5 steps to automate user access reviews and simplify IT compliance
by nlqip
As the landscape of modern work changes, with its distributed teams and quickly evolving cloud-based technologies, maintaining access controls is an increasingly Sisyphean task.
The process of achieving and maintaining IT compliance certifications is the perfect microcosm of this challenge: The work involved in identifying and designating assets as “in scope” for each regulation has become drastically more laborious in the modern context of distributed workers and rapid SaaS adoption.
While the proliferation of SaaS tools has been a boon for worker productivity, it introduces substantial complexity when it comes to IT audits and compliance.
If you’ve ever been tasked with preparing and gathering evidence for SOC 2, HIPAA, or PCI DSS, you know just how daunting the project can feel.
Tackling IT compliance in the age of SaaS sprawl
A key component of IT compliance regulations involves assessing and defining which systems and applications are “in scope,” meaning that they house, process, or transmit confidential data that needs to be protected.
Organizations need to perform regular user access reviews on applications in scope to determine who still has access, verify that they need continued access, and remove access from anyone who doesn’t.
Of course, the challenge of maintaining these certifications in a SaaS-first world is that you can’t define which applications are in scope for each regulation if you don’t even know what’s out there.
Security and IT teams rarely have a complete picture of what workers are using or where they might be storing sensitive corporate data, and manually keeping up with changes as users sign up for new applications could be its own full-time job.
Meanwhile, SaaS sprawl isn’t a problem organizations have the luxury of ignoring anymore.
Recent supply chain attacks have underscored the fact that the modern attack surface is the SaaS attack surface, which means organizations preparing for these certifications need to account for their organization’s SaaS sprawl and shadow IT.
The secret to simplifying user access reviews? Automation.
SaaS discovery is a beast of its own, but there are other aspects of user access reviews that can require a significant amount of tedious, manual work. For example, once you’ve identified that an app is in use, you still need to track down which users have active accounts and figure out who at your organization owns the app in order to remove access for those who don’t need it.
Ahead, we’ll show you how to get audit-ready faster by automating user access reviews with Nudge Security. We’ll help you discover and review access for both the SaaS apps you already know about and the ones you don’t, all while minimizing manual effort.
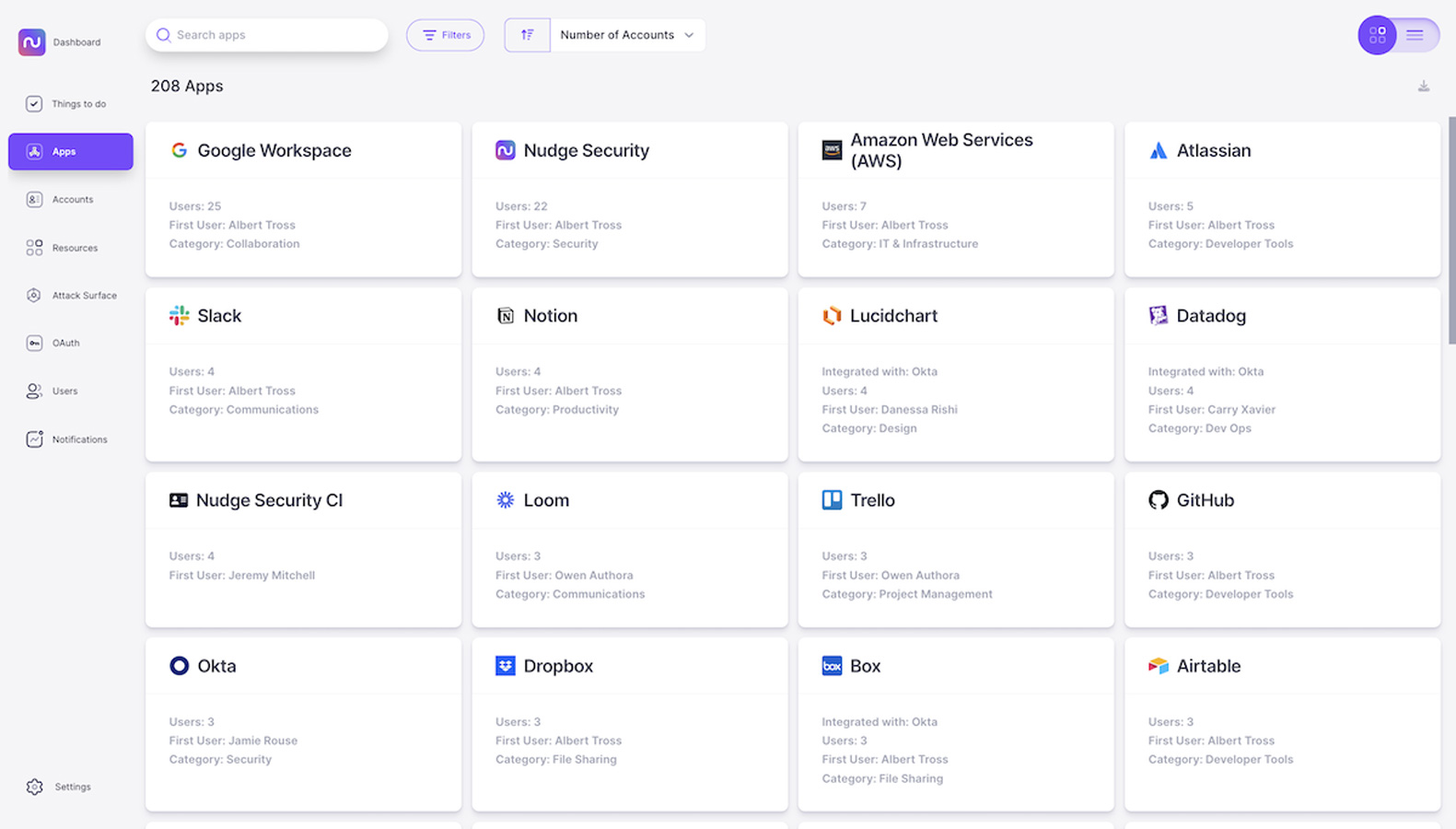
1. Discover your company’s cloud and SaaS assets, including shadow IT.
Whether it takes the form of a rogue AWS account created by a developer or an unsanctioned file-sharing app that a few vendors or clients insist on using, critical data often finds its way outside of corporate-managed, IT-approved applications. You could try questioning every department about the apps they use, or digging through chat logs and billing statements for clues, but none of those methods are sustainable or effective. Your organization needs a plan for discovering both managed and unmanaged SaaS applications on a regular basis, before you can think about whether they’re in scope.
Nudge Security uses a patented SaaS discovery method to identify all the cloud and SaaS assets in use at your organization, including apps that aren’t managed by corporate IT and security. Applications are categorized by type and key information like first user, all users, security program details and more will all be at your fingertips.
As users sign up for new applications, they’ll automatically appear in the dashboards, and you can get alerts when new apps are introduced.
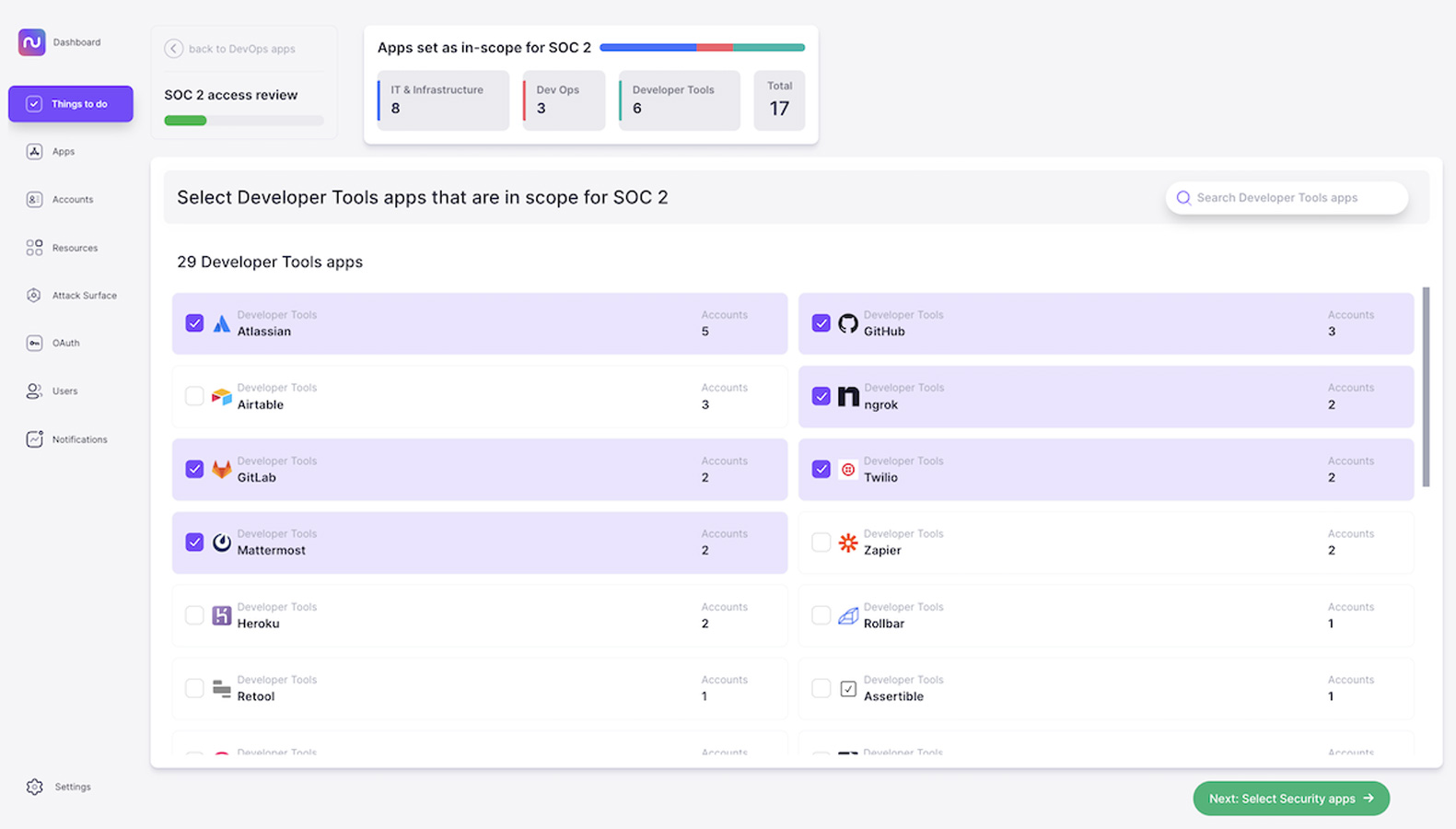
2. Determine which assets are in scope.
Nudge Security’s playbook to automate SOC 2 access reviews, for instance, starts with determining which cloud and SaaS assets are in scope for your organization. The playbook uses smart app categorization to give you a headstart in identifying the applications most likely to be in scope by walking you through high-priority categories, such as infrastructure apps, devops apps, developer tools, and security apps.
Nudge Security keeps track of the apps you’ve identified as in scope, helping you streamline future access reviews. You can easily update the scope you’ve defined as your users add new apps over time.
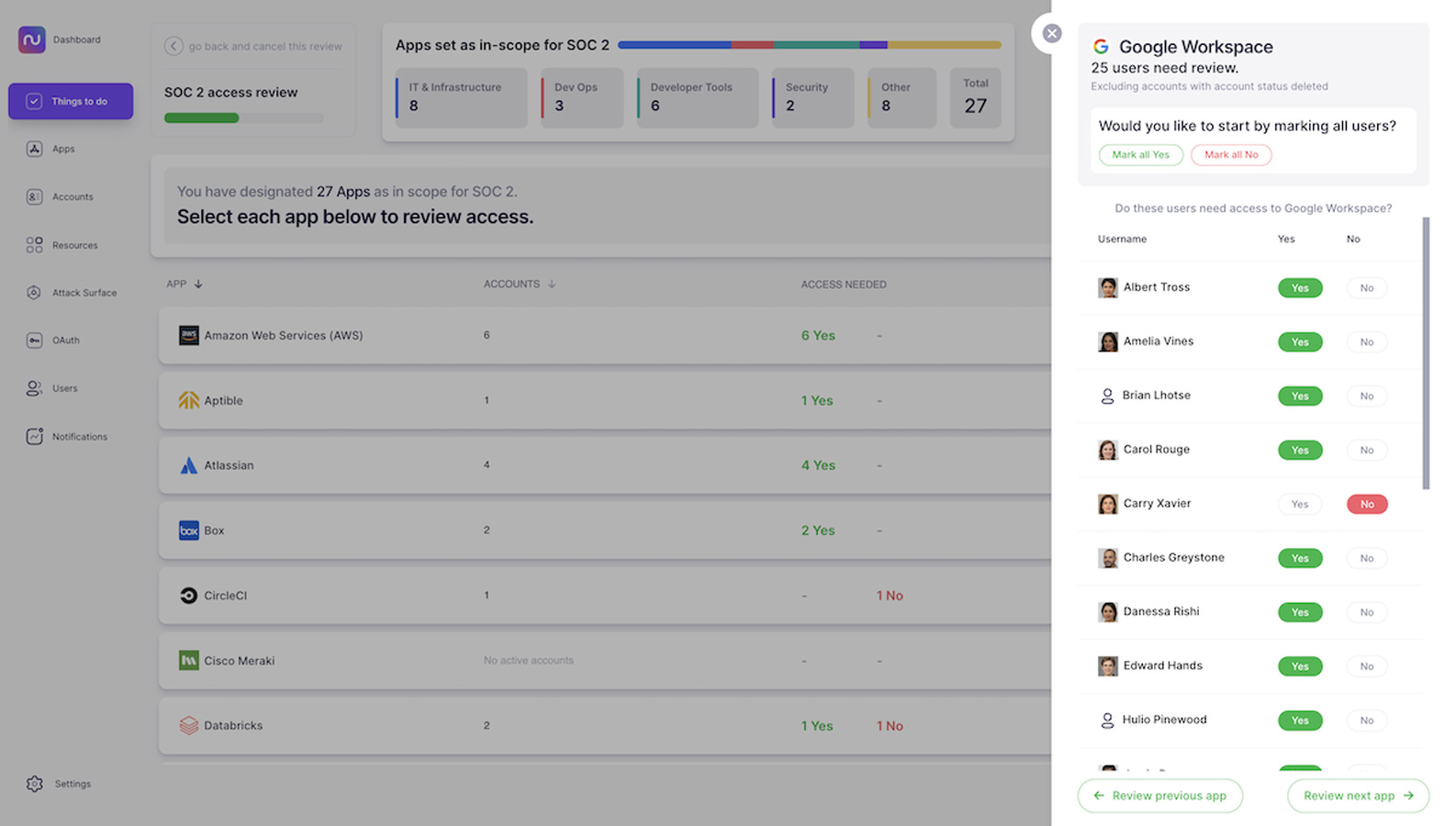
3. Review who needs access to each application.
For each of the applications you’ve classified as in scope, Nudge Security walks you through a review of the users at your organization who have active accounts. You can then automate nudges through Slack or email to ask users to confirm which accounts are still needed and collect their responses.
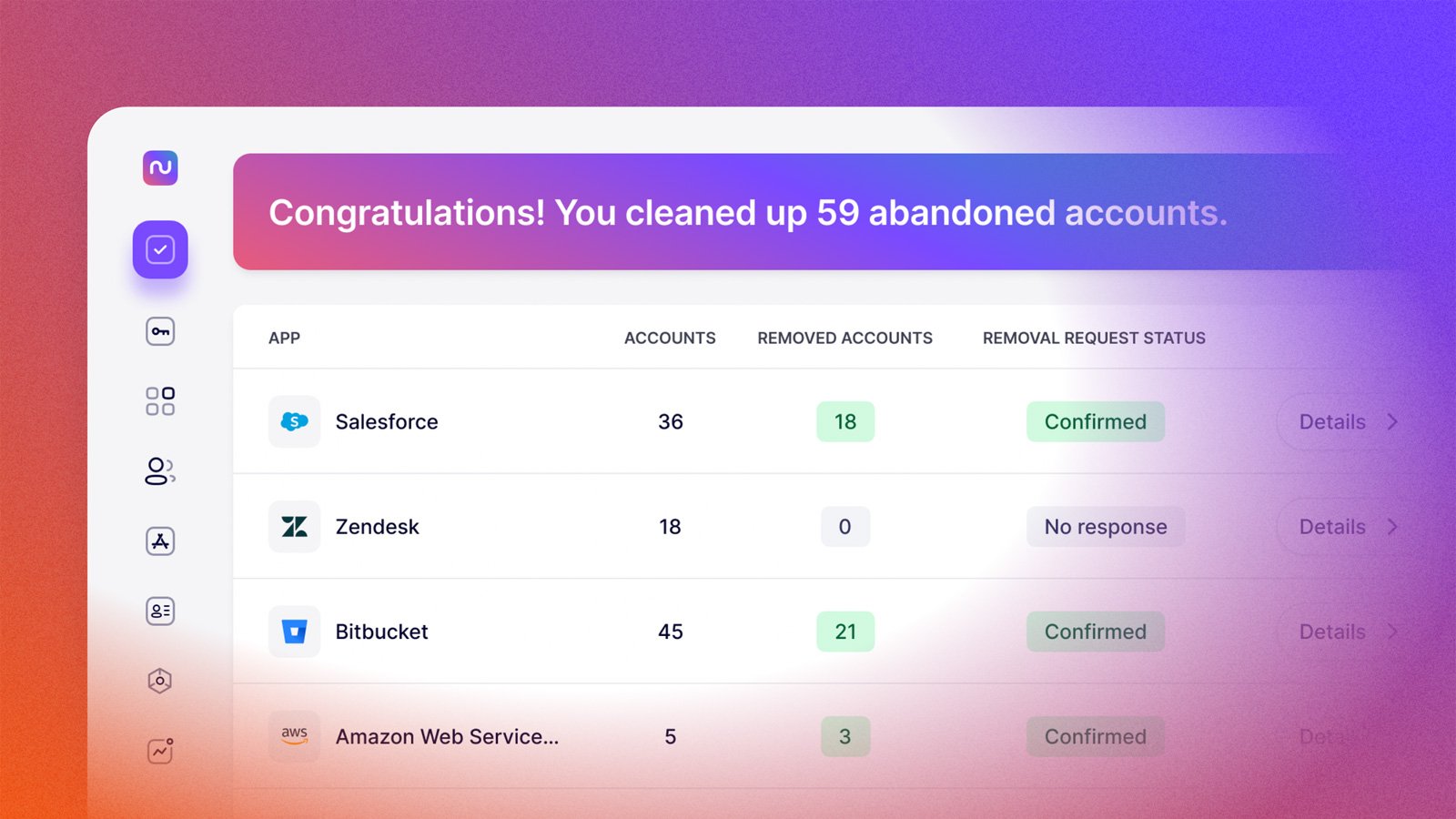
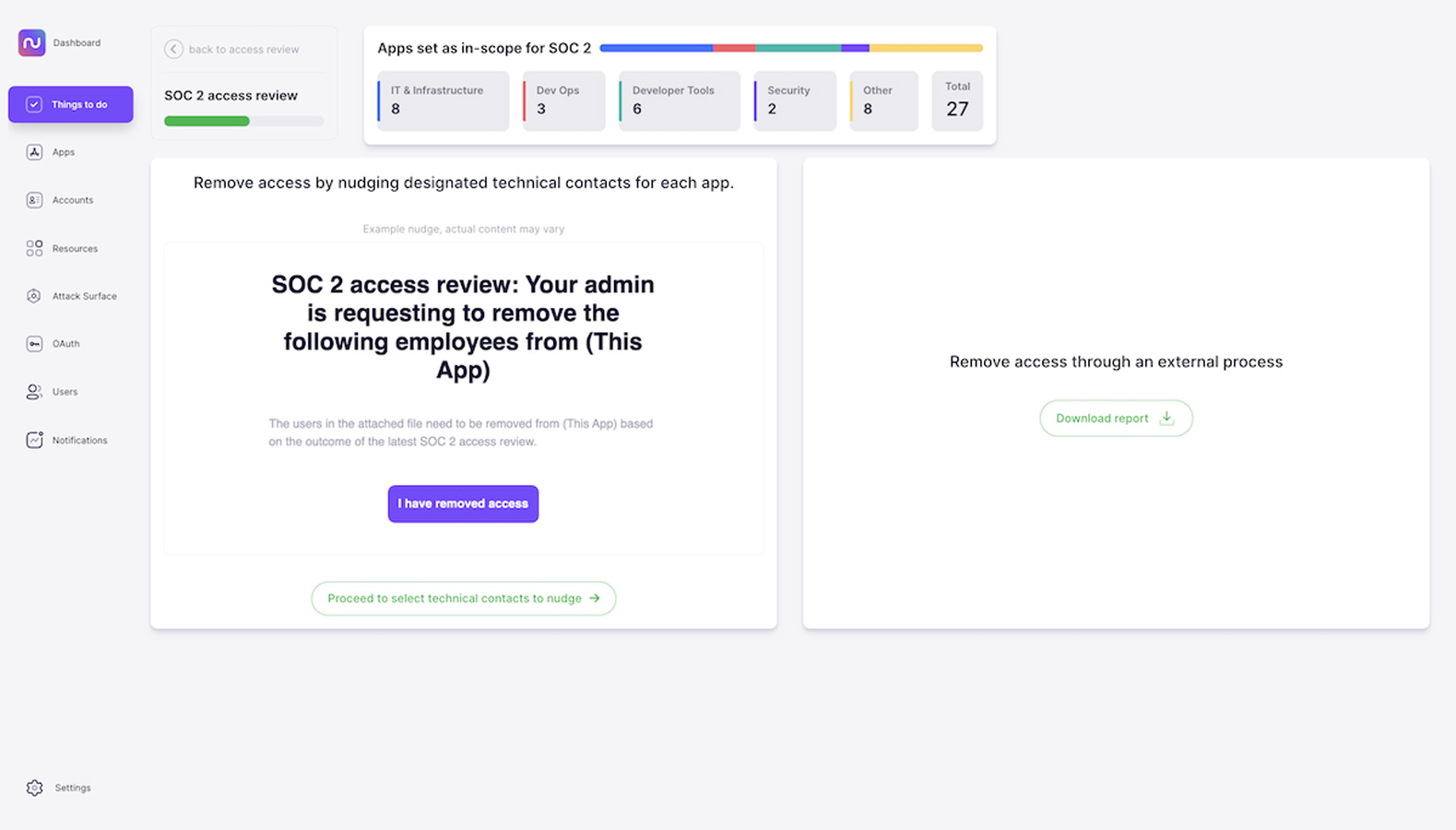
4. Easily remove access by enlisting technical contacts.
When you discover a team at your organization using an application that isn’t managed by anyone in corporate IT or security, how do you remove access for users who no longer use it? Someone within the team is likely an administrator, but without an efficient system in place, tracking down that admin user can require a lot of legwork. Multiply that by every application on your list and you’d have quite a bit of work ahead of you.
Nudge Security gives you two options for removing access for users who no longer need it. If you have an existing process for managing access that works well for you, you can download a list of users and applications and handle it yourself.
If you don’t, you can use nudges to enlist the owner of each app within your organization to remove access, with instructions and a link to verify that they’ve completed the task.
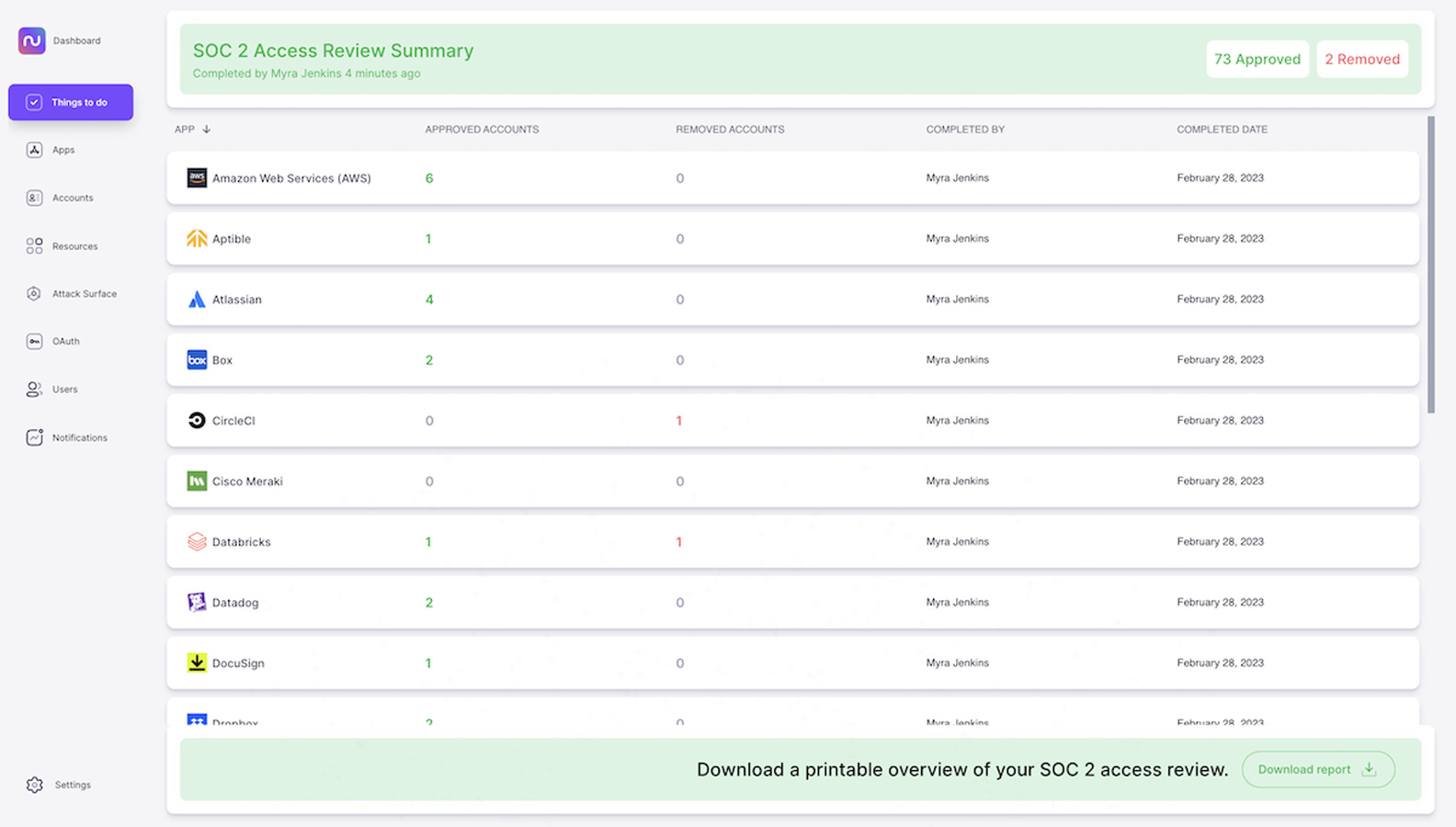
5. Generate audit-ready reports.
Once you’ve received confirmation that the accounts you flagged have been removed, you can officially complete your access review and view a summary, which will be stored for your reference. You’ll also get the option to download a printable report summarizing the applications included in your access review and the users whose access you’ve either verified or removed.
You can share this report with your auditors to demonstrate that you have a repeatable process in place to maintain your compliance certifications.
Simplify IT compliance and much more with Nudge Security
In summary, Nudge Security’s automated user access review playbook can help you:
- Capture and classify all of your in-scope assets, starting with complete discovery and smart app categorization to speed up your process.
- Easily identify users associated with each application and nudge them to verify if they need continued access.
- Engage application technical owners inside or outside of IT to remove accounts that are no longer needed.
- Generate an auditor-ready report of your user access review to demonstrate a repeatable process.
With Nudge Security, you can also automate IT offboarding, discover genAI accounts, and speed up vendor security reviews.
Start a free trial and begin automating tedious IT governance tasks today.
Sponsored and written by Nudge Security..
Source link
lol
As the landscape of modern work changes, with its distributed teams and quickly evolving cloud-based technologies, maintaining access controls is an increasingly Sisyphean task. The process of achieving and maintaining IT compliance certifications is the perfect microcosm of this challenge: The work involved in identifying and designating assets as “in scope” for each regulation has…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
