Avast releases free decryptor for DoNex ransomware and past variants
by nlqip

Antivirus company Avast have discovered a weakness in the cryptographic scheme of the DoNex ransomware family and released a decryptor so victims can recover their files for free.
The company says it has been working with law enforcement to privately provide the decryptor to DoNex ransomware victims since March 2024. Cybersecurity vendors commonly distribute decryptors in this manner to prevent the threat actors from learning about the bug and fixing it.
The flaw was publicly disclosed at last month’s Recon 2024 cybersecurity conference, so Avast has decided to release the decryptor.
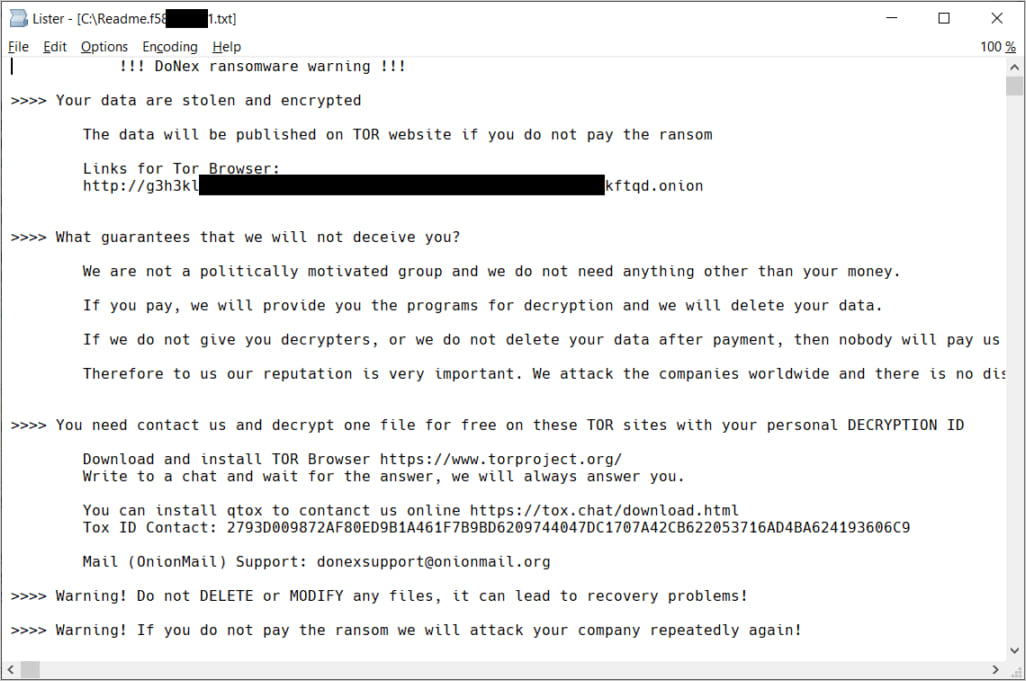
Decrypting DoNex
DoNext is a 2024 rebrand of DarkRace, which was, in turn, a 2023 rebrand of the Muse ransomware, first released in April 2022.
Source: Avast
The flaw discovered by Avast impacts all past DoNex ransomware family variants, including a fake Lockbit 3.0-branded variant used under the ‘Muse’ name in November 2022.
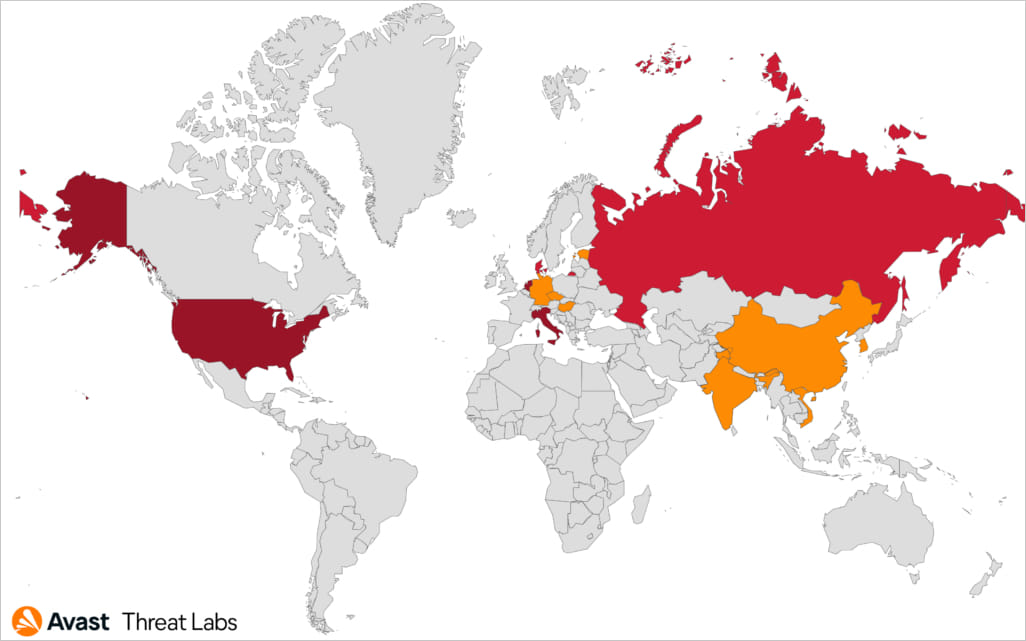
Avast says that based on its telemetry, DoNex’s recent activity was concentrated in the United States, Italy, and Belgium but had a worldwide reach.
Source: Avast
Weakness in cryptography
During the DoNex ransomware’s execution, an encryption key is generated using the ‘CryptGenRandom()’ function, initializing a ChaCha20 symmetric key used to encrypt the target’s files.
After the file encryption phase, the ChaCha20 key is encrypted using RSA-4096 and appended to the end of each file.
Avast has not elaborated on where the weakness lies, so it might concern key reuse, predictable key generation, improper padding, or other problems.
It is worth noting that DoNex uses intermittent encryption for files larger than 1MB. This tactic increases speed when encrypting files but introduces weaknesses that can be leveraged to restore encrypted data without paying a ransom.
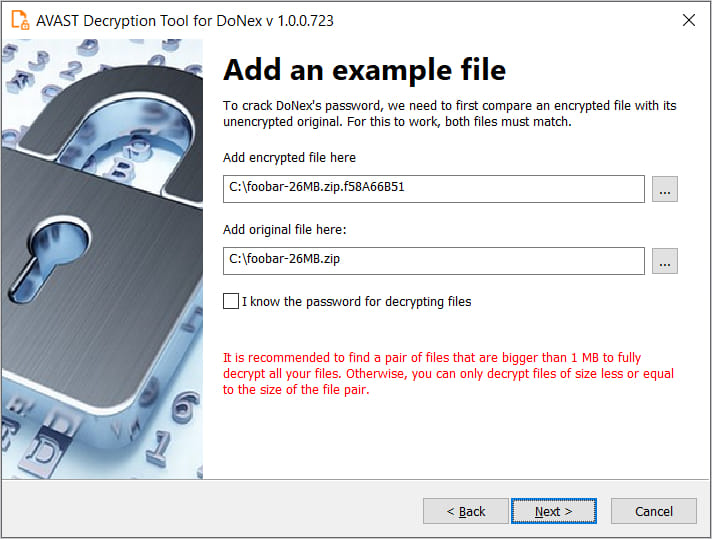
Avast’s decryptor for DoNex and past variants is available from here. Users are recommended to pick the 64-bit version, as the password-cracking step requires a lot of memory.
The decryptor tool needs to be executed by an admin user, requiring a pair of encrypted and original files.
Avast advises users to provide the largest possible file as an “example” file, as it will determine the maximum file size that can be decrypted using the tool.
Source: Avast
Make sure to backup your encrypted files before attempting decryption using the tool, as there’s always the possibility of something going wrong and corrupting those files beyond recovery.
Source link
lol
Antivirus company Avast have discovered a weakness in the cryptographic scheme of the DoNex ransomware family and released a decryptor so victims can recover their files for free. The company says it has been working with law enforcement to privately provide the decryptor to DoNex ransomware victims since March 2024. Cybersecurity vendors commonly distribute decryptors in…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
