Month: July 2024
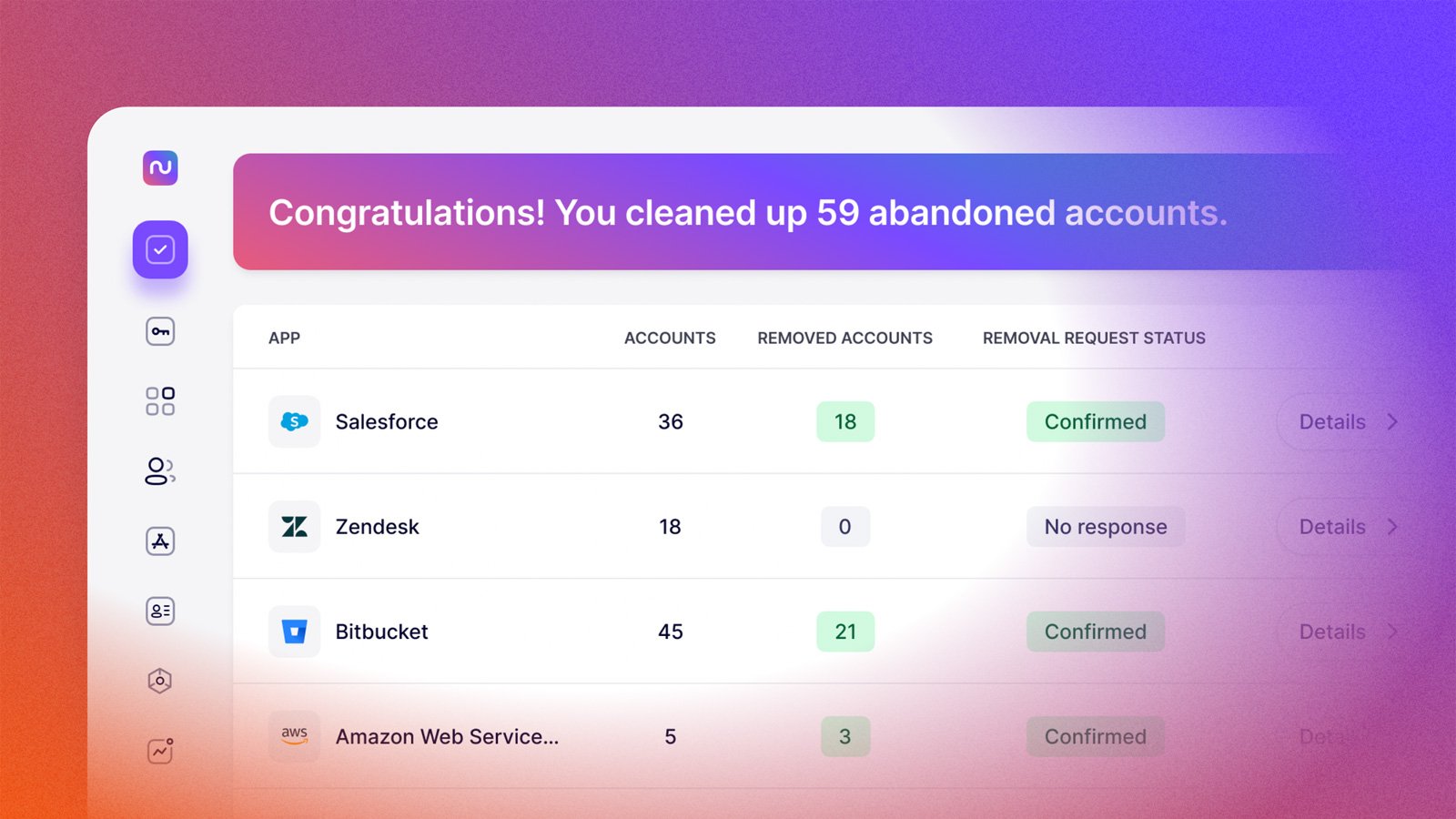
As the landscape of modern work changes, with its distributed teams and quickly evolving cloud-based technologies, maintaining access controls is an increasingly Sisyphean task. The process of achieving and maintaining IT compliance certifications is the perfect microcosm of this challenge: The work involved in identifying and designating assets as “in scope” for each regulation has…
Read MoreMarineMax, self-described as the world’s largest recreational boat and yacht retailer, is notifying over 123,000 individuals whose personal information was stolen in a March security breach claimed by the Rhysida ransomware gang. The company operates over 130 locations, including 83 dealerships and 66 marinas and storage facilities worldwide. Last year, it reported $2.39 billion in revenue…
Read MoreMarineMax, self-described as the world’s largest recreational boat and yacht retailer, is notifying over 123,000 individuals whose personal information was stolen in a March security breach claimed by the Rhysida ransomware gang. The company operates over 130 locations, including 83 dealerships and 66 marinas and storage facilities worldwide. Last year, it reported $2.39 billion in revenue…
Read More‘You want AI to understand the conditions of the data and to act according to the data they provide. So this creates a big opportunity for connecting existing data platforms into AI systems and serving them with all the permission sets and all that. That’s the premise of the data intelligence service that we are…
Read MoreWhile blue teams defend, red teams attack. They share a common goal, however – help identify and address gaps in organizations’ defenses before these weaknesses can be exploited by malicious actors. The blue/red team exercises provide invaluable insights across the technical, procedural and human sides of security and can ultimately help organizations fend off actual…
Read More“Most SaaS providers don’t provide multi-tenant data protection and choose to rely on data at rest encryption for all of their customers’ data,” Ho explained. “They have avoided this highly effective security control because of the overhead of implementing the code changes to encrypt data for each of their customers separately and the complexity of…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-081 DATE(S) ISSUED: 07/17/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated…
Read MoreThe financially motivated threat actor known as FIN7 has been observed using multiple pseudonyms across several underground forums to likely advertise a tool known to be used by ransomware groups like Black Basta. “AvNeutralizer (aka AuKill), a highly specialized tool developed by FIN7 to tamper with security solutions, has been marketed in the criminal underground…
Read MoreJul 17, 2024The Hacker NewsInsider Threats / Cybersecurity Attacks on your network are often meticulously planned operations launched by sophisticated threats. Sometimes your technical fortifications provide a formidable challenge, and the attack requires assistance from the inside to succeed. For example, in 2022, the FBI issued a warning1 that SIM swap attacks are growing: gain…
Read More“Internet Explorer (IE) has officially ended support on June 15, 2022,” the researchers explain. “Additionally, IE has been officially disabled through later versions of Windows 10, including all versions of Windows 11. Disabled, however, does not mean IE was removed from the system. The remnants of IE exist on the modern Windows system, though it…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day