US Marshals Service disputes ransomware gang’s breach claims
by nlqip

The U.S. Marshals Service (USMS) denies its systems were breached by the Hunters International ransomware gang after being listed as a new victim on the cybercrime group’s leak site on Monday.
“USMS is aware of the allegations and has evaluated the materials posted by individuals on the dark web, which do not appear to derive from any new or undisclosed incident,” a spokesperson told BleepingComputer when asked to confirm the cybercrime group’s claims.
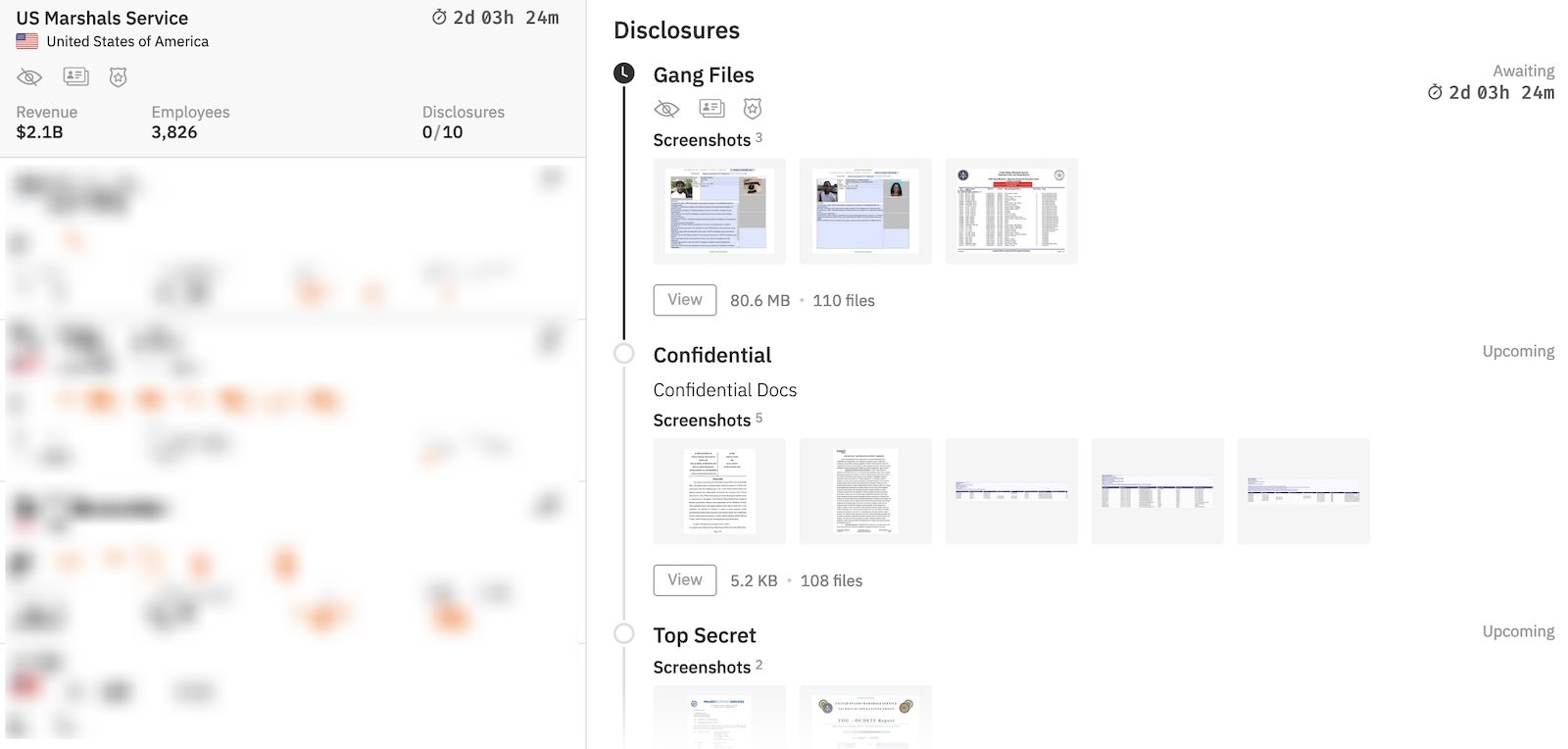
While the ransomware group has not yet released any allegedly stolen documents, they have already included thumbnail screenshots of some of those files in the USMS entry as evidence to support their claims.
Even though the federal law enforcement agency didn’t provide additional information, BleepingComputer has learned that the data published by Hunters International on their dark web data leak site is the same as the data put up for sale in March 2023 on a Russian-speaking hacking forum.
A threat actor named “Tronic” claimed in 2023 that the stolen files contained copies of passports and identification documents, aerial footage and photos of military bases and other high-security areas, details on wiretapping and surveillance of citizens, information on convicts, gang leaders, and cartels, and some files are marked as SECRET or TOP SECRET.
It is unclear if the original seller, Tronic, is now associated with Hunters International or if the ransomware gang previously purchased the data and is now trying to resell it.
One month earlier, in February 2023, the USMS confirmed it was investigating the theft of sensitive law enforcement information after “a stand-alone USMS system” was impacted in a ransomware attack.
“The affected system contains law enforcement sensitive information, including returns from legal process, administrative information, and personally identifiable information pertaining to subjects of USMS investigations, third parties, and certain USMS employees,” USMS spokesperson Drew Wade said at the time.
USMS disclosed another data breach in May 2020 after it accidentally exposed the details of over 387,000 former and current inmates in a December 2019 incident, including personally identifiable information like their names, dates of birth, home addresses, and social security numbers.
Hunters International, the cybercrime gang that listed USMS as a new victim on their leak site this week, is a ransomware operation that surfaced in late 2023 and was flagged as a possible rebrand of Hive because of code similarities.
Notable victims claimed by this ransomware gang over the last year include Japanese optics giant Hoya, U.S. Navy contractor Austal USA, and Integris Health.
The gang also breached the Fred Hutch Cancer Center in December, threatening to leak the stolen data of over 800,000 cancer patients (including their names, Social Security numbers, phone numbers, medical history, lab results, and insurance history) if they weren’t paid.
So far, Hunters International operators have targeted companies of all sizes, with ransom demands seen by BleepingComputer ranging between hundreds of thousands to millions of dollars, depending on the targeted organization’s size.
Since the start of the year, they’ve claimed 157 attacks against various organizations worldwide (including USMS), ranking it as one of the most active ransomware operations.
Source link
lol
The U.S. Marshals Service (USMS) denies its systems were breached by the Hunters International ransomware gang after being listed as a new victim on the cybercrime group’s leak site on Monday. “USMS is aware of the allegations and has evaluated the materials posted by individuals on the dark web, which do not appear to derive…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
