Month: July 2024
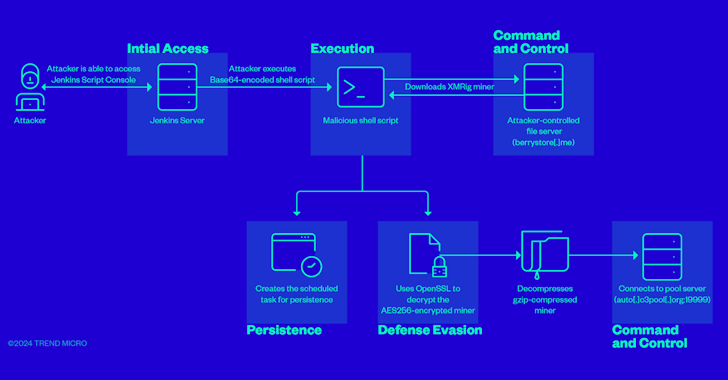
Jul 09, 2024NewsroomCI/CD Security / Server Security Cybersecurity researchers have found that it’s possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. “Misconfigurations such as improperly set up authentication mechanisms expose the ‘/script’ endpoint to attackers,” Trend Micro’s Shubham Singh and Sunil Bharti said in…
Read MoreJul 09, 2024Newsroom Military personnel from Middle East countries are the target of an ongoing surveillanceware operation that delivers an Android data-gathering tool called GuardZoo. The campaign, believed to have commenced as early as October 2019, has been attributed to a Houthi-aligned threat actor based on the application lures, command-and-control (C2) server logs, targeting footprint,…
Read MoreClear Web vs. Deep Web vs. Dark Web Threat intelligence professionals divide the internet into three main components: Clear Web – Web assets that can be viewed through public search engines, including media, blogs, and other pages and sites. Deep Web – Websites and forums that are unindexed by search engines. For example, webmail, online…
Read More“Typically, after successful initial access APT40 focuses on establishing persistence to maintain access on the victim’s environment,” said the advisory. “However, as persistence occurs early in an intrusion, it is more likely to be observed in all intrusions regardless of the extent of compromise or further actions taken.” A concerning trend identified in the advisory…
Read MoreJul 09, 2024NewsroomCyber Espionage / Threat Intelligence Cybersecurity agencies from Australia, Canada, Germany, Japan, New Zealand, South Korea, the U.K., and the U.S. have released a joint advisory about a China-linked cyber espionage group called APT40, warning about its ability to co-opt exploits for newly disclosed security flaws within hours or days of public release.…
Read MorePass the CRISC exam Adhere to the CRISC Code of Professional Ethics Demonstrate the required minimum work experience As noted, CRISC is intended as a relatively high-level cert; as such its holders must demonstrate real-world experience. To be certified, you must have at least three years of work experience performing tasks involved in two of the…
Read More“The State of Fake Traffic 2024,” a report from security tech company CHEQ, shows just how big the problem is getting. According to its research, 17.9% of all observed traffic in 2023 was automated or invalid, a 58% increase from the 11.3% identified as such by CHEQ in the previous year. (Others that count all…
Read MoreJul 09, 2024NewsroomSupply Chain Attack / Web Security Unknown threat actors have been found propagating trojanized versions of jQuery on npm, GitHub, and jsDelivr in what appears to be an instance of a “complex and persistent” supply chain attack. “This attack stands out due to the high variability across packages,” Phylum said in an analysis…
Read MoreThe Case for Tying Executive Compensation to Cybersecurity Performance to Incentivize Strong Cybersecurity Leadership – CnSight.io – Cybersecurity Performance Improvement
by nlqip
Cybersecurity is no longer an optional or peripheral aspect of business operations; it’s an absolute necessity. The increasing frequency and sophistication of cyberattacks have highlighted the critical importance of robust cybersecurity measures. Along with these increases in frequency and sophistication, cyberattacks have also become incredibly expensive, with the average data breach costing millions. To stay…
Read MoreMicrosoft’s recent cloud data leak: What can we learn? – CnSight.io – Cybersecurity Performance Improvement
by nlqip
In the last few days, Microsoft disclosed a data leak that exposed 38 terabytes of company data, including passwords, Teams messages, and the backups of two Microsoft AI research employees’ workstations. Thankfully, Microsoft has confirmed that no customer data was exposed. The leak was caused by an overly permissive Shared Access Signature (SAS) token that…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day