Hackers now use AppDomain Injection to drop CobaltStrike beacons
by nlqip
A wave of attacks that started in July 2024 rely on a less common technique called AppDomain Manager Injection, which can weaponize any Microsoft .NET application on Windows.
The technique has been around since 2017, and multiple proof-of-concept apps have been released over the years. However, it is typically used in red team engagements and seldomly observed in malicious attacks, with defenders not actively monitoring it.
The Japanese division of NTT has tracked attacks that end with deploying a CobaltStrike beacon that targeted government agencies in Taiwan, the military in the Philippines, and energy organizations in Vietnam.
Tactics, techniques, and procedures, and infrastructural overlaps with recent AhnLab reports and other sources, suggest that the Chinese state-sponsored threat group APT 41 is behind the attacks, although this attribution has low confidence.
AppDomain Manager Injection
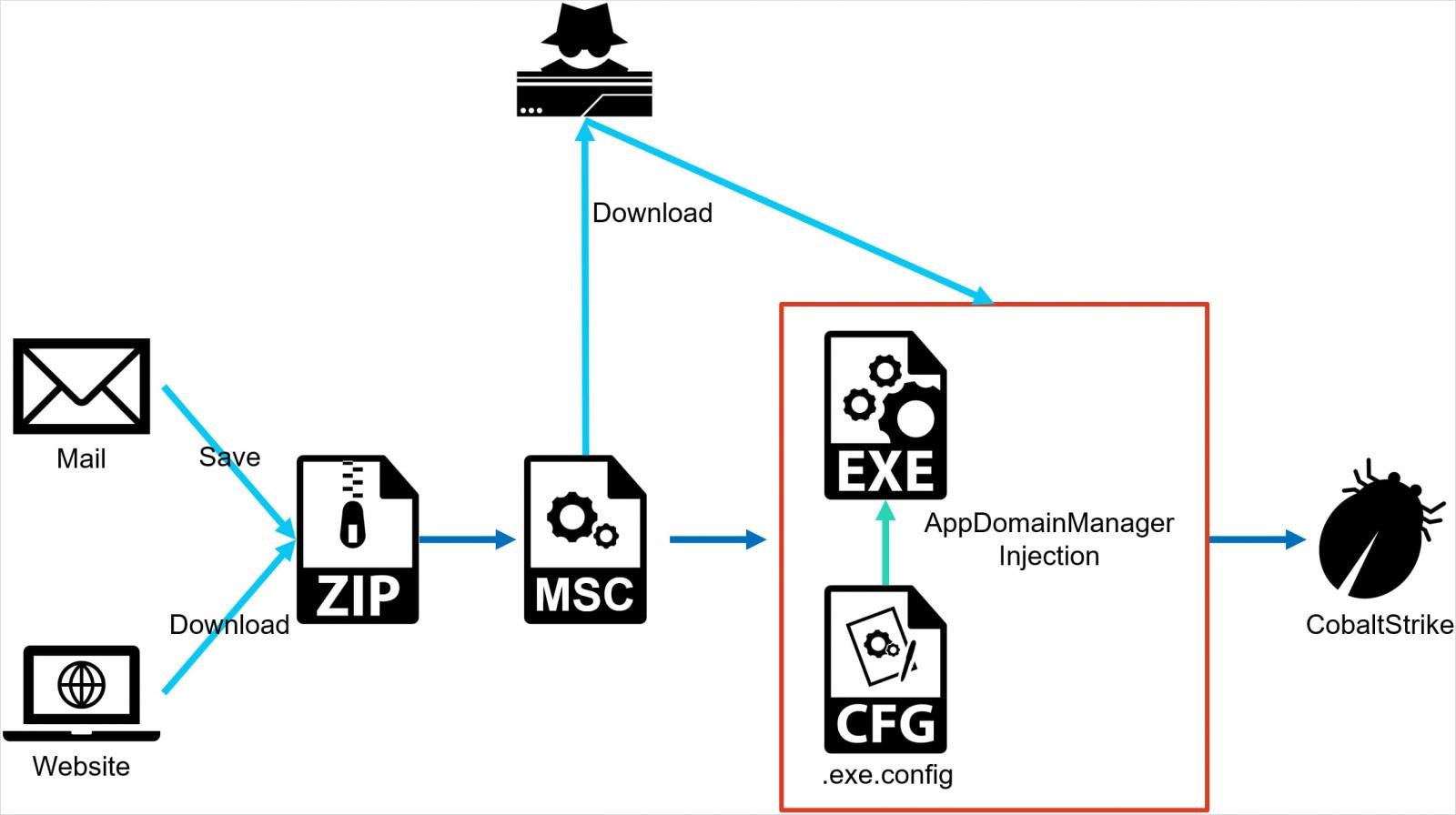
Similar to standard DLL side-loading, AppDomainManager Injection also involves the use of DLL files to achieve malicious goals on breached systems.
However, AppDomainManager Injection leverages .NET Framework’s AppDomainManager class to inject and execute malicious code, making it stealthier and more versatile.
The attacker prepares a malicious DLL that contains a class inheriting from the AppDomainManager class and a configuration file (exe.config) that redirects the loading of a legitimate assembly to the malicious DLL.
The attacker only needs to place the malicious DLL and config file in the same directory as the target executable, without needing to match the name of an existing DLL, like in DLL side-loading.
When the .NET application runs, the malicious DLL is loaded, and its code is executed within the context of the legitimate application.
Unlike DLL side-loading, which can be more easily detected by security software, AppDomainManager injection is harder to detect because the malicious behavior appears to come from a legitimate, signed executable file.
GrimResource attacks
The attacks NTT observed start with the delivery of a ZIP archive to the target that contains a malicious MSC (Microsoft Script Component) file.
When the target opens the file, malicious code is executed immediately without further user interaction or clicks, using a technique called GrimResource, described in detail by Elastic’s security team in June.
GrimResource is a novel attack technique that exploits a cross-site scripting (XSS) vulnerability in the apds.dll library of Windows to execute arbitrary code through Microsoft Management Console (MMC) using specially crafted MSC files.
The technique allows attackers to execute malicious JavaScript, which in turn can run .NET code using the DotNetToJScript method.
The MSC file in the latest attacks seen by NTT creates an exe.config file in the same directory as a legitimate, signed Microsoft executable file (e.g. oncesvc.exe).
This configuration file redirects the loading of certain assemblies to a malicious DLL, which contains a class inheriting from the .NET Framework’s AppDomainManager class and is loaded instead of the legitimate assembly.
Ultimately, this DLL executes malicious code within the context of the legitimate and signed Microsoft executable, completely evading detection and bypassing security measures.
Source: NTT
The final stage of the attack is loading a CobaltStrike beacon on the machine, which the attacker may use to perform a broad range of malicious actions, including introducing additional payloads and lateral movement.
Although it’s not certain that APT41 is responsible for the attacks, the combination of the AppDomainManager Injection and GrimResource techniques indicates that the attackers have the technical expertise to mix novel and less-known techniques in practical cases.
Source link
lol
A wave of attacks that started in July 2024 rely on a less common technique called AppDomain Manager Injection, which can weaponize any Microsoft .NET application on Windows. The technique has been around since 2017, and multiple proof-of-concept apps have been released over the years. However, it is typically used in red team engagements and seldomly observed in…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
