GenAI is Powering the Latest Surge in Modern Email Threats
by nlqip

Generative artificial intelligence (GenAI) tools like ChatGPT have extensive business value. They can write content, clean up context, mimic writing styles and tone, and more. But what if bad actors abuse these capabilities to create highly convincing, targeted and automated phishing messages at scale?
No need to wonder as it’s already happening. Not long after the launch of ChatGPT, business email compromise (BEC) attacks, which are language-based, increased across the globe. According to the 2024 State of the Phish report from Proofpoint, BEC emails are now more personalized and convincing in multiple countries. In Japan, there was a 35% increase year-over-year for BEC attacks. Meanwhile, in Korea they jumped 31% and in the UAE 29%. It turns out that GenAI boosts productivity for cybercriminals, too. Bad actors are always on the lookout for low-effort, high-return modes of attack. And GenAI checks those boxes. Its speed and scalability enhance social engineering, making it faster and easier for attackers to mine large datasets of actionable data.
As malicious email threats increase in sophistication and frequency, Proofpoint is innovating to stop these attacks before they reach users’ inboxes. In this blog, we’ll take a closer look at GenAI email threats and how Proofpoint semantic analysis can help you stop them.
Why GenAI email threats are so dangerous
Verizon’s 2023 Data Breach Investigations Report notes that three-quarters of data breaches (74%) involve the human element. If you were to analyze the root causes behind online scams, ransomware attacks, credential theft, MFA bypass, and other malicious activities, that number would probably be a lot higher. Cybercriminals also cost organizations over $50 billion in total losses between October 2013 and December 2022 using BEC scams. That represents only a tiny fraction of the social engineering fraud that’s happening.
Email is the number one threat vector, and these findings underscore why. Attackers find great success in using email to target people. As they expand their use of GenAI to power the next generation of email threats, they will no doubt become even better at it.
We’re all used to seeing suspicious messages that have obvious red flags like spelling errors, grammatical mistakes and generic salutations. But with GenAI, the game has changed. Bad actors can ask GenAI to write grammatically perfect messages that mimic someone’s writing style—and do it in multiple languages. That’s why businesses around the globe now see credible malicious email threats coming at their users on a massive scale.
How can these threats be stopped? It all comes down to understanding a message’s intent.
Stop threats before they’re delivered with semantic analysis
Proofpoint has the industry’s first predelivery threat detection engine that uses semantic analysis to understand message intent. Semantic analysis is a process that is used to understand the meaning of words, phrases and sentences within a given context. It aims to extract the underlying meaning and intent from text data.
Proofpoint semantic analysis is powered by a large language model (LLM) engine to stop advanced email threats before they’re delivered to users’ inboxes in both Microsoft 365 and Google Workspace.
It doesn’t matter what words are used or what language the email is written in. And the weaponized payload that’s included in the email (e.g., URL, QR code, attached file or something else) doesn’t matter, either. With Proofpoint semantic analysis, our threat detection engines can understand what a message means and what attackers are trying to achieve.
An overview of how Proofpoint uses semantic analysis.
Proofpoint
How it works
Proofpoint Threat Protection now includes semantic analysis as an extra layer of threat detection. Emails must pass through an ML-based threat detection engine, which analyzes them at a deeper level. And it does this in-line—before emails are delivered to users. Here is a closer look at how it works.
Step 1
The goal of semantic analysis is to extract the underlying meaning and intent from text data. You can use various methods and techniques to achieve this. We choose LLM text embedding for our process.
We fine-tune the model to detect semantics according to a taxonomy that was defined by our threat analysts. This approach allows us to capture semantic similarity so that we can better understand the meaning of the words that are used within emails.
With the LLM-based method for semantic analysis, Proofpoint uses powerful representations learned to better understand and analyze the meaning of text in an email. The ability to capture complex semantic relationships and contextual nuances that are independent of text variations and different languages allows us to excel at text classifications and sentiment analysis.
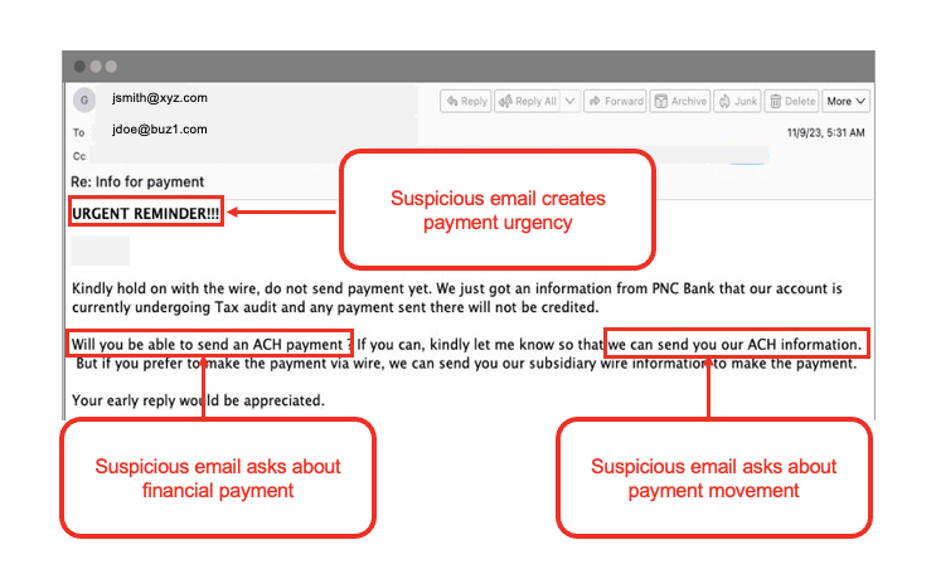
Let’s look at key intent indicators found in the suspicious message below. This message aimed to create urgency and talked about changing payment routing information.
What Proofpoint semantic analysis looks like.
Proofpoint
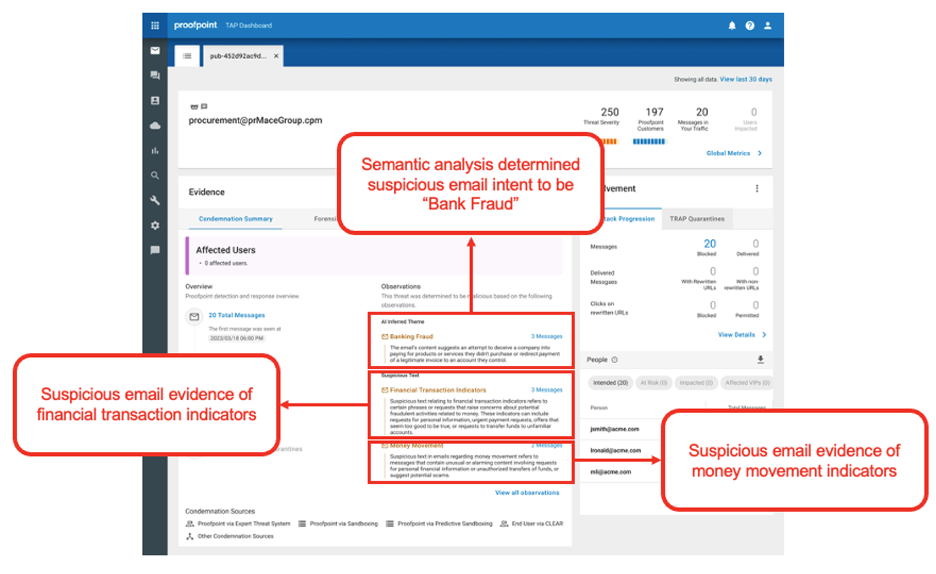
Our semantic analysis determined that “bank fraud” was the intent of this message.
An example of semantic analysis explainability.
Proofpoint
Step 2
Proofpoint uses our behavioral AI detection engine to identify signals and anomalies in key message attributes including:
- Sender
- Receiver
- Headers
- Message traits
- Images
- URL links
- Attachments
- And many more…
With this approach, we can detect and block tens of millions of advanced email threats per month. This includes business email compromise (BEC) scams, telephone-oriented attack delivery (TOAD) attacks and multifactor authentication (MFA) bypass attacks across our 500,000+ customers. And we do this before these emails are delivered to users’ inboxes.
A commitment to continuous innovation
The contemporary email threat landscape is characterized by fragmentation, with a myriad of sophisticated attacks emerging daily. From phishing schemes to ransomware attacks, malicious actors constantly evolve their tactics, exploiting vulnerabilities in email systems and human behavior. To combat these threats, a complete and comprehensive approach is crucial. With a modern approach that provides continuous threat detection and analysis (predelivery to post-delivery to click-time) throughout the email delivery chain, organizations can achieve end-to-end protection even against new threats, like GenAI.
Over the past two decades, Proofpoint has demonstrated that we are committed to innovating when it comes to AI, ML and detection engine technologies. During this time, we have secured more than 250 innovation patents. Simple email security tools rely on a single-layered detection stack to analyze delivered emails. But with our continuous detection stack, Proofpoint out-innovates the market.
Proofpoint Threat Protection features a multilayered detection stack that identifies modern threats with accuracy. We employ a wide array of detection techniques to catch the widest array of threat types. Our broad set of detection technology allows us to apply the right technique to the right threat.
By layering semantic analysis with behavioral AI, Proofpoint provides businesses with high-fidelity detection and efficacy for advanced email threats.
Proofpoint delivers human-centric security
It’s more important than ever for defenders to take a proactive approach toward protecting users from malicious email. Predelivery semantic analysis and behavioral AI detection from Proofpoint can stop malicious emails before they reach users’ inboxes. With a multilayered detection stack approach, your business can detect and analyze malicious messages continuously. That will allow you to better protect your people from even the most sophisticated email threats.
Our new semantic analysis LLM detection engine, which we just announced, is now available to all Proofpoint Threat Protection customers. To learn why 87% of the Fortune 100 trust Proofpoint to protect their people and business, see this solution brief.
Source link
lol
Generative artificial intelligence (GenAI) tools like ChatGPT have extensive business value. They can write content, clean up context, mimic writing styles and tone, and more. But what if bad actors abuse these capabilities to create highly convincing, targeted and automated phishing messages at scale? No need to wonder as it’s already happening. Not long after…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
