Month: July 2024
‘This year we have got a big one coming [with HashiCorp]. … Part of the discipline is also making sure that we kind of digest them at the right rate and pace and put them into our global market distribution engine,’ says IBM CEO Arvind Krishna on the company’s second-quarter earnings call. IBM exceeded expectations…
Read MoreGoogle Chrome now warns when downloading risky password-protected files and provides improved alerts with more information about potentially malicious downloaded files. These new, more detailed warning messages help users quickly learn the nature of the danger presented by each file downloaded from the Internet. For this, Google introduced a two-tier download warning system that uses AI-powered…
Read MoreOnce upon a time, I.T. security teams depended on hodgepodges of different cybersecurity solutions from various vendors. However, these multivendor tech stacks became prohibitively costly and complex to integrate and manage, creating gaps for threat actors to exploit. In a webinar for MSP and SME leaders, Cynet experts will explain how these challenges are driving…
Read More“An attacker could exploit a bypass using an API request with Content-Length set to 0, causing the Docker daemon to forward the request without the body to the AuthZ plugin, which might approve the request incorrectly,” Docker said in the advisory. The AuthZ plugin would have otherwise denied the request if the body had been…
Read MoreJul 25, 2024NewsroomCybercrime / Online Safety Meta Platforms on Wednesday said it took steps to remove around 63,000 Instagram accounts in Nigeria that were found to target people with financial sextortion scams. “These included a smaller coordinated network of around 2,500 accounts that we were able to link to a group of around 20 individuals,”…
Read MoreWhile the specifics for security testing vary for applications, web applications, and APIs, a holistic and proactive applications security strategy is essential for all three types. There are six core types of testing that every security professional should know about to secure their applications, regardless of what phase they are in in development or deployment.…
Read MoreData Wallets Using the Solid Protocol I am the Chief of Security Architecture at Inrupt, Inc., the company that is commercializing Tim Berners-Lee’s Solid open W3C standard for distributed data ownership. This week, we announced a digital wallet based on the Solid architecture. Details are here, but basically a digital wallet is a repository for…
Read MoreJul 25, 2024NewsroomDNS Security /Vulnerability The Internet Systems Consortium (ISC) has released patches to address multiple security vulnerabilities in the Berkeley Internet Name Domain (BIND) 9 Domain Name System (DNS) software suite that could be exploited to trigger a denial-of-service (DoS) condition. “A cyber threat actor could exploit one of these vulnerabilities to cause a…
Read More“I think [dismantling CISA] would be disastrous,” Michael Daniel, CEO of the Cyber Threat Alliance and former Special Assistant to President Obama and Cybersecurity Coordinator on the National Security Council Staff, tells CSO. “Reasonable people can disagree about how effective CISA has been, but we have labored for literally decades to create an effective cyber…
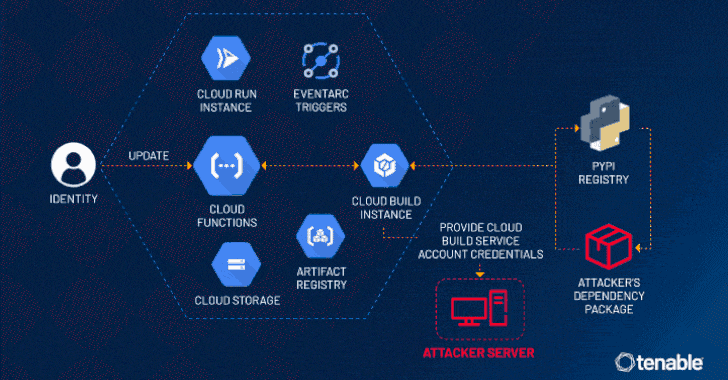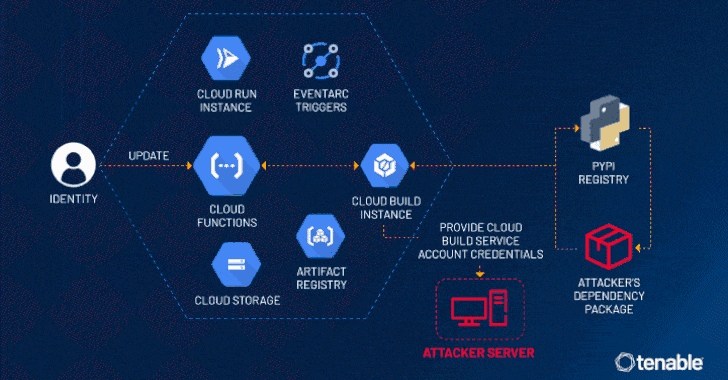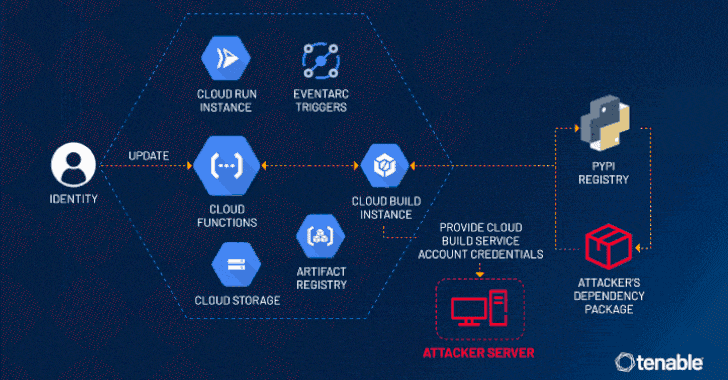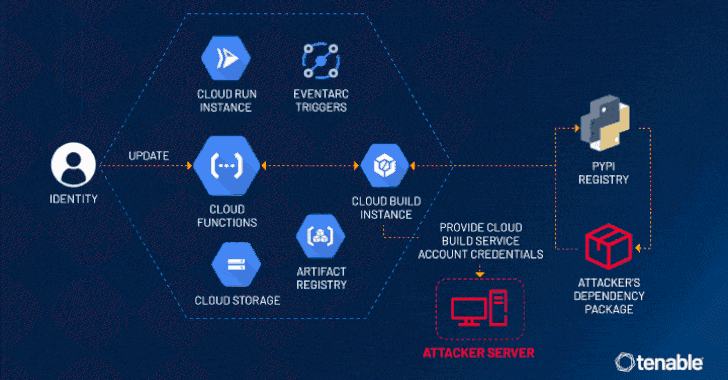
Read MoreJul 25, 2024NewsroomCloud Security / Vulnerability Cybersecurity researchers have disclosed a privilege escalation vulnerability impacting Google Cloud Platform’s Cloud Functions service that an attacker could exploit to access other services and sensitive data in an unauthorized manner. Tenable has given the vulnerability the name ConfusedFunction. “An attacker could escalate their privileges to the Default Cloud…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day