Month: August 2024
Reports suggest that well-known cybersecurity vendors including Tenable, eSentire and Trend Micro are seeking to be acquired. Buyers Wanted The list of major cybersecurity vendors that are reportedly pursuing an acquisition by private equity investors—or are facing pressure to do so—is continuing to grow. Following recent reports that top security vendors including Tenable and Trend…
Read MoreCISA has added four new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
Read MoreAccording to user reports following this month’s Patch Tuesday, the August 2024 Windows security updates are breaking dual boot on some Linux systems with Secure Boot enabled. This issue is caused by Microsoft’s decision to apply a Secure Boot Advanced Targeting (SBAT) update to block Linux boot loaders unpatched against the CVE-2022-2601 GRUB2 Secure Boot…
Read MorePhrack #71 has been released online and is available to read for free. This issue is the first to be released since 2021, marking a new chapter in the influential online magazine’s history. Phrack is an underground online magazine first launched in 1985 as a text file distributed through Bulletin Board Systems (BBS) and later…
Read MoreWelcome to this week’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. At Canary Trap, it is our mission to keep you up-to-date with the most crucial news in the world of cybersecurity and this bi-weekly publication is your gateway to the latest news. This week’s newsletter covers a range of critical cybersecurity issues,…
Read MoreA critical vulnerability affecting multiple versions of GitHub Enterprise Server could be exploited to bypass authentication and enable an attacker to gain administrator privileges on the machine. The security issue is identified as CVE-2024-6800 and received a 9.5 severity rating as per the CVSS 4.0 standard. It is described as an XML signature wrapping problem that occurs…
Read MoreStory of an Undercover CIA Agent who Penetrated Al Qaeda Rolling Stone has a long investigative story (non-paywalled version here) about a CIA agent who spent years posing as an Islamic radical. Unrelated, but also in the “real life spies” file: a fake Sudanese diving resort run by Mossad. Tags: al Qaeda, CIA, espionage, undercover…
Read MoreHours after the CSO exclusive on the potential deal went live, several users submitted their disapproval on Reddit. One wrote, “Oh god I hope not. Action1 is my personal RMM (remote monitoring and management) at this point”, while user another said, “This would be a great acquisition for CS, but will probably suck for a…
Read MoreAug 21, 2024Ravie LakshmananMalware / Cryptocurrency Cybersecurity researchers have uncovered a new macOS malware strain dubbed TodoSwift that they say exhibits commonalities with known malicious software used by North Korean hacking groups. “This application shares several behaviors with malware we’ve seen that originated in North Korea (DPRK) — specifically the threat actor known as BlueNoroff…
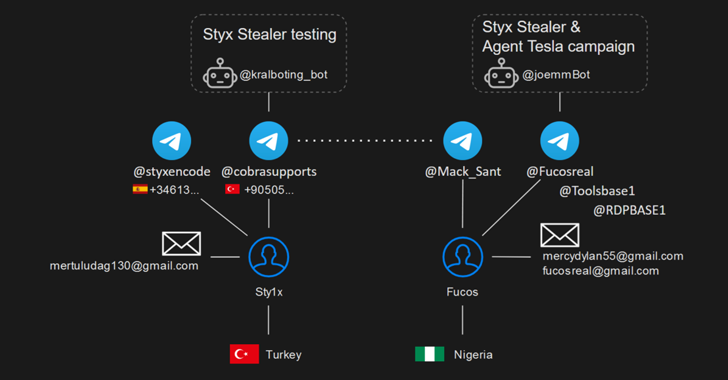
Read MoreAug 21, 2024Ravie LakshmananCyber Espionage / Threat Intelligence In what’s a case of an operational security (OPSEC) lapse, the operator behind a new information stealer called Styx Stealer leaked data from their own computer, including details related to the clients, profit information, nicknames, phone numbers, and email addresses. Styx Stealer, a derivative of the Phemedrone…
Read MoreRecent Posts
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm
- Seven Trends to Watch for in 2025
- Multiple Vulnerabilities in Ivanti Products Could Allow for Remote Code Execution
- Ivanti Releases Security Updates for Connect Secure, Policy Secure, and ZTA Gateways | CISA
- CISA Adds One Vulnerability to the KEV Catalog | CISA