How cybercriminals recruit insiders for malicious acts
by nlqip

Cybersixgill
Insider Threats: Government and military
Transcending from cybercrime to espionage, we discovered several posts in which actors solicited governmental or government-affiliated insiders to provide information. This includes individuals, like in the image below, who can provide national citizen databases to assist in doxing. An actor seeking an insider in the French government to provide citizen data.
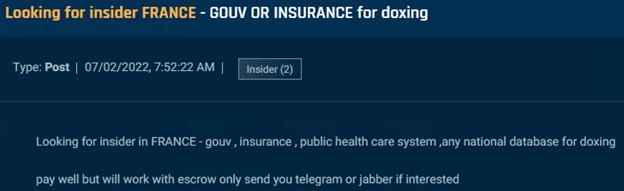
Cybersixgill
Other posts seek individuals who can provide classified information. For example, this next post appeared several times across several forums and Telegram from a self-described “intelligence analysis corporation” offering $1,000-$2,000 as a finders fee for someone that can connect them with an insider at a US military contractor.
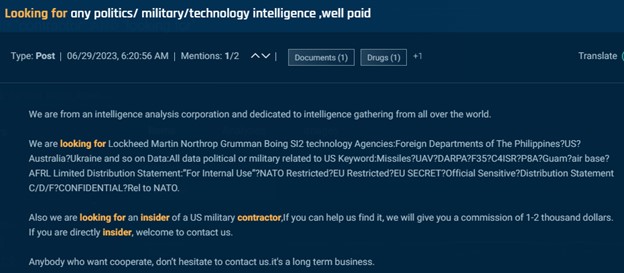
Cybersixgill
Finally, we also discovered the below post in which an individual purported to sell sixteen sets of classified government data, including proprietary data belonging to defense manufacturers such as Raytheon and Elbit. The post also lists a secret document about a confidential Five Eyes military exercise for $300, noting that it was obtained by an insider.

Cybersixgill
We must emphasize that posts soliciting insiders to provide classified information are rare. The penalties for such activities are severe, and most of the dark web’s users are financially motivated. Even so, it is not unheard of for an insider to leak classified information on the deep and dark web; most recently, a Massachusetts National Guardsman has been charged with posting classified documents on a Discord server.
Defending Against Insider Threats
Employees can pose a unique type of threat to an organization. Most employees are not malicious, and they ought to be trusted with access to the data and systems needed for performing their tasks. However, those who are lured by a variety of methods to use their positions to assist in criminal enterprises can cause significant financial and reputational damage to their employers.
According to the 2023 Verizon Data Breach Investigations Report, malicious insiders perpetrate about 19% of known data breaches. While there is no way of knowing for sure how many of these attacks originated from a partnership forged on the deep and dark web, there are several practices that companies can take to protect themselves.
- Principal of least privilege: Employee privileges should be limited only to what their tasks require.
- Job rotation: Regular cycling of employees between tasks to reveal fraudulent activity.
- Multiple signoff: Execution of sensitive actions should require multiple employees to approve.
- VIP account protection: Customers with sensitive accounts or who are more likely to be targeted should be able to opt-in to more stringent account protection.
- Employee awareness: Employees should understand that threat actors seek to recruit their peers and perpetrate fraud. If they see something suspicious, they should report it.
- Automated detection: Use of software to flag suspicious activities.
- Underground monitoring: Organizations must understand adversarial efforts to recruit insiders. Real-time cyber threat intelligence from the clear, deep, and dark web is essential to gather the information needed to expose organizational risk from insider threats.
A rogue employee can severely impact a business’s operations, finances, network security, and brand. They are far more than just an “IT problem” or even a “security team problem.” A proper organizational defense requires coordination between technical and non-technical players, from the SOC to HR, in order to keep the company secure.
Organizations must identify which of their employees are in roles that might be targeted for recruitment by cybercriminals, and enforce stringent monitoring and controls to neutralize any threats from inside the building.
Source link
lol
Cybersixgill Insider Threats: Government and military Transcending from cybercrime to espionage, we discovered several posts in which actors solicited governmental or government-affiliated insiders to provide information. This includes individuals, like in the image below, who can provide national citizen databases to assist in doxing. An actor seeking an insider in the French government to provide…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
