Month: July 2024
A large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the Summer Olympics in Paris. The operation offers fake tickets to the Olympic Games and appears to take advantage of other major sports and music events. Researchers analyzing the campaign are calling it Ticket Heist and…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/digital-forensics-in-the-age-of-cryptocurrency-investigating-blockchain-and-crypto-crimes” on this server. Reference #18.e6d7ce17.1720605955.746b0c73 https://errors.edgesuite.net/18.e6d7ce17.1720605955.746b0c73 Source link lol
Read MoreJul 10, 2024NewsroomOnline Scam / Blockchain Cryptocurrency analysts have shed light on an online marketplace called HuiOne Guarantee that’s widely used by cybercriminals in Southeast Asia, particularly those linked to pig butchering scams. “Merchants on the platform offer technology, data, and money laundering services, and have engaged in transactions totaling at least $11 billion,” Elliptic…
Read MoreScams Scammers gonna scam scam scam, so before hunting for your tickets to a Taylor Swift gig or other in-demand events, learn how to stop fraudsters from leaving a blank space in your bank account 09 Jul 2024 • , 5 min. read Thanks to advances in technology, buying tickets to your favorite show has…
Read MoreDespite the SBOM’s conceptual attractiveness as a simple tool for spotting potentially problematic software components, its value is still too limited to be helpful. “What I’m seeing is that SBOM is too nascent for department and agency proactive use,” Rebecca McWhite, cyber supply chain risk management technical Lead at NIST, said during the CISA conference.…
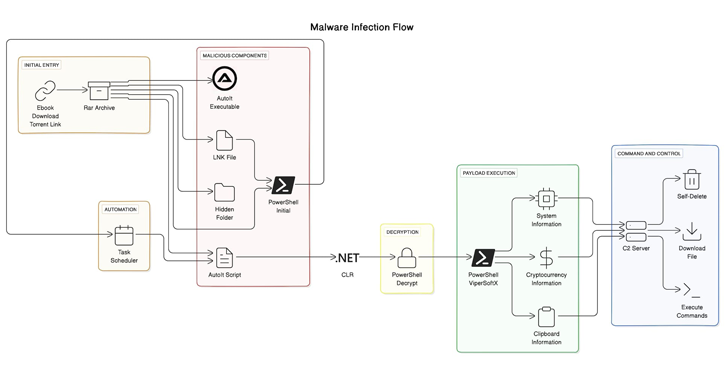
Read MoreJul 10, 2024NewsroomEndpoint Security / Threat Intelligence The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. “A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime (CLR) to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for…
Read MoreHe believes these dual-title roles can provide a more direct reporting line to the CEO or board, which is important for risk reporting. It gives the CISO greater autonomy to report to the board and helps them understand business risk because the CISO is looking across all the different parts of the organization. “It’s not…
Read MoreJul 10, 2024NewsroomVulnerability / Network Security Select versions of the OpenSSH secure networking suite are susceptible to a new vulnerability that can trigger remote code execution (RCE). The vulnerability, tracked as CVE-2024-6409 (CVSS score: 7.0), is distinct from CVE-2024-6387 (aka RegreSSHion) and relates to a case of code execution in the privsep child process due…
Read MoreApply the stable channel update provided by Mozilla to vulnerable systems immediately after appropriate testing. (M1051: Update Software)o Safeguard 7.1 : Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard.o…
Read MoreGartner Magic Quadrant: Cato, Netskope Join Palo Alto Networks As Single-Vendor SASE ‘Leaders’
by nlqip
The second year of Gartner rankings for single-vendor SASE (secure access service edge) featured nine vendors in total. Cato Networks moved up and Netskope appeared for the first time as Gartner released its latest Magic Quadrant ranking of single-vendor SASE vendors — with the two companies joining Palo Alto Networks in the sought-after “leaders” quadrant…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day