Hackers use PoC exploits in attacks 22 minutes after release
by nlqip

Threat actors are quick to weaponize available proof-of-concept (PoC) exploits in actual attacks, sometimes as quickly as 22 minutes after exploits are made publicly available.
That is according to Cloudflare’s Application Security report for 2024, which covers activity between May 2023 and March 2024 and highlights emerging threat trends.
Cloudflare, which currently processes an average of 57 million HTTP requests per second, continues to see heightened scanning activity for disclosed CVEs, followed by command injections and attempts to weaponize available PoCs.
During the examined period, the most targeted flaws were CVE-2023-50164 and CVE-2022-33891 in Apache products, CVE-2023-29298, CVE-2023-38203 and CVE-2023-26360 in Coldfusion, and CVE-2023-35082 in MobileIron.
A characteristic example of the rise in the speed of weaponization is CVE-2024-27198, an authentication bypass flaw in JetBrains TeamCity.
Cloudflare observed a case of an attacker deploying a PoC-based exploit 22 minutes after its publication, leaving defenders essentially no margin for remediation opportunity.
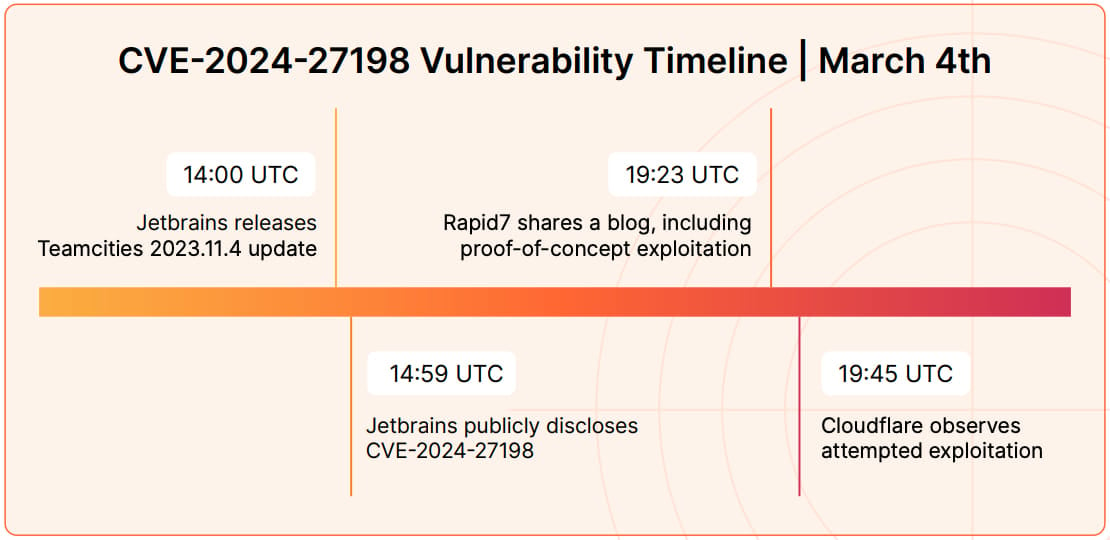
Source: Cloudflare
The internet firm says the only way to combat this speed is to employ AI assistance to quickly develop effective detection rules.
“The speed of exploitation of disclosed CVEs is often quicker than the speed at which humans can create WAF rules or create and deploy patches to mitigate attacks,” explains Cloudflare in the report.
“This also applies to our own internal security analyst team that maintains the WAF Managed Ruleset, which has led us to combine the human written signatures with an ML-based approach to achieve the best balance between low false positives and speed of response.”
Cloudflare says this is partially the result of specific threat actors specializing in certain CVE categories and products, developing an in-depth understanding of how to quickly take advantage of new vulnerability disclosures.
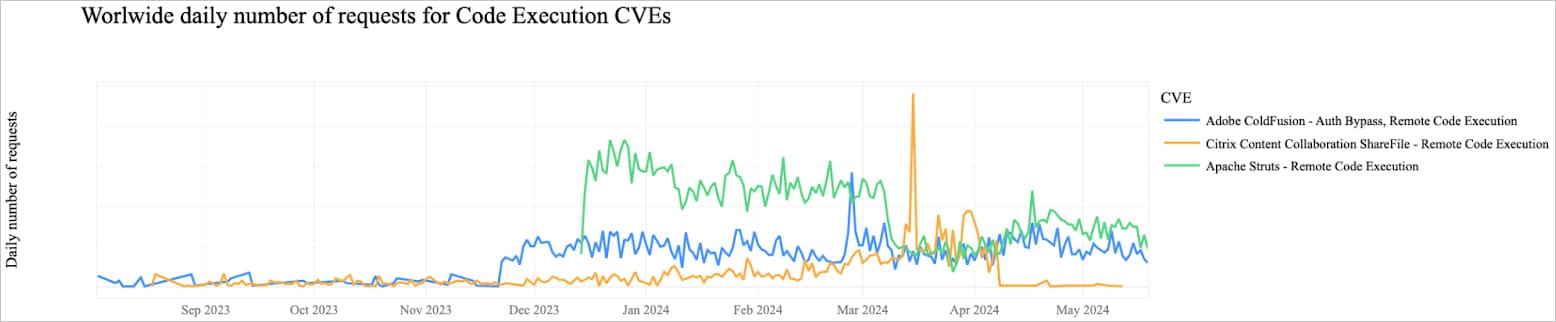
Source: Cloudflare
6.8% of all internet traffic is DDoS
Another staggering highlight in Cloudflare’s report is that 6.8% of all daily internet traffic is distributed denial of service (DDoS) traffic aimed at rendering online apps and services unavailable to legitimate users.
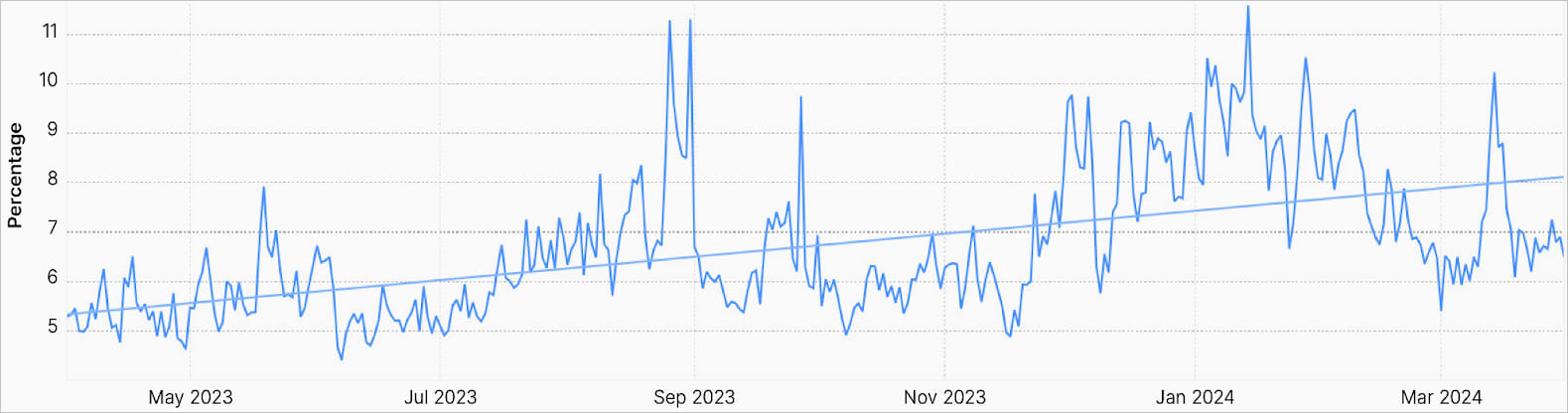
Source: Cloudflare
This is a notable increase compared to the 6% recorded over the previous 12-month period (2022-2023), showing an increase in the overall volume of DDoS attacks.
Cloudflare says that during large global attack events, malicious traffic may account for as much as 12% of all HTTP traffic.
“Focusing on HTTP requests only, in Q1 2024 Cloudflare blocked an average of 209 billion cyber threats each day (+86.6% YoY) […which] is a substantial increase in relative terms compared to the same time last year,” says Cloudflare.
The firm’s PDF report, available for download here, provides additional recommendations for defenders and deeper insights into the compiled stats.

Source link
lol
Threat actors are quick to weaponize available proof-of-concept (PoC) exploits in actual attacks, sometimes as quickly as 22 minutes after exploits are made publicly available. That is according to Cloudflare’s Application Security report for 2024, which covers activity between May 2023 and March 2024 and highlights emerging threat trends. Cloudflare, which currently processes an average…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
