Router maker’s support portal hacked, replies with MetaMask phishing
by nlqip
BleepingComputer has verified that the helpdesk portal of a router maker is currently sending MetaMask phishing emails in response to newly filed support tickets, in what appears to be a compromise.
The Canadian router manufacturer, Mercku provides equipment to Canadian and European Internet Service providers (ISP) and networking companies including Start.ca, FibreStream, Innsys, RealNett, Orion Telekom, and Kelcom.
Support tickets acknowledged with MetaMask phishing
Support requests submitted to router manufacturer, Mercku are being auto-responded to with phishing emails, BleepingComputer has confirmed.
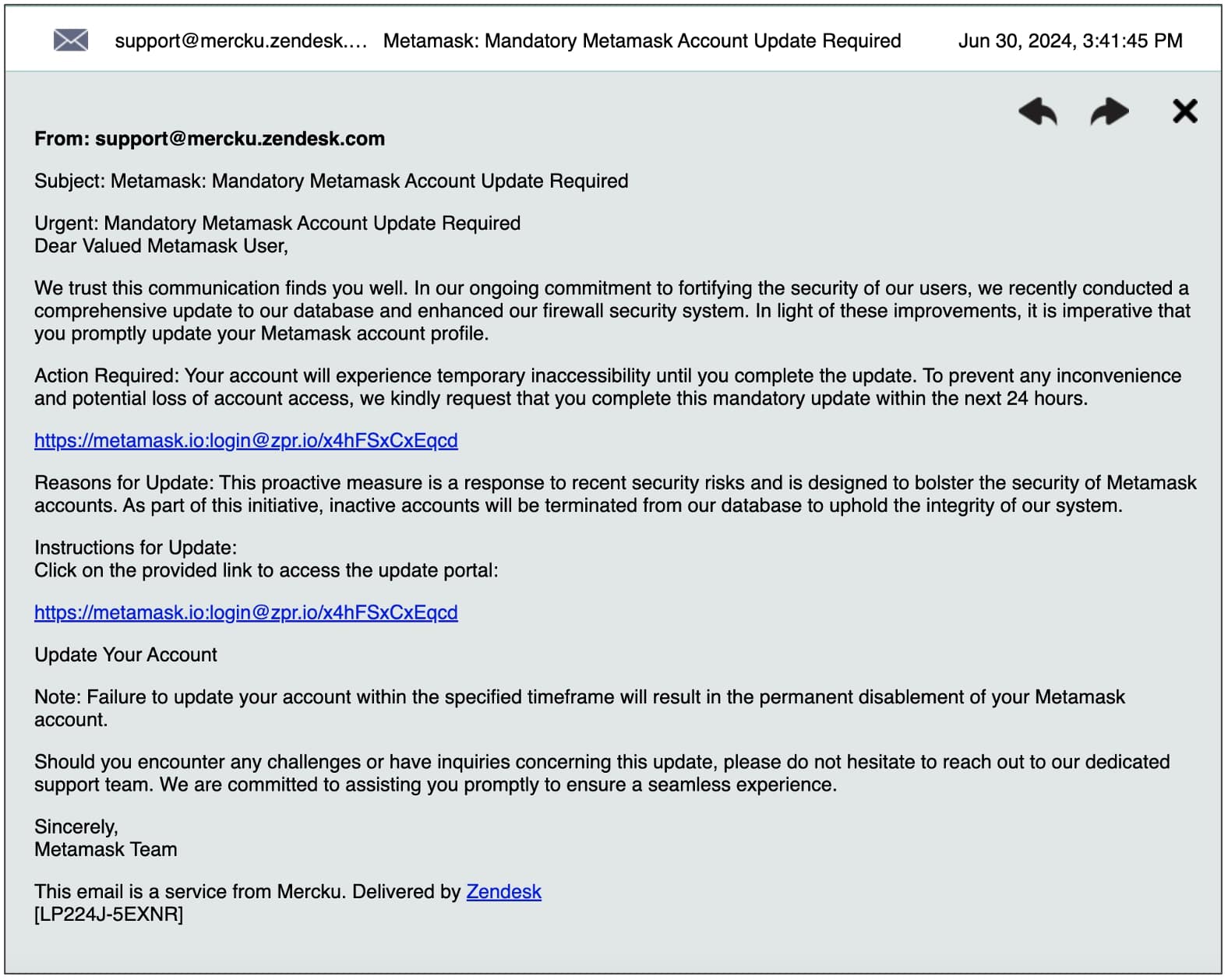
As soon as the online form is submitted, the user is sent an email titled, “Metamask: Mandatory Metamask Account Update Required” shown below:
(BleepingComputer)
Specifically, the email instructs users to “update your Metamask account” within 24 hours or experience “potential loss of account access.”
“We trust this communication finds you well. In our ongoing commitment to fortifying the security of our users, we recently conducted a comprehensive update to our database and enhanced our firewall security system. In light of these improvements, it is imperative that you promptly update your Metamask account profile.
Action Required: Your account will experience temporary inaccessibility until you complete the update. To prevent any inconvenience and potential loss of account access, we kindly request that you complete this mandatory update within the next 24 hours.
hxxps://metamask.io:login@zpr[.]io/x4hFSxCxEqcd
Reasons for Update: This proactive measure is a response to recent security risks and is designed to bolster the security of Metamask accounts. As part of this initiative, inactive accounts will be terminated from our database to uphold the integrity of our system.”
With its offices across Canada, China, Germany, and Pakistan, Mercku makes “mesh WiFi” routers and equipment. ISPs including Start.ca, FibreStream, Innsys, RealNett, Orion Telekom, and Kelcom provide Mercku’s equipment to their customers.

In our tests, we contacted Mercku via its Zendesk portal and received the above message in place of an automated acknowledgment.
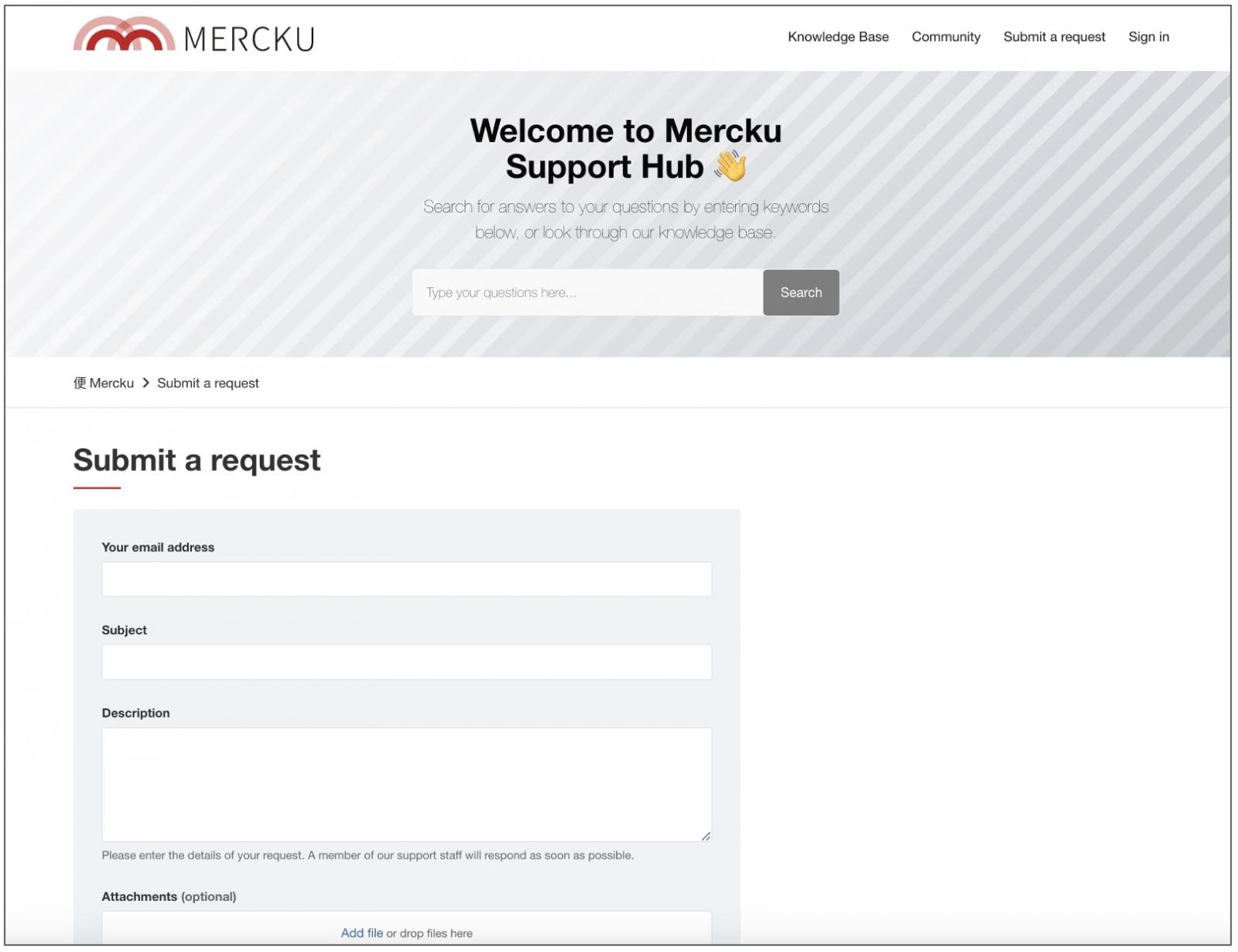
The acknowledgment email is a phishing message. Users should not respond to it and not open any links or attachments contained therein.
MetaMask is a cryptocurrency wallet that uses the Ethereum blockchain and is available as a browser extension and a mobile app.
Given its popularity, MetaMask has often become a target for attackers including phishing actors and crypto scammers.
Abuses userinfo part of a URL to look real
The phishing link included in the email (defanged for your safety) has a rather interesting structure:
hxxps://metamask.io:login@zpr[.]io/x4hFSxCxEqcd
Contrary to how the URL appears, it’s not leading you to “metamask.io”, but zpr[.]io instead.
A URL or an IP address can be represented in different formats. Attackers have abused such variations allowed by the IETF’s specifications to target unsuspecting users with phishing attacks.
The URL schema allows for the usage of a part called “Authority.” This part allows you to specify “userinfo”— which is something like a username, present between the URL’s protocol and the host parts.
Specifically, from RFC 3986, this feature of “userinfo” makes it easy for attackers to abuse it for “semantic attacks.”
“Because the userinfo subcomponent is rarely used and appears before the host in the authority component, it can be used to construct a URI intended to mislead a human user by appearing to identify one (trusted) naming authority while actually identifying a different authority hidden behind the noise. For example
ftp://cnn.example.com&story=breaking_news@10.0.0.1/top_story.htm
might lead a human user to assume that the host is ‘cnn.example.com’, whereas it is actually ‘10.0.0.1’.
Note that a misleading userinfo subcomponent could be much longer than the example above.
A misleading URI, such as that above, is an attack on the user’s preconceived notions about the meaning of a URI rather than an attack on the software itself.”
The same goes for https://google.com@bleepingcomputer.com/tag/security
Although it may appear that you are connecting to ‘google.com’, the part before the ‘@’ represents “userinfo” and not the authentic Google website, so you’d still arrive at BleepingComputer.
In practice, the userinfo part of the URI scheme is rarely used, from a technical perspective. Even though your web browser will still be “sending” userinfo to the server, it’ll be ignored by the server, and your request will proceed as it’d even if the userinfo part was absent (i.e. had the URL been https://www.bleepingcomputer.com/tag/security/).
Regardless, this feature can be and has been abused by threat actors to give off a false impression that a user is reaching out to a legitimate business URL when in actuality they are not.
In this particular case, clicking on hxxps://metamask.io:login@zpr[.]io/x4hFSxCxEqcd first takes you to zpr[.]io/x4hFSxCxEqcd.
The zpr[.]io service, which is a URL shortener abused by the attacker in this instance, further redirects the visitor to another website, hxxps://matjercasa.youcan[.]store.
Fortunately, during our tests, the final destination webpage indicates that the .store domain’s hosting account has been “suspended” and therefore further attacks have been thwarted for now.
BleepingComputer contacted Mercku’s support and press teams over the weekend to notify them of this compromise and ask additional questions about how it occurred.
In the meantime, Mercku customers and prospects should refrain from using the manufacturer’s support portal and interacting with any communications originating from it.
Source link
lol
BleepingComputer has verified that the helpdesk portal of a router maker is currently sending MetaMask phishing emails in response to newly filed support tickets, in what appears to be a compromise. The Canadian router manufacturer, Mercku provides equipment to Canadian and European Internet Service providers (ISP) and networking companies including Start.ca, FibreStream, Innsys, RealNett, Orion Telekom, and Kelcom. Support…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
