Links that Lie: Stop URL- based Attacks Before They Start
by nlqip

The most damaging cyber threats today don’t target machines or systems—they target humans. Today, 74% of data breaches rely on exploiting the human element. From employees clicking on malicious links to being deceived by emails posing as executives and suppliers, human-targeted attacks jeopardize businesses worldwide every day.
When it comes to targeted email threats, Proofpoint has seen attackers pivot away from static file attachments toward malicious links which must be triggered by human clicks to initiate a wider attack. Whether their goal is to launch a phishing attack and steal credentials or direct users to malware-laden websites and unleash ransomware, adversaries now count malicious URLs as one of their favored tactics to further their attacks.
To help organizations stop URL-based attacks before they even start, Proofpoint is introducing the industry’s first pre-delivery suspicious URL hold and sandboxing capability as part of Proofpoint Threat Protection. When combined with our click-time protections, it creates the most formidable set of defense-in-depth measures available for organizations to prevent attacks from reaching their human targets.
URL-based threats: a popular attacker technique
Recent Proofpoint threat intelligence and research data shows that the average number of daily URL-based threats has increased to over 4.5 million. This is an alarming 119% rise over the past three years.
Infographic: 1 in 7 clicks on malicious links happen in 60 seconds of delivery.
Proofpoint
What’s equally concerning is the speed at which these attacks can cause damage. Research from Proofpoint shows that 1 in 7 clicks on an unsafe link happens in less than 60 seconds after an email’s delivery. This rapid click response demonstrates the critical nature of strong pre-delivery protection to reduce risk of users clicking on malicious links.
Enhanced predelivery protection for URL-based threats
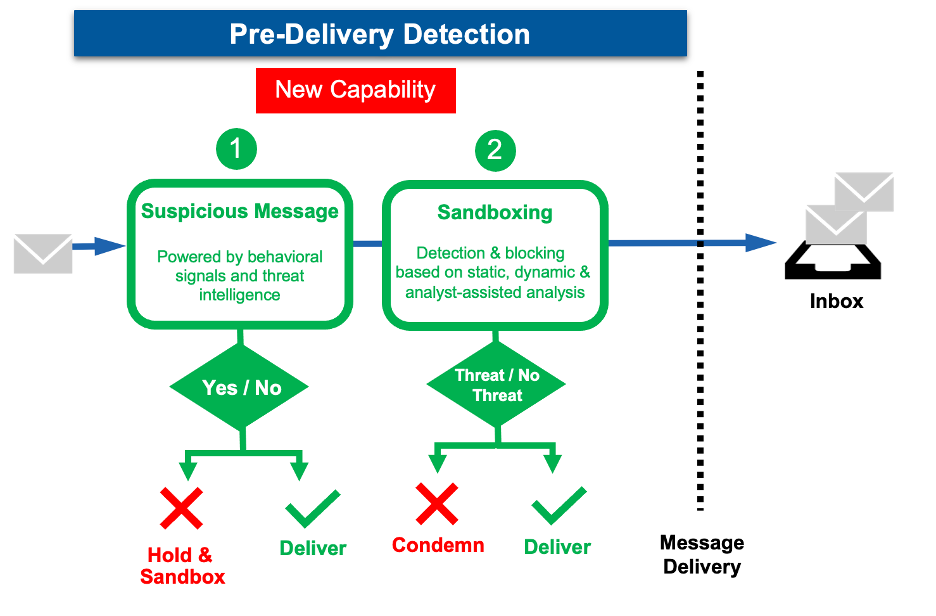
Our new capability allows organizations to hold suspicious messages with URLs for sandbox analysis, minimizing the risk of a user engaging with the malicious URL. We use behavioral signals and threat intelligence to determine if a message should be held for more thorough inspection. Our sandbox technology conducts an exhaustive analysis of the URL using static and dynamic analysis, as well as analyst-assisted execution to maximize detection and intelligence extraction.
Hold and sandbox messages with suspicious URLs stops threats before they reach users.
Proofpoint
Continuous defense with click-time protection
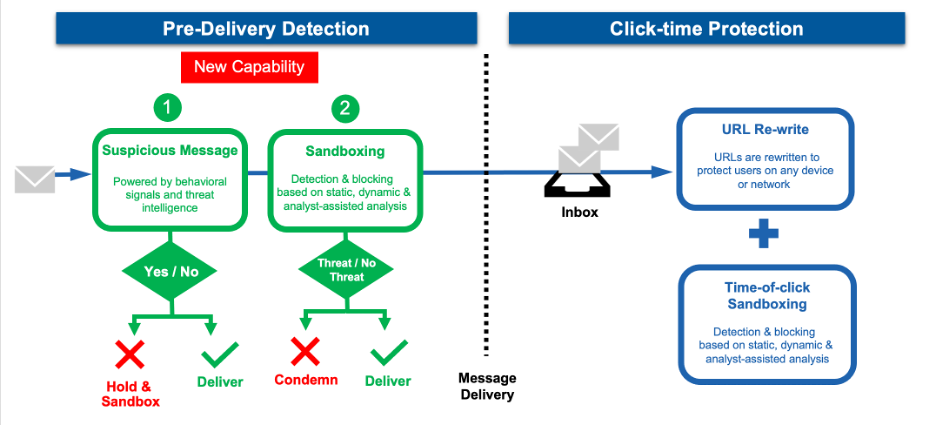
URLs are not always born malicious. They can become weaponized post-delivery. As such, emails containing links require constant scrutiny to protect against advanced threats. That’s why continuous analysis from pre-delivery through to click-time is so important for stopping URL-based attacks. With our new pre-delivery hold & sandbox for suspicious URL capability, Proofpoint uniquely provides the most advanced, end-to-end protection against URL threats.
Proofpoint uniquely delivers continuous defense for URL-based threats.
Proofpoint
Predelivery detection. Proofpoint identifies and blocks attacks before they land in users’ inboxes, eliminating the chance a user may activate them. We’ve enhanced this capability by holding suspicious messages with URLs for sandbox analysis.
Click-time protection. Proofpoint continues to monitor delivered messages for links that may change over time. URLs in delivered messages are re-written and sandboxed at time of click. Customers can also enable isolation for another layer of protection post-delivery.
Learn more
If you want more details about how to build a comprehensive email security strategy for your business, see this guide from Proofpoint. And to gain more insight into the changing threat landscape and the risks for your users, be sure to read our latest State of the Phish report.
Source link
lol
The most damaging cyber threats today don’t target machines or systems—they target humans. Today, 74% of data breaches rely on exploiting the human element. From employees clicking on malicious links to being deceived by emails posing as executives and suppliers, human-targeted attacks jeopardize businesses worldwide every day. When it comes to targeted email threats, Proofpoint…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
