Month: August 2024
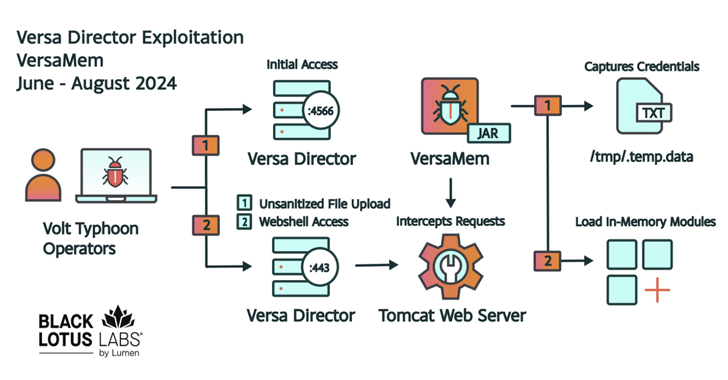
The China-nexus cyber espionage group tracked as Volt Typhoon has been attributed with moderate confidence to the zero-day exploitation of a recently disclosed high-severity security flaw impacting Versa Director. The attacks targeted four U.S. victims and one non-U.S. victim in the Internet service provider (ISP), managed service provider (MSP) and information technology (IT) sectors as…
Read MoreThe Chinese state-backed hacking group Volt Typhoon is behind attacks that exploited a zero-day flaw in Versa Director to upload a custom webshell to steal credentials and breach corporate networks. Versa Director is a management platform ISPs and MSPs use to manage virtual WAN connections created using SD-WAN services. The vulnerability is tracked as CVE-2024-39717…
Read MoreHackers relentlessly probe your organization’s digital defenses, hunting for the slightest vulnerability to exploit. And while penetration testing serves as a valuable tool, there might be some areas of risk your testing program is overlooking. The harsh reality is that even the most security-conscious organizations often have blind spots, with portions of their internet-exposed attack…
Read MoreA massive QR code phishing campaign abused Microsoft Sway, a cloud-based tool for creating online presentations, to host landing pages to trick Microsoft 365 users into handing over their credentials. The attacks were spotted by Netskope Threat Labs in July 2024 after detecting a dramatic 2,000-fold increase in attacks exploiting Microsoft Sway to host phishing…
Read MoreThe cloud, artificial intelligence (AI), machine learning and other technological breakthroughs are radically changing the modern work environment. New assets and services offer increased flexibility, growth potential and access to more resources. However, they also introduce new security risks. Managing vulnerabilities across this ever-expanding threat landscape requires a risk-based approach beyond point solutions and reactive…
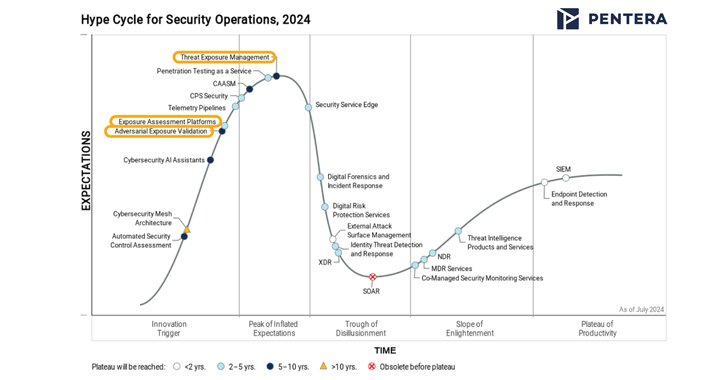
Read MoreWant to know what’s the latest and greatest in SecOps for 2024? Gartner’s recently released Hype Cycle for Security Operations report takes important steps to organize and mature the domain of Continuous Threat Exposure Management, aka CTEM. Three categories within this domain are included in this year’s report: Threat Exposure Management, Exposure Assessment Platforms (EAP),…
Read MoreMedia Room
by nlqip
https://www.iotinsider.com/podcast/iot-unplugged-s3e7-establishing-priorities-f… Source link lol
Read More‘Our vision is to build technology that supports MSPs throughout the entire insurance process, from software consumption to policy acquisition,” says Cole Knuth, FifthWall CEO. ‘We want to maintain the MSPs’ role as technical advisors and provide them with tools that enhance their ability to manage cybersecurity for their clients.’ To prepare for its next…
Read More$200 Million Cybersecurity E-Rate Funding Available for K-12 Schools and Libraries through FCC Cybersecurity Pilot Program
by nlqip
Empowering K-12 schools and libraries to strengthen their cybersecurity posture with new funding opportunities and best practices. Recent attacks reveal that K-12 schools and libraries are prime targets for cyber actors. Ransomware attacks have had dire consequences and highlighted the need for such institutions to strengthen their cybersecurity posture and reduce risk. Increased attacks against…
Read MoreEyes are on Salesforce to “reverse those challenging results from 1Q25,” according to a KeyBanc report. Salesforce Data Cloud performance. Artificial intelligence investments. And a partnership with rival Workday. These are some of the main subjects expected to come up Wednesday when Salesforce reveals its performance for the fiscal 2025 second quarter ended July 31.…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm