfakes as credit risks It’s not just cybersecurity experts who are warning of the corporate risk from deepfakes. In May, credit ratings firm Moody’s issued a warning about deepfakes, saying they create new credit risks. The Moody’s report details a handful of attempted deepfake scams, including faked video calls, that have targeted the financial sector…
Read MoreDoesn’t Tor enable criminals to do bad things? Tor’s mission is to advance human rights with free and open-source technology, empowering users to defend against mass surveillance and internet censorship. We hate that there are some people who use Tor for nefarious purposes, and we condemn the misuse and exploitation of our technology for criminal…
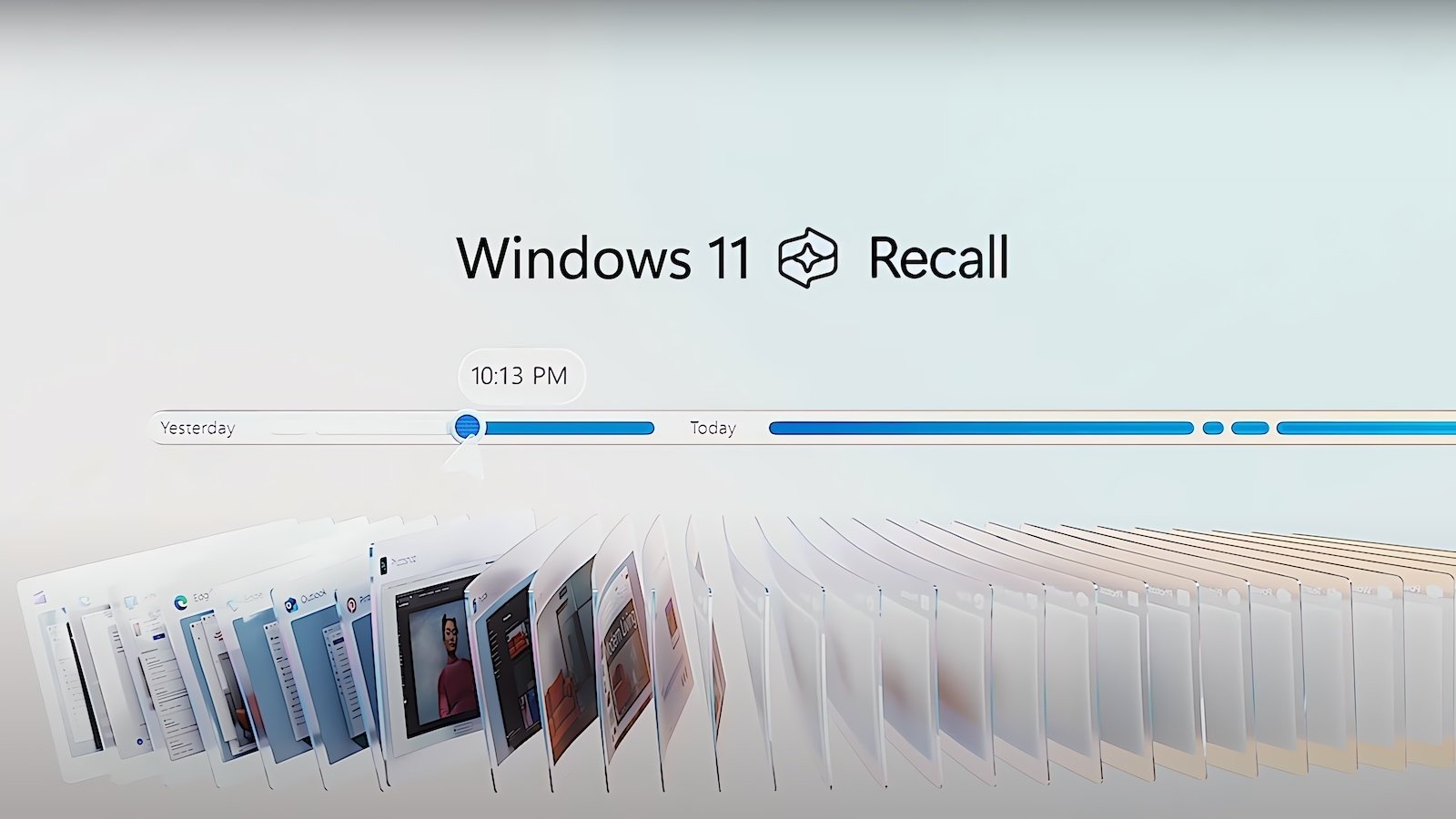
Read MoreJun 14, 2024NewsroomArtificial Intelligence / Data Protection Microsoft on Thursday revealed that it’s delaying the rollout of the controversial artificial intelligence (AI)-powered Recall feature for Copilot+ PCs. To that end, the company said it intends to shift from general availability preview available first in the Windows Insider Program (WIP) in the coming weeks. “We are…
Read MoreMicrosoft is delaying the release of its AI-powered Windows Recall feature to test and secure it further before releasing it in a public preview on Copilot+ PCs. Initially slated for release in a public preview on June 18 with the arrival of the new Copilot+ AI PCs, the company now says they are delaying its release by…
Read More‘There’s so much opportunity, and my challenge is when I close my eyes, I can see it. I can see it end to end. Not just today, not just next month, but three years out, five years out. I see it. I just can’t build it that fast,’ says Pax8 CEO Scott Chasin. At its…
Read MoreLeading U.S. commercial bank Truist confirmed its systems were breached in an October 2023 cyberattack after a threat actor posted some of the company’s data for sale on a hacking forum. Headquartered in Charlotte, North Carolina, Truist Bank was formed after SunTrust Banks and BB&T (Branch Banking and Trust Company) merged in December 2019. Now…
Read More