Google fixes ninth Chrome zero-day exploited in attacks this year
by nlqip

Today, Google released a new Chrome emergency security update to patch a zero-day vulnerability tagged as exploited in attacks.
“Google is aware that an exploit for CVE-2024-7971 exists in the wild,” the company said in an advisory published on Wednesday.
This high-severity zero-day vulnerability is caused by a type confusion weakness in Chrome’s V8 JavaScript engine. Security researchers with the Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC) reported it on Monday.
Although such security flaws can commonly enable attackers to trigger browser crashes after data allocated into memory is interpreted as a different type, they can also exploit them for arbitrary code execution on targeted devices running unpatched browsers.
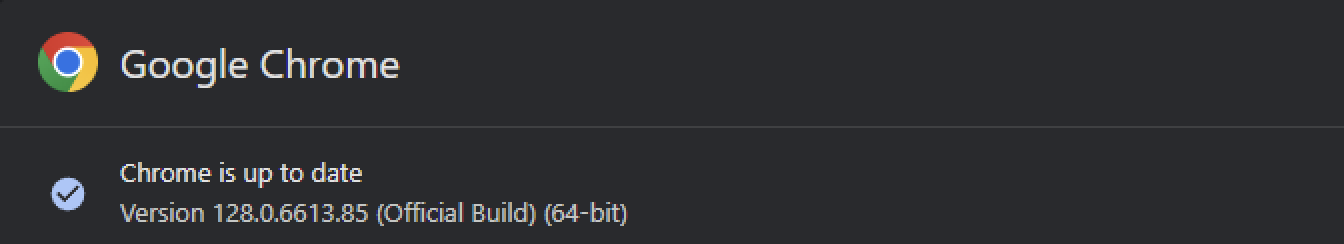
Google has fixed the zero-day with the release of 128.0.6613.84/.85 for Windows/macOS and 128.0.6613.84 (Linux), versions that will roll out to all users in the Stable Desktop channel over the coming weeks.
While Chrome updates automatically when security patches are available, users can also speed up the process by going to the Chrome menu > Help > About Google Chrome, letting the update finish, and clicking the ‘Relaunch’ button to install it.
Today’s update was immediately available when BleepingComputer looked for new updates today.
Even though Google confirmed the CVE-2024-7971 vulnerability was used in attacks, the company has yet to share additional information regarding in-the-wild exploitation.
“Access to bug details and links may be kept restricted until a majority of users are updated with a fix,” Google said.
“We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed.”
CVE-2024-7971 is the ninth Chrome zero-day patched by Google in 2024, either exploited in the wild or at the Pwn2Own hacking contest:
- CVE-2024-0519: A high-severity out-of-bounds memory access weakness within the Chrome V8 JavaScript engine, allowing remote attackers to exploit heap corruption via a specially crafted HTML page, leading to unauthorized access to sensitive information.
- CVE-2024-2887: A high-severity type confusion flaw in the WebAssembly (Wasm) standard. It could lead to remote code execution (RCE) exploits leveraging a crafted HTML page.
- CVE-2024-2886: A use-after-free vulnerability in the WebCodecs API used by web applications to encode and decode audio and video. Remote attackers exploited it to perform arbitrary reads and writes via crafted HTML pages, leading to remote code execution.
- CVE-2024-3159: A high-severity vulnerability caused by an out-of-bounds read in the Chrome V8 JavaScript engine. Remote attackers exploited this flaw using specially crafted HTML pages to access data beyond the allocated memory buffer, resulting in heap corruption that could be leveraged to extract sensitive information.
- CVE-2024-4671: A high-severity use-after-free flaw in the Visuals component that handles the rendering and displaying of content in the browser.
- CVE-2024-4761: An out-of-bounds write problem in Chrome’s V8 JavaScript engine, which is responsible for executing JS code in the application.
- CVE-2024-4947: Type confusion weakness in the Chrome V8 JavaScript engine enabling arbitrary code execution on the target device.
- CVE-2024-5274: A type confusion Chrome’s V8 JavaScript engine that can lead to crashes, data corruption, or arbitrary code execution
Source link
lol
Today, Google released a new Chrome emergency security update to patch a zero-day vulnerability tagged as exploited in attacks. “Google is aware that an exploit for CVE-2024-7971 exists in the wild,” the company said in an advisory published on Wednesday. This high-severity zero-day vulnerability is caused by a type confusion weakness in Chrome’s V8 JavaScript…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
