Month: August 2024
New details are emerging about a breach at National Public Data (NPD), a consumer data broker that recently spilled hundreds of millions of Americans’ Social Security Numbers, addresses, and phone numbers online. KrebsOnSecurity has learned that another NPD data broker which shares access to the same consumer records inadvertently published the passwords to its back-end…
Read MoreSuspected hackers behind the heist of $14,000,000 worth of cryptocurrency from blockchain tech firm Holograph was arrested in Italy after living a lavish lifestyle for weeks in the country. As announced over the weekend by Italy’s national police force (Polizia di Stato), four individuals suspected of cybercrime and money laundering have been living in a…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-23897 Jenkins Command Line Interface (CLI) Path Traversal Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk…
Read More‘Our aim is to be more valuable to our clients tomorrow than we are today,’ says Rich Falcone, president of Ahead. ‘If we can achieve that, growth will naturally follow.’ Nearly six months after Ahead acquired CDI, the combined company is ready to drive significant value for customers and reshape its go-to-market strategy. “Now that…
Read MoreFlight tracking platform FlightAware is asking some users to reset their account login passwords due to a data security incident that may have exposed personal information. The technology company is based in Houston, Texas and provides real-time as well as historical flight tracking data. FlightAware is considered the world’s largest flight-tracking platform with a network…
Read MoreCRN breaks down Forrester’s new report on the 10 most important cloud trends right know, which include Nvidia significantly aiding AI cloud startups, VMware customers migrating to the public cloud and the converging of AI and edge computing. From VMware migrations to the public cloud and Nvidia helping cloud AI startups win market share, Forrester’s…
Read MoreAug 19, 2024Ravie LakshmananMalvertising / Cybercrime Cybersecurity researchers have uncovered a surge in malware infections stemming from malvertising campaigns distributing a loader called FakeBat. “These attacks are opportunistic in nature, targeting users seeking popular business software,” the Mandiant Managed Defense team said in a technical report. “The infection utilizes a trojanized MSIX installer, which executes…
Read MoreAug 19, 2024Ravie LakshmananThreat Intelligence / Cryptocurrency A new type of malware called UULoader is being used by threat actors to deliver next-stage payloads like Gh0st RAT and Mimikatz. The Cyberint Research Team, which discovered the malware, said it’s distributed in the form of malicious installers for legitimate applications targeting Korean and Chinese speakers. There…
Read More“Combining our high-performance Instinct AI accelerator, EPYC CPU, and networking product portfolios with ZT Systems’ industry-leading data center systems expertise will enable AMD to deliver end-to-end data center AI infrastructure at scale with our ecosystem of OEM and ODM partners,” said AMD CEO Lisa Su. Chipmaker superstar AMD is acquiring server supplier and cloud computing…
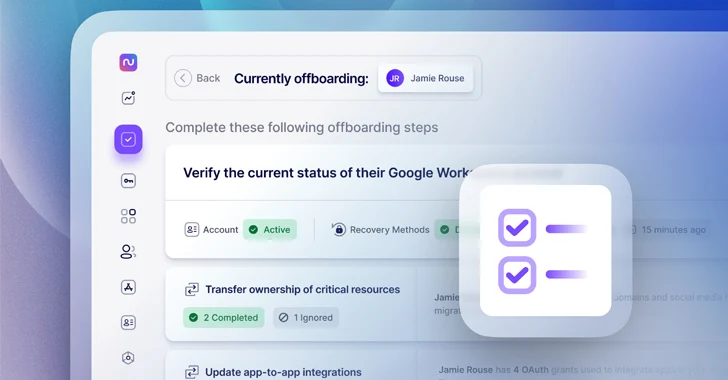
Read MoreAccording to recent research on employee offboarding, 70% of IT professionals say they’ve experienced the negative effects of incomplete IT offboarding, whether in the form of a security incident tied to an account that wasn’t deprovisioned, a surprise bill for resources that aren’t in use anymore, or a missed handoff of a critical resource or…
Read MoreRecent Posts
- Trump Touts New $20B Data Center Investment In US
- AMD Wins Over Dell In Commercial PC Deal For Ryzen AI Pro Chips
- Google Gemini AI Coming To TVs And Smartwatches: CES 2025
- CISA Adds Three Known Exploited Vulnerabilities to Catalog | CISA
- CISA Releases Two Industrial Control Systems Advisories | CISA