Month: August 2024
Cybersecurity Snapshot: Schools Suffer Heavy Downtime Losses Due To Ransomware, as Banks Grapple with AI Challenges
by nlqip
The cost of ransomware downtime in schools gets pegged at $500K-plus per day. Meanwhile, check out the AI-usage risks threatening banks’ cyber resilience. Plus, Uncle Sam is warning about a dangerous Iran-backed hacking group. And get the latest on AI-system inventories, the APT29 nation-state attacker and digital identity security! Dive into six things that are…
Read More“ERR_SSL_BAD_RECORD_MAC_ALERT” error generally occurs when your web server and browser have differing views concerning security levels. As a result, the server sends out an incorrectly encrypted message. This blog explains what causes the ERR_SSL_BAD_RECORD_MAC_ALERT. Also, get troubleshooting tips that can help resolve the issue easily. Let’s begin! What is ERR_SSL_BAD_Record_MAC_Alert Error? ERR_SSL_BAD_RECORD_MAC_ALERT is a client-side…
Read MoreAug 30, 2024Ravie LakshmananCyber Threat / Cyber Espionage Cybersecurity researchers have unearthed new network infrastructure set up by Iranian threat actors to support activities linked to the recent targeting of U.S. political campaigns. Recorded Future’s Insikt Group has linked the infrastructure to a threat it tracks as GreenCharlie, an Iran-nexus cyber threat group that overlaps…
Read MoreIncidentally, the FBI and CISA have released a joint advisory on the Ransomhub Ransomware variant, calling it a formidable service model attracting high-profile affiliates from other prominent variants such as LockBit and ALPHV. “Since its inception in February 2024, RansomHub has encrypted and exfiltrated data from at least 210 victims representing the water and wastewater,…
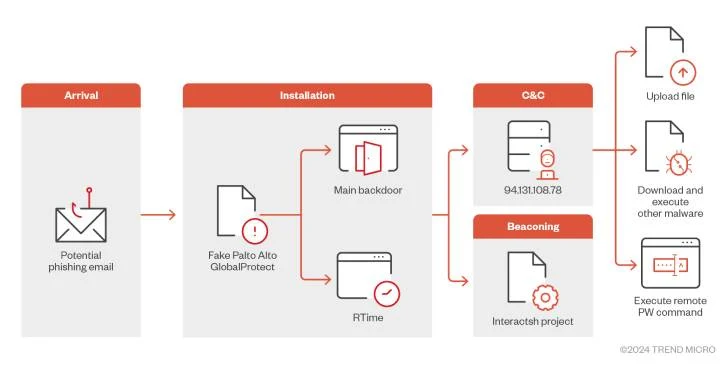
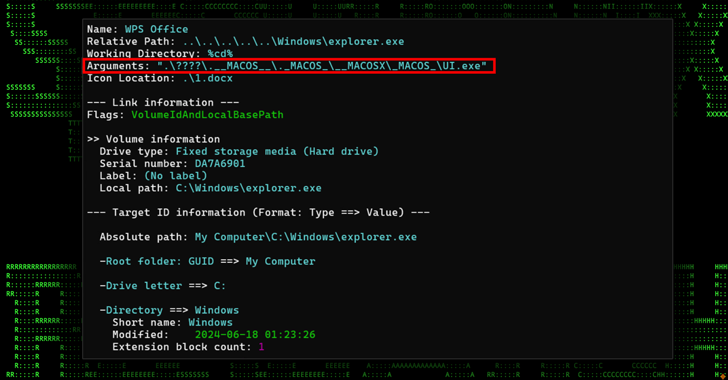
Read MoreAug 30, 2024Ravie LakshmananMalware / Network Security Cybersecurity researchers have disclosed a new campaign that potentially targets users in the Middle East through malware that disguises itself as Palo Alto Networks GlobalProtect virtual private network (VPN) tool. “The malware can execute remote PowerShell commands, download and exfiltrate files, encrypt communications, and bypass sandbox solutions, representing…
Read MoreThe most dangerous vulnerability you’ve never heard of. In the world of cybersecurity, vulnerabilities are discovered so often, and at such a high rate, that it can be very difficult to keep up with. Some vulnerabilities will start ringing alarm bells within your security tooling, while others are far more nuanced, but still pose an…
Read MoreAug 30, 2024Ravie LakshmananCryptojacking / Vulnerability Threat actors are actively exploiting a now-patched, critical security flaw impacting the Atlassian Confluence Data Center and Confluence Server to conduct illicit cryptocurrency mining on susceptible instances. “The attacks involve threat actors that employ methods such as the deployment of shell scripts and XMRig miners, targeting of SSH endpoints,…
Read MoreEmotet first appeared in 2014, but like Zeus, is now a modular program most often used to deliver other forms of malware, with Trickster and Ryuk being two prominent examples. Emotet is so good at what it does that Arne Schoenbohm, head of the German Federal Office for Information Security, calls it the “king of…
Read MoreAug 30, 2024Ravie LakshmananCyber Espionage / Threat Intelligence Chinese-speaking users are the target of a “highly organized and sophisticated attack” campaign that is likely leveraging phishing emails to infect Windows systems with Cobalt Strike payloads. “The attackers managed to move laterally, establish persistence and remain undetected within the systems for more than two weeks,” Securonix…
Read MoreSANS Institute Unveils Critical Infrastructure Strategy Guide for 2024: A Call to Action for Securing ICS/OT Environments
by nlqip
Aug 30, 2024The Hacker NewsICS Security / OT Security A comprehensive guide authored by Dean Parsons emphasizes the growing need for specialized ICS security measures in the face of rising cyber threats. With a staggering 50% increase in ransomware attacks targeting industrial control systems (ICS) in 2023, the SANS Institute is taking decisive action by…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA