Month: August 2024
‘We need partners to get these products into those spaces, so we’re all in supporting partners with what they need to win in these situations,’ Tim Madsen, vice president of marketing for Minnesota-based uninterrupted power system maker CyberPower, tells CRN. ‘We’re evolving and adding products and services to these lines with channel partners in mind.…
Read MoreMicrosoft warned Entra global admins on Thursday to enable multi-factor authentication (MFA) for their tenants until October 15 to ensure users don’t lose access to admin portals. This is part of Redmond’s recently announced Secure Future Initiative (SFI) and it aims to ensure that Azure accounts are protected against phishing and hijacking attempts by enforcing…
Read MoreIt’s a situation that would seem nonsensical on the surface, but AMD’s James Knight and Supermicro’s Ken Kajikawa say the unique customer engagements reflect the highly collaborative nature of their partnership and how they differ from competitors. AMD and Supermicro are large tech companies, but senior leaders at both firms said they have the capacity…
Read MoreBackground check service National Public Data confirms that hackers breached its systems after threat actors leaked a stolen database with millions of social security numbers and other sensitive personal information. The company states that the breached data may include names, email addresses, phone numbers, social security numbers (SSNs), and postal addresses. Breach linked to late…
Read MoreIT admins usually know what to watch out for when end users are creating weak, easy-to-guess passwords. However, a common yet overlooked type of weak password are keyboard walk patterns. A keyboard walk password typically refers to a password created by moving sequentially over the keyboard keys in a pattern that resembles walking. These are…
Read MoreImage: MidjourneyCISA warned on Thursday that attackers are exploiting a recently patched critical vulnerability in SolarWinds’ Web Help Desk solution for customer support. Web Help Desk (WHD) is IT help desk software widely used by large corporations, government agencies, and healthcare and education organizations worldwide to centralize, automate, and streamline help desk management tasks. Tracked…
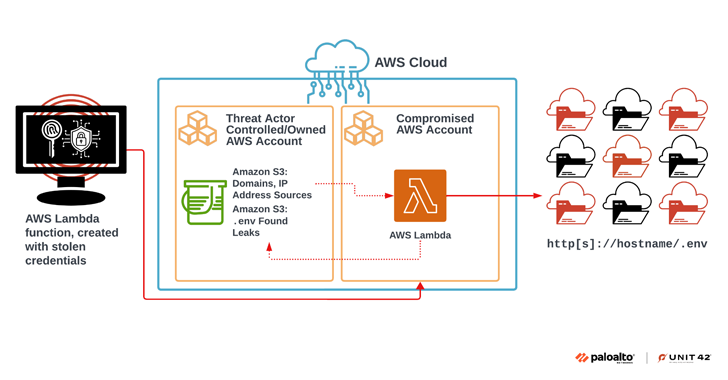
Read MoreAug 16, 2024Ravie LakshmananCloud Security / Application Security A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files (.env) that contain credentials associated with cloud and social media applications. “Multiple security missteps were present in the course of this campaign, including the following: Exposing environment variables, using long-lived…
Read MoreCisco CEO Chuck Robbins cited ‘several $100 million-plus transactions in the quarter.’ Deep cuts at Cisco Systems appear aimed at readying the 40-year-old networking giant for increased customer demand to modernize technology for improved security and artificial intelligence growth – areas where Cisco partners can see business gains in the new fiscal year. These are…
Read More‘You need to strengthen your client relationships, your team collaboration and your service consistency. That’s going to increase your efficiency, your operational maturity and, ultimately, your sales, your revenue and your profitability,’ says Ray Mann, channel development manager at ScalePad. Ray Mann, channel development manager at ScalePad, told an audience of MSPs at XChange August…
Read More‘There is a certain amount of cloud repatriation that is happening, and that’s happening purely from a cost perspective,’ Cognizant’s Naveen Sharma tells CRN in an interview. Naveen Sharma compares the classic public cloud vendor business model to buying wine. The seller loves for a customer to try a glass, and then maybe drink another,…
Read MoreRecent Posts
- Opinion: Why Nvidia, MediaTek May Enter The PC CPU Market Soon
- Microsoft VP Of Silicon Engineering Jumps To Google Cloud To Head Chip Technology And Manufacturing
- 10 Cloud Startup Companies To Watch In 2025
- Cybersecurity Snapshot: After Telecom Hacks, CISA Offers Security Tips for Cell Phone Users, While Banks Seek Clearer AI Regulations
- IBM’s Hashicorp Acquisition Now Faces UK Investigation