New Eldorado ransomware targets Windows, VMware ESXi VMs
by nlqip

A new ransomware-as-a-service (RaaS) called Eldorado emerged in March and comes with locker variants for VMware ESXi and Windows.
The gang has already claimed 16 victims, most of them in the U.S., in real estate, educational, healthcare, and manufacturing sectors.
Researchers at cybersecurity company Group-IB monitored the Eldorado’s activity and noticed its operators promoting the malicious service on RAMP forums and seeking skilled affiliates to join the program.
Eldorado also runs a data leak site that lists victims but it was down at the time of writing.
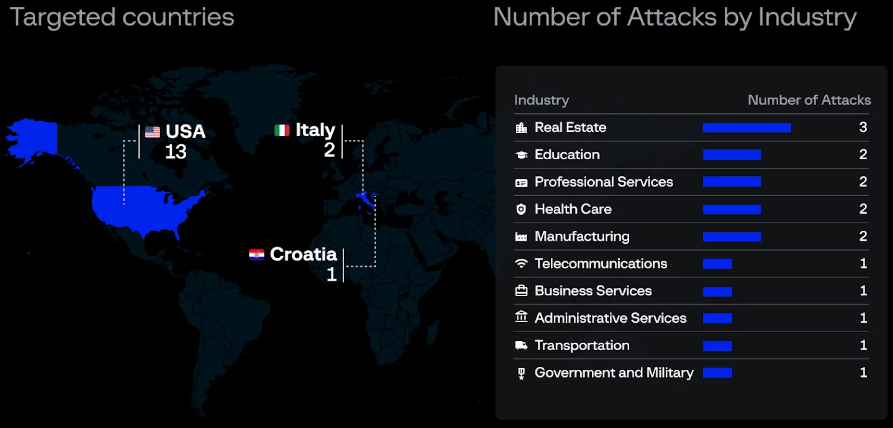
Source: Group-IB
Encrypting Windows and Linux
Eldorado is a Go-based ransomware that can encrypt both Windows and Linux platforms through two distinct variants with extensive operational similarities.
The researchers obtained from the developer an encryptor, which came with a user manual saying that there are 32/64-bit variants available for VMware ESXi hypervisors and Windows.
Group-IB says that Eldorado is a unique development “and does not rely on previously published builder sources.”
The malware uses the ChaCha20 algorithm for encryption and generates a unique 32-byte key and 12-byte nonce for each of the locked files. The keys and nonces are then encrypted using RSA with the Optimal Asymmetric Encryption Padding (OAEP) scheme.
After the encryption stage, files are appended the “.00000001” extension and ransom notes named “HOW_RETURN_YOUR_DATA.TXT” are dropped in the Documents and Desktop folders.
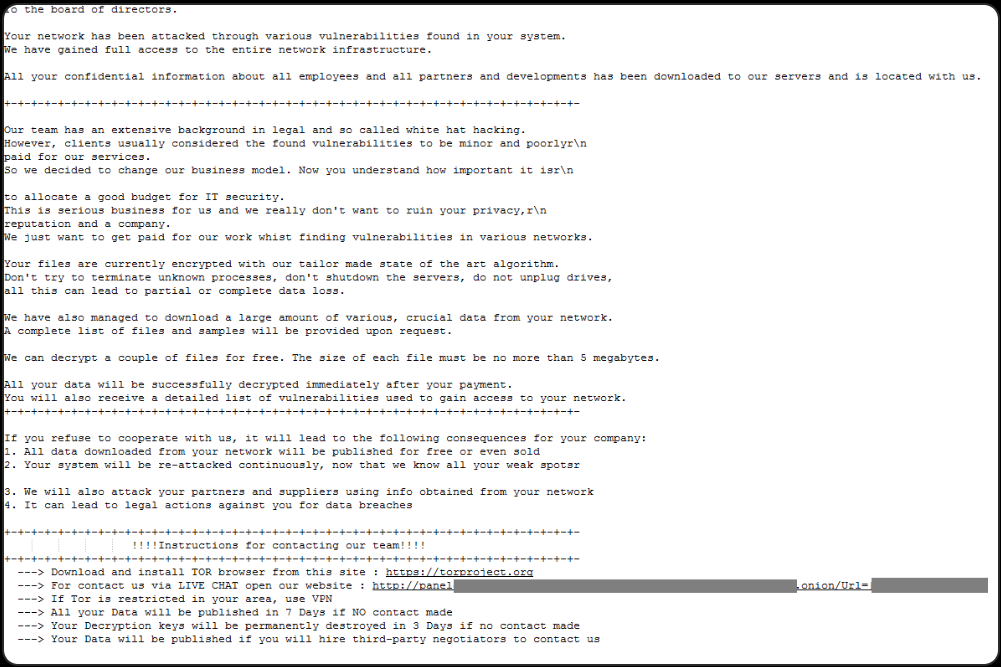
Source: Group-IB
Eldorado also encrypts network shares utilizing the SMB communication protocol to maximize its impact and deletes shadow volume copies on the compromised Windows machines to prevent recovery.
The ransomware skips DLLs, LNK, SYS, and EXE files, as well as files and directories related to system boot and basic functionality to prevent rendering the system unbootable/unusable.
Finally, it’s set by default to self-delete to evade detection and analysis by response teams.
According to Group-IB researchers, who infiltrated the operation, affiliates can customize their attacks. For instance, on Windows they can specify which directories to encrypt, skip local files, target network shares on specific subnets, and prevent self-deletion of the malware.
On Linux, though, customization parameters stop at setting the directories to encrypt.
Defense recommendations
Group-IB highlights that the Eldorado ransomware threat is a new, standalone operation that did not emerge as a rebrand of another group.
The researchers recommend the following defenses, which can help protect against all ransomware attack, to a degree:
- Implement multi-factor authentication (MFA) and credential-based access solutions.
- Use Endpoint Detection and Response (EDR) to quickly identify and respond to ransomware indicators.
- Take data backups regularly to minimize damage and data loss.
- Utilize AI-based analytics and advanced malware detonation for real-time intrusion detection and response.
- Prioritize and periodically apply security patches to fix vulnerabilities.
- Educate and train employees to recognize and report cybersecurity threats.
- Conduct annual technical audits or security assessments and maintain digital hygiene.
- Refrain from paying ransom as it rarely ensures data recovery and can lead to more attacks.
Source link
lol
A new ransomware-as-a-service (RaaS) called Eldorado emerged in March and comes with locker variants for VMware ESXi and Windows. The gang has already claimed 16 victims, most of them in the U.S., in real estate, educational, healthcare, and manufacturing sectors. Researchers at cybersecurity company Group-IB monitored the Eldorado’s activity and noticed its operators promoting the malicious service on…
Recent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
