Month: August 2024
It’s no great revelation to say that SaaS applications have changed the way we operate, both in our personal and professional lives. We routinely rely on cloud-based and remote applications to conduct our basic functions, with the result that the only true perimeter of our networks has become the identities with which we log into…
Read MoreSemiconductor firms are appealing targets due to the high value of their intellectual property (IP), sensitive manufacturing processes, and their critical role in global supply chains. The complexity and precision involved in chip manufacturing mean that any disruption — whether through data theft, ransomware, or system sabotage — can have far-reaching consequences, impacting not just…
Read More“Let’s say someone is using those providers and they happen to have a common identity platform, maybe SailPoint. If SailPoint is passing a data stream to AWS and Microsoft and maybe others, it could permit access to all that client’s information in one of those hyperscaler environments. It might allow limited data access in the…
Read MoreOther than scanning huge amounts of data for potential threats, the technology comes in handy at sniffing out anomalies. By analyzing patterns and behaviors, GenAI can pinpoint suspicious activities, an ability well realized by Darktrace, a cybersecurity company that uses GenAI to understand normal network behavior and identify deviations. “GenAI can efficiently handle many tasks…
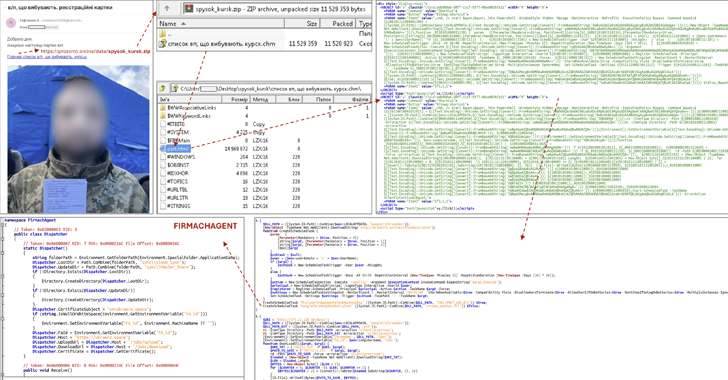
Read MoreAug 21, 2024Ravie LakshmananCyber Warfare / Threat Intelligence The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of new phishing attacks that aim to infect devices with malware. The activity has been attributed to a threat cluster it tracks as UAC-0020, which is also known as Vermin. The exact scale and scope of the…
Read MoreLouis Blackburn, operations director at global ethical hacker and red team cybersecurity solutions provider CovertSwarm, commented: “In order to combat this [RMM abuse] tactic, organizations need to focus on endpoint hardening and reducing their attack surface.” “Implementing application control measures, such as Windows Defender Application Control (WDAC) or AppLocker, will act as a primary line…
Read MoreAug 21, 2024Ravie LakshmananWordPress / Cybersecurity A maximum-severity security flaw has been disclosed in the WordPress GiveWP donation and fundraising plugin that exposes more than 100,000 websites to remote code execution attacks. The flaw, tracked as CVE-2024-5932 (CVSS score: 10.0), impacts all versions of the plugin prior to version 3.14.2, which was released on August…
Read MoreToyota confirmed that customer data was exposed in a third-party data breach after a threat actor leaked an archive of 240GB of stolen data on a hacking forum. “We are aware of the situation. The issue is limited in scope and is not a system wide issue,” Toyota told BleepingComputer when asked to validate the…
Read MoreThe Cannon Corporation dba CannonDesign is sending notices of a data breach to more than 13,000 of its clients, informing that hackers breached and stole data from its network in an attack in early 2023. CannonDesign is a multi-awarded architectural, engineering, and consulting firm based in the United States, recognized for its work on high-profile projects such…
Read More‘Sadly, we have made the very difficult decision to say painful goodbyes to some of our team members,’ Five9 CEO Mike Burkland said in an email to employees. Five9 has revealed plans to lay off about 7 percent of its workforce, totaling less than 200 people based on the vendor’s 2,684 full-time employee count as…
Read MoreRecent Posts
- Seven Trends to Watch for in 2025
- Multiple Vulnerabilities in Ivanti Products Could Allow for Remote Code Execution
- Ivanti Releases Security Updates for Connect Secure, Policy Secure, and ZTA Gateways | CISA
- CISA Adds One Vulnerability to the KEV Catalog | CISA
- CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild