Black Basta ransomware switches to more evasive custom malware
by nlqip

The Black Basta ransomware gang has shown resilience and an ability to adapt to a constantly shifting space, using new custom tools and tactics to evade detection and spread throughout a network.
Black Basta is a ransomware operator who has been active since April 2022 and is responsible for over 500 successful attacks on companies worldwide.
The ransomware group follows a double-extortion strategy, combining data theft and encryption, and demands large ransom payments in the millions. The ransomware gang previously partnered with the QBot botnet to gain initial access to corporate networks.
However, after the QBot botnet was disrupted by law enforcement, Mandiant reports that the ransomware gang had to create new partnerships to breach corporate networks.
Moreover, Mandiant, who tracks the threat actors as UNC4393, has identified new malware and tools used in Black Basta intrusions, demonstrating evolution and resilience.
The Black Basta ransomware gang has had an active year thus far, compromising notable entities such as Veolia North America, Hyundai Motor Europe, and Keytronic.
The threat group’s sophistication is reflected in the fact that it often has access to zero-day vulnerability exploits, including Windows privilege elevation (2024-26169) and VMware ESXi authentication bypass flaws (CVE-2024-37085).
New Black Basta tactics and tools
After the FBI and DOJ took down the QBot infrastructure in late 2023, Black Basta turned to other initial access distribution clusters, most notably those delivering DarkGate malware.
Later, Black Basta switched to using SilentNight, a versatile backdoor malware delivered through malvertising, marking a departure from phishing as their primary method for initial access.
Mandiant reports that Black Basta has gradually switched from using publicly available tools to internally developed custom malware.
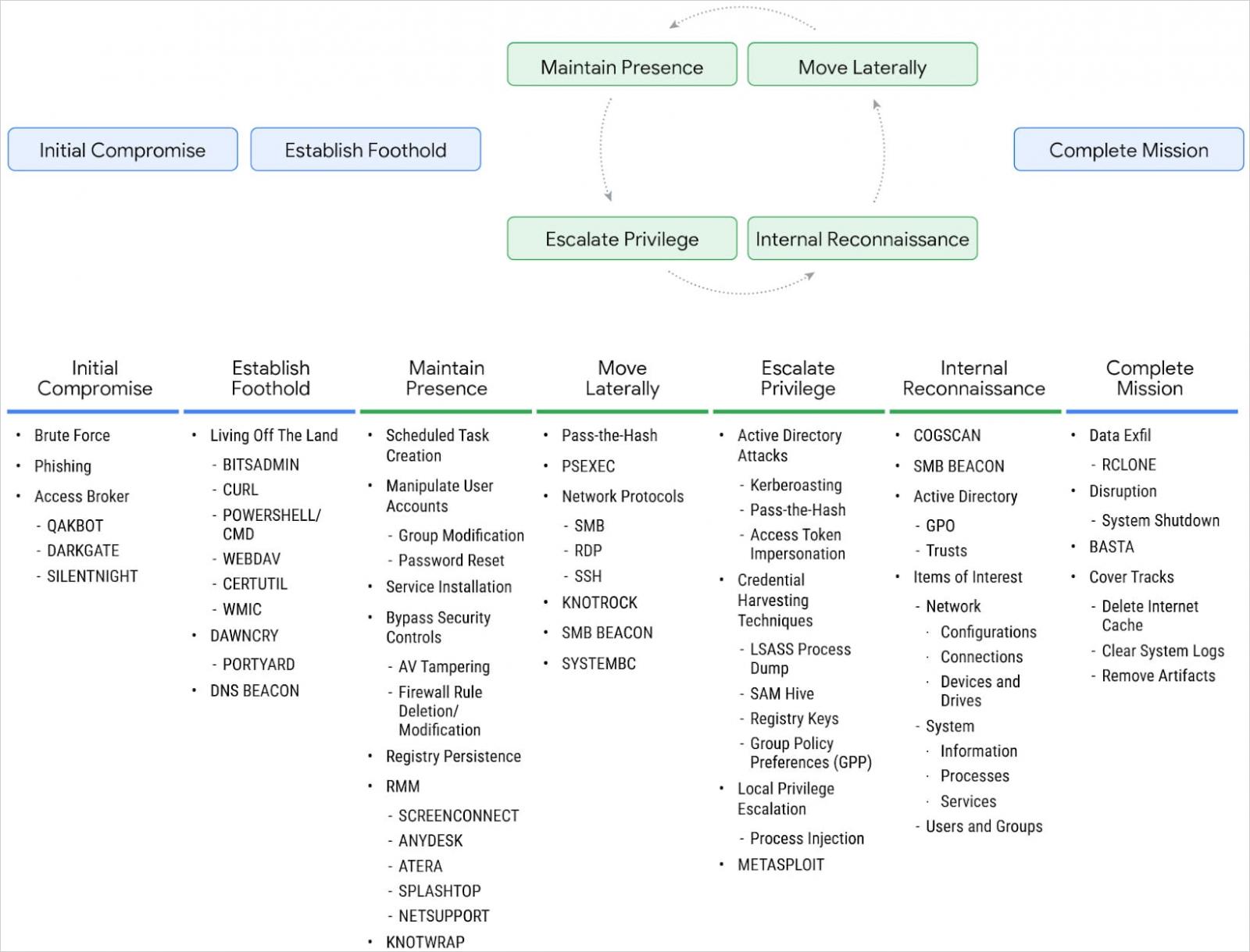
Source: Mandiant
In early 2024, UNC4393 was observed deploying a custom memory-only dropper named DawnCry. This dropper initiated a multi-stage infection, followed by DaveShell, which ultimately led to the PortYard tunneler.
PortYard, also a custom tool, establishes connections to Black Basta’s command and control (C2) infrastructure and proxies traffic.
Other noteworthy custom tools used by Black Basta in recent operations are:
- CogScan: A .NET reconnaissance tool used to gather a list of hosts available on the network and collect system information.
- SystemBC: A tunneler that retrieves proxy-related commands from a C2 server using a custom binary protocol over TCP.
- KnockTrock: A .NET-based utility that creates symbolic links on network shares and executes the BASTA ransomware executable, providing it with the path to the newly created symbolic link.
- KnowTrap: A memory-only dropper written in C/C++ that can execute an additional payload in memory.
Combined with the above, Black Basta continues using “living off the land” binaries and readily available tools in its latest attacks, including the Windows certutil command-line utility to download SilentNight and the Rclone tool to exfiltrate data.
All in all, Black Basta remains a significant global threat and one of the top players in the ransomware space.

Source link
lol
The Black Basta ransomware gang has shown resilience and an ability to adapt to a constantly shifting space, using new custom tools and tactics to evade detection and spread throughout a network. Black Basta is a ransomware operator who has been active since April 2022 and is responsible for over 500 successful attacks on companies…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
