Month: June 2024
Fortinet has released security updates to address a vulnerability in FortiOS. A cyber threat actor could exploit this vulnerability to take control of an affected system. Users and administrators are encouraged to review the following Fortinet Security Bulletin and apply the necessary updates: Source link lol
Read More‘If I give you a paragraph of text and I convert it to embeddings that then get stored, the size of the embeddings is much bigger than the size of the original text,’ Manuvir Das, vice president of enterprise computing at Nvidia, tells CRN. ‘It can be 10 times bigger. This is a massive data…
Read MoreAttackers are easily sidestepping endpoint detection and response (EDR) and extended detection and response (XDR) defenses, often catching enterprises unaware, according to a new study of cybersecurity threats. The study of global cyberthreats, by EDR/XDR vendor Trellix, highlighted the danger posed by the emergence of “EDR killer tools” and their use to deliver ransomware or…
Read MoreLLMs Acting Deceptively New research: “Deception abilities emerged in large language models“: Abstract: Large language models (LLMs) are currently at the forefront of intertwining AI systems with human communication and everyday life. Thus, aligning them with human values is of great importance. However, given the steady increase in reasoning abilities, future LLMs are under suspicion…
Read MoreJun 11, 2024NewsroomCloud Computing / Artificial Intelligence Apple has announced the launch of a “groundbreaking cloud intelligence system” called Private Cloud Compute (PCC) that’s designed for processing artificial intelligence (AI) tasks in a privacy-preserving manner in the cloud. The tech giant described PCC as the “most advanced security architecture ever deployed for cloud AI compute…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. From humble beginnings as a niche hobby relegated to small gaming cafes and basements, eSports has grown into a huge affair where gamers…
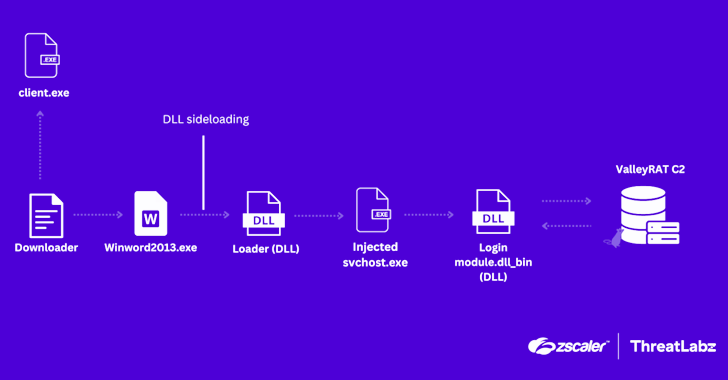
Read MoreJun 11, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have uncovered an updated version of malware called ValleyRAT that’s being distributed as part of a new campaign. “In the latest version, ValleyRAT introduced new commands, such as capturing screenshots, process filtering, forced shutdown, and clearing Windows event logs,” Zscaler ThreatLabz researchers Muhammed Irfan V A and…
Read MoreJun 11, 2024NewsroomMobile Security / Technology Arm is warning of a security vulnerability impacting Mali GPU Kernel Driver that it said has been actively exploited in the wild. Tracked as CVE-2024-4610, the use-after-free issue impacts the following products – “A local non-privileged user can make improper GPU memory processing operations to gain access to already…
Read MoreJun 11, 2024NewsroomData Theft / Cloud Security As many as 165 customers of Snowflake are said to have had their information potentially exposed as part of an ongoing campaign designed to facilitate data theft and extortion, indicating the operation has broader implications than previously thought. Google-owned Mandiant, which is assisting the cloud data warehousing platform…
Read MoreDigital Security The award is an excellent opportunity for us to thank our readers and to recognize the depth of talent of ESET’s security researchers and writers 10 Jun 2024 • , 2 min. read Drumroll, please! The winners of the 2024 European Cybersecurity Blogger Awards have been chosen, and we couldn’t be prouder –…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA