Critical Exim bug bypasses security filters on 1.5 million mail servers
by nlqip

Censys warns that over 1.5 million Exim mail transfer agent (MTA) instances are unpatched against a critical vulnerability that lets threat actors bypass security filters.
Tracked as CVE-2024-39929 and patched by Exim developers on Wednesday, the security flaw impacts Exim releases up to and including version 4.97.1.
The vulnerability is due to the incorrect parsing of multiline RFC2231 header filenames, which can let remote attackers deliver malicious executable attachments into end users’ mailboxes by circumventing the $mime_filename extension-blocking protection mechanism.
“If a user were to download or run one of these malicious files, the system could be compromised,” Censys warned, adding that “a PoC is available, but no active exploitation is known yet.”
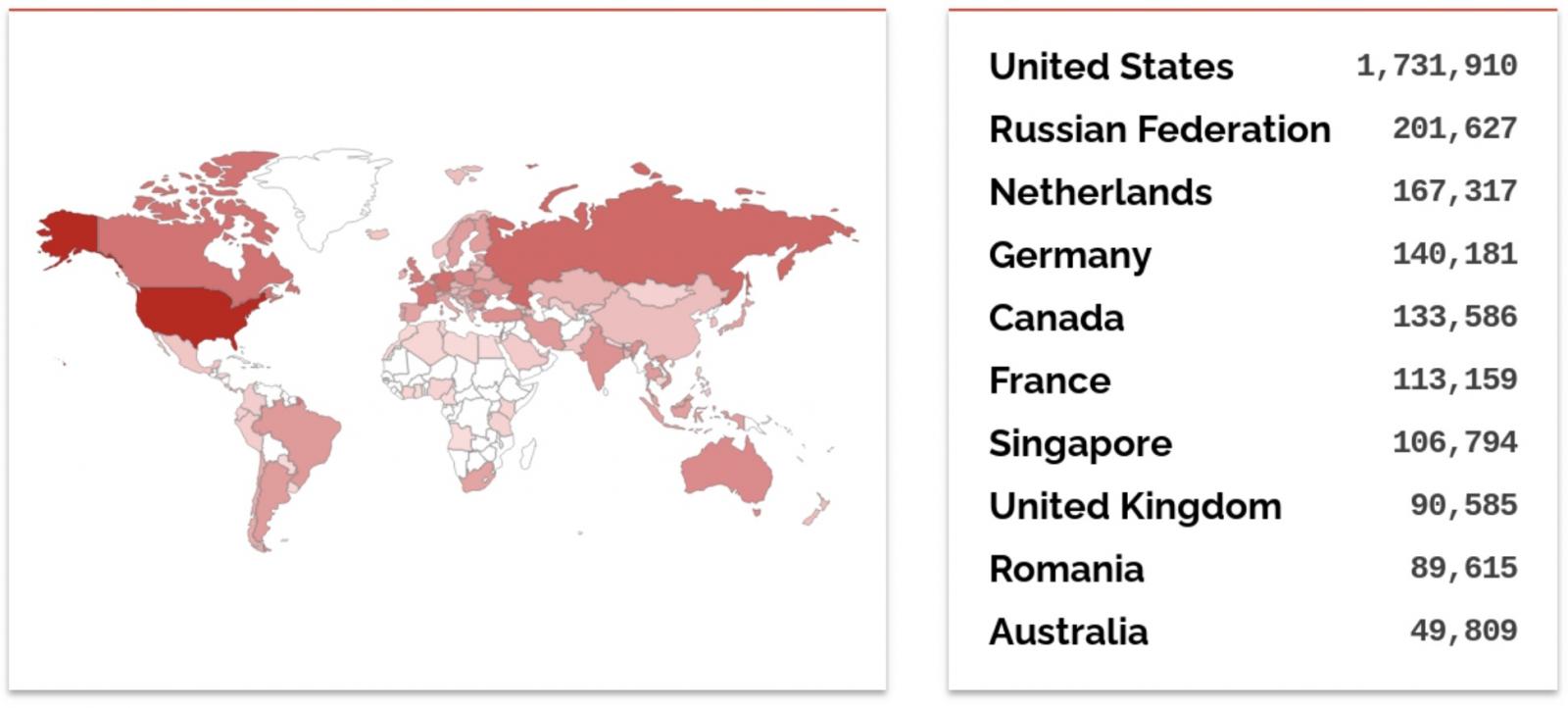
“As of July 10, 2024, Censys observes 1,567,109 publicly exposed Exim servers running a potentially vulnerable version (4.97.1 or earlier), concentrated mostly in the United States, Russia, and Canada,” the company added.
While email recipients will still need to launch the malicious attachment to be affected, the flaw allows threat actors to bypass security checks based on file extensions. This allows them to deliver risky files that are normally blocked, such as executables, into their targets’ mailboxes.
Admins who cannot immediately upgrade Exim are advised to restrict remote access to their servers from the Internet to block incoming exploitation attempts.
Millions of servers exposed online
MTA servers, such as Exim, are often targeted in attacks because they are almost always accessible via the Internet, making them easy to find potential entry points into a target’s network.
Exim is also the default Debian Linux MTA and is the world’s most popular MTA software, based on a mail server survey from earlier this month.
According to the survey, over 59% of the 409,255 mail servers reachable on the Internet during the survey were running Exim, representing just over 241,000 Exim instances.
Also, per a Shodan search, over 3.3 million Exim servers are currently exposed online, most in the United States, followed by Russia and the Netherlands. Censys found 6,540,044 public-facing mail servers online, 4,830,719 (roughly 74%) running Exim.
The National Security Agency (NSA) revealed in May 2020 that the notorious Russian military hacking group Sandworm has been exploiting a critical CVE-2019-10149 Exim flaw (dubbed The Return of the WIZard) since at least August 2019.
More recently, in October, the Exim devs patched three zero-days disclosed through Trend Micro’s Zero Day Initiative (ZDI), one of them (CVE-2023-42115) exposing millions of Internet-exposed Exim servers to pre-auth RCE attacks.

Source link
lol
Censys warns that over 1.5 million Exim mail transfer agent (MTA) instances are unpatched against a critical vulnerability that lets threat actors bypass security filters. Tracked as CVE-2024-39929 and patched by Exim developers on Wednesday, the security flaw impacts Exim releases up to and including version 4.97.1. The vulnerability is due to the incorrect parsing…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
