Greasy Opal’s CAPTCHA solver still serving cybercrime after 16 years
by nlqip

A developer that researchers now track as Greasy Opal, operating as a seemingly legitimate business, has been fueling the cybercrime-as-a-service industry with a tool that bypasses account security solutions and allows bot-led CAPTCHA solving at scale.
Greasy Opal has been active for more nearly two decades and tailors its tools based on customers’ targeting needs. Its software has been used to target governments and various technology companies and services (e.g. Amazon, Apple, Steam, Joomla, Facebook, WhatsApp, Vkontakte).
Among Greasy Opal’s customers is the Vietnam-based cybercrime group known as Storm-1152, who created around 750 million Microsoft accounts to sell to various threat actors, including Scattered Spider.
Savvy developer
Researchers at Arkose Labs, a fraud prevention company offering bot detection solutions, have observed Greasy Opal’s tools being used by various bad actors for years and now provide a glimpse into the actor’s operation.
The actor appears to have created a website to market its CAPTCHA bypass tool on the clear web since at least 2016 but BleepingComputer found that it was already in use in 2008 and capable of breaking Microsoft’s CAPTCHA controls for Hotmail (today’s Outlook) at the time.
Furthermore, the tool, which the actor dubs “the best captcha solver in the world,” has had multiple major iterations and is regularly updated to adapt to new types of CAPTCHAs.
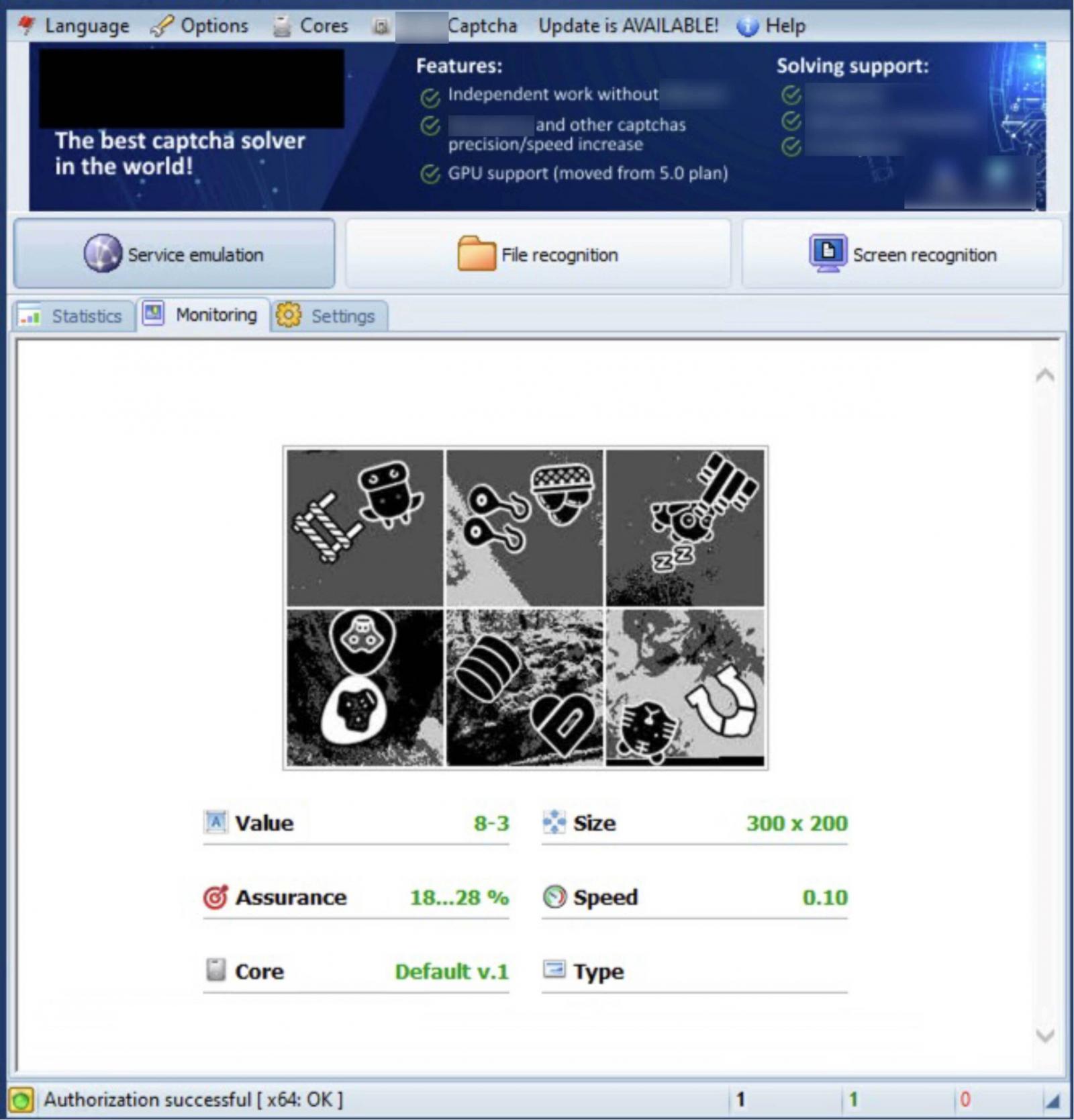
The report from Arkose Labs notes that the tool is very efficient and relies on advanced optical character recognition (OCR) technology combined with machine-learning models “to solve with high accuracy text CAPTCHAs in general and more focused tools for other specific popular text CAPTCHAS.”
Arkose Labs CEO Kevin Gosschalk told BleepingComputer that Greasy Opal likely develops in-house the cutting-edge OCR technology for analyzing and interpreting text-based CAPTCHAs.
Greasy Opal provides two editions for its CAPTCHA solver, a free one that is slower and less accurate, and a paid version that the developer says comes with 90-100% image identification accuracy and can recognize objects in less than a second.
Making money and paying taxes
According to the researchers, the actor’s motivation is purely financial and does not care who its customers are as long as they pay for the product.
“[…] attackers can purchase Greasy Opal’s toolkit for US$70. For an additional US$100 customers can upgrade to get the beta version. Regardless of the version, Greasy Opal requires customers to pay an additional US$10 per month as a subscriber fee” – Arkose Labs
The most expensive package that bundles all the tools costs $190 plus the $10 monthly subscription, a very low price for what they offer, despite the restricted number of installations allowed.
There is also a business edition bundle that costs $300 and permits a slightly higher number of installations. The monthly fee applies for this one, too.
With hundreds of individual attackers using the tools, the researchers estimate that Greasy Opal had a revenue of at least $1.7 million last year.
While not directly involved in attacks, the actor is aware of their tools being used for illegal activities but maintains a legitimate facade by paying taxes for the business.
Per customers’ CAPTCHA needs
Despite the conflicting information on Greasy Opal’s website – which notes in one place that the business started in 2007 and in another the year is 2005, it is certain that some of the tools have a history of nearly 20 years.
Arkose Labs believes that the actor is operating from the Czech Republic, supplying cybercrime-as-a-business (CaaB) operations indiscriminately with tools for spamming, promoting content on social networks, and black SEO, typical tools for pushing content at scale.
After Microsoft disrupted Storm-1152’s activity through seizing several of its domains, Arkose Labs was able to analyze software developed by Greasy Opal and used in attacks.
Although some of the software could be perceived as utilities for marketing purposes, the researchers found that the CAPTCHA solver was developed to target specific organizations.
Some of the targets are public and government services in Russia (State Traffic, Moscow Unified Navigation and Information System, Tax Service, Federal Bailiff, Electronic Passport), Brazil (Secretary of Infrastructure, ), and the U.S. (Dept. of State Bureau of Consular Affairs).
Among the more prominent entities in the tech sector that Greasy Opal’s CAPTCHA solver focused on are Amazon, Apple, Steam, Joomla, Facebook, WhatsApp, GMX, Vkontakte, Yandex, World of Tanks.
Gosschalk described Greasy Opal as being a “very intelligent, low ethics” developer of software that is only interested in making money.
Even if not carrying out the attacks, Greasy Opal’s role in the cybercriminal supply chain is significant as it knowingly enables low-skill threat actors to automate massive attacks against businesses all over the world.
Source link
lol
A developer that researchers now track as Greasy Opal, operating as a seemingly legitimate business, has been fueling the cybercrime-as-a-service industry with a tool that bypasses account security solutions and allows bot-led CAPTCHA solving at scale. Greasy Opal has been active for more nearly two decades and tailors its tools based on customers’ targeting needs.…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
