South Korean hackers exploited WPS Office zero-day to deploy malware
by nlqip

The South Korea-aligned cyberespionage group APT-C-60 has been leveraging a zero-day code execution vulnerability in the Windows version of WPS Office to install the SpyGlace backdoor on East Asian targets.
WPS Office is a productivity suite developed by the Chinese firm Kingsoft that is popular in Asia. Reportedly, it has over 500 million active users worldwide.
The zero-day flaw, tracked as CVE-2024-7262, has been leveraged in attacks in the wild since at least late February 2024, but impacts versions from 12.2.0.13110 (August 2023) to 12.1.0.16412 (March 2024).
Kingsoft “silently” patched the problem in March this year without informing the customers that the flaw was actively exploited, prompting ESET, who discovered the campaign and vulnerability, to publish a detailed report today.
In addition to CVE-2024-7262, ESET’s investigation unveiled a second severe flaw, tracked as CVE-2024-7263, which Kingsoft patched in late May 2024 with version 12.2.0.17119.
APT-C-60 exploitation
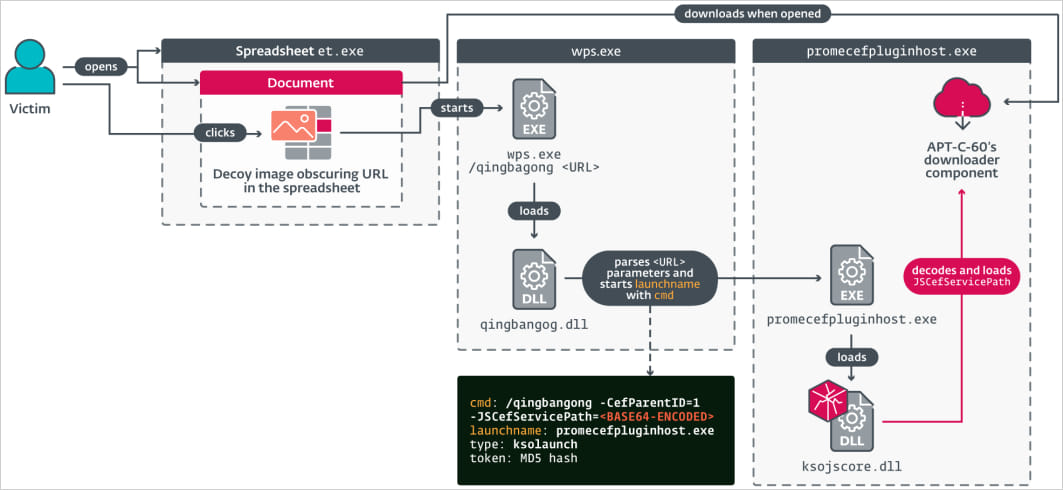
CVE-2024-7262 resides in how the software handles custom protocol handlers, specifically ‘ksoqing://,’ which allows the execution of external applications through specially crafted URLs within documents.
Due to improper validation and sanitization of these URLs, the flaw allows attackers to craft malicious hyperlinks that lead to arbitrary code execution.
APT-C-60 created spreadsheet documents (MHTML files) where they embedded malicious hyperlinks hidden under a decoy image to trick the victim into clicking them, triggering the exploit.
The processed URL parameters include a base64-encoded command to execute a specific plugin (promecefpluginhost.exe) that attempts to load a malicious DLL (ksojscore.dll) containing the attacker’s code.
This DLL is APT-C-60’s downloader component, designed for fetching the final payload (TaskControler.dll) from the attacker’s server, a custom backdoor named ‘SpyGlace.’
Source: ESET
SpyGlace is a backdoor previously analyzed by Threatbook when APT-C-60 used it in attacks on human resources and trade-related organizations.
Bad patch leaves gap
While investigating APT-C-60’s attacks, ESET’s researchers discovered CVE-2024-7263, a second arbitrary code execution flaw impacting WPS Office, which emerged as an incomplete patch of CVE-2024-7262.
Specifically, Kingsoft’s initial attempt to address the problem added validation on specific parameters. However, some, like the ‘CefPluginPathU8,’ were still not adequately secured, allowing attackers to point to paths of malicious DLLs through promecefpluginhost.exe again.
ESET explains that this vulnerability can be exploited locally or through a network share, where the malicious DLL could be hosted.
Despite this possibility, the researchers did not observe APT-C-60 or any other actors leveraging the flaw in the wild. However, given enough time, it’s not unlikely they would have discovered the security gap left by Kingsoft’s bad patch.
Users of WPS Office are recommended to move to the latest release as soon as possible, or at least 12.2.0.17119, to address both code execution flaws.
“The exploit is cunning as it is deceptive enough to trick any user into clicking on a legitimate-looking spreadsheet while also being very effective and reliable,” warns ESET in the report.
“The choice of the MHTML file format allowed the attackers to turn a code execution vulnerability into a remote one.”
Check this GitHub repository for a complete list of indicators of compromise (IoCs) associated with the APT-C-60 activity.
Source link
lol
The South Korea-aligned cyberespionage group APT-C-60 has been leveraging a zero-day code execution vulnerability in the Windows version of WPS Office to install the SpyGlace backdoor on East Asian targets. WPS Office is a productivity suite developed by the Chinese firm Kingsoft that is popular in Asia. Reportedly, it has over 500 million active users…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
