Month: July 2024
Jul 01, 2024NewsroomSupply Chain / Software Security A trio of security flaws has been uncovered in the CocoaPods dependency manager for Swift and Objective-C Cocoa projects that could be exploited to stage software supply chain attacks, putting downstream customers at severe risks. The vulnerabilities allow “any malicious actor to claim ownership over thousands of unclaimed…
Read More‘By combining our best-in-class software with Metrics’ cloud-based simulation as a service, we are excited to bring this groundbreaking technology to our EDA [electric design automation] and semiconductor customers,’ says Altair CEO James Scapa. AI cloud specialist Altair is acquiring Metrics Design Automation in a move to transform the semiconductor market by making top-notch automation…
Read MoreAuvik CEO Doug Murray tells CRN he is aiming to put more muscle behind sales, channel marketing and a go-to-market strategy to grow the channel business — and making it one of the fastest-growing parts of the company is ‘top of mind.’ In the last year, Auvik has seen 45 percent year-over-year growth, which CEO…
Read MoreAdditional customers are now believed to have had their emails viewed in connection with the compromise of Microsoft’s corporate email system by the Midnight Blizzard threat group. Microsoft has reportedly sent out more notifications to customers impacted by the compromise of its corporate email system by Russian threat actor Midnight Blizzard. According to Bloomberg, the…
Read MoreNvidia, Silverfort and Pax8 are among the ISVs to receive Microsoft Partner of the Year awards this year. A chip making giant. An identity protection upstart. And a disruptor to IT distribution. Nvidia, Silverfort and Pax8 are among the independent software vendors (ISVs) to receive Microsoft Partner of the Year awards this year in a…
Read MoreA new OpenSSH unauthenticated remote code execution (RCE) vulnerability dubbed “regreSSHion” gives root privileges on glibc-based Linux systems. OpenSSH is a suite of networking utilities based on the Secure Shell (SSH) protocol. It is extensively used for secure remote login, remote server management and administration, and file transfers via SCP and SFTP. The flaw, discovered by researchers…
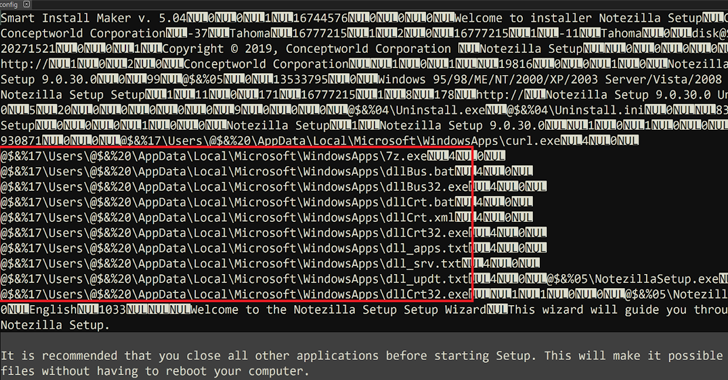
Read MoreJul 01, 2024NewsroomSupply Chain Attack / Threat Intelligence Installers for three different software products developed by an Indian company named Conceptworld have been trojanized to distribute information-stealing malware. The installers correspond to Notezilla, RecentX, and Copywhiz, according to cybersecurity firm Rapid7, which discovered the supply chain compromise on June 18, 2024. The issue has since…
Read MoreJul 01, 2024NewsroomMobile Security / Spyware The threat actor known as Transparent Tribe has continued to unleash malware-laced Android apps as part of a social engineering campaign to target individuals of interest. “These APKs continue the group’s trend of embedding spyware into curated video browsing applications, with a new expansion targeting mobile gamers, weapons enthusiasts,…
Read MoreUnderstanding Data Privacy and Security: How do they Relate? Data privacy and security are critical topics for any business to focus on in today’s environment. The rising costs of cyberattacks and other threats mean a clear strategy for safeguarding sensitive data is more important than ever before. This is something no organization can afford to…
Read MoreJul 01, 2024NewsroomLinux / Vulnerability OpenSSH maintainers have released security updates to contain a critical security flaw that could result in unauthenticated remote code execution with root privileges in glibc-based Linux systems. The vulnerability has been assigned the CVE identifier CVE-2024-6387. It resides in the OpenSSH server component, also known as sshd, which is designed…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA