Month: August 2024
As Rodgers puts it, “What got you here won’t get you there. You know how to configure a firewall, but now you have to communicate to executives. You have to know the business and be able to talk about your technology, your security, the solution through the language of the business. Being able to have…
Read MoreOn July 19, 2024, a seemingly routine CrowdStrike update caused a global IT meltdown. Millions of systems running Windows 10 and later experienced vital failures, bringing banks, airports, and critical infrastructure to a halt. The cause? A configuration error in the CrowdStrike Falcon sensor update. The CrowdStrike outage was more than just a temporary inconvenience;…
Read MoreAug 15, 2024Ravie LakshmananCyber Attack / Social Engineering Russian and Belarusian non-profit organizations, Russian independent media, and international non-governmental organizations active in Eastern Europe have become the target of two separate spear-phishing campaigns orchestrated by threat actors whose interests align with that of the Russian government. While one of the campaigns – dubbed River of…
Read MoreClearScale CEO Jimmy Chui explains why price-concerned VMware customers need to migrate to AWS, his company’s new AI-powered offerings to help them, and why businesses need to ‘really get off all their licensed software.’ ClearScale is launching an AI-powered attack seeking to migrate existing VMware customers worried about price increases over to the AWS cloud.…
Read MoreCisco CEO Chuck Robbins says his team is “shifting hundreds of millions of dollars into AI,” including AI networking for cloud, AI infrastructure, silicon and cybersecurity. Cisco Systems crossed $1 billion to date in AI orders with webscale customers and predicts another $1 billion in AI product orders this fiscal year. On the San Jose,…
Read MoreAug 15, 2024Ravie LakshmananRansomware / Cybercrime A cybercrime group with links to the RansomHub ransomware has been observed using a new tool designed to terminate endpoint detection and response (EDR) software on compromised hosts, joining the likes of other similar programs like AuKill (aka AvNeutralizer) and Terminator. The EDR-killing utility has been dubbed EDRKillShifter by…
Read MoreAug 15, 2024The Hacker NewsIdentity Security / Threat Detection The Emergence of Identity Threat Detection and Response Identity Threat Detection and Response (ITDR) has emerged as a critical component to effectively detect and respond to identity-based attacks. Threat actors have shown their ability to compromise the identity infrastructure and move laterally into IaaS, Saas, PaaS…
Read MoreAs Rodgers puts it, “What got you here won’t get you there. You know how to configure a firewall, but now you have to communicate to executives. You have to know the business and be able to talk about your technology, your security, the solution through the language of the business. Being able to have…
Read MoreAug 15, 2024Ravie LakshmananCyber Espionage / Data Theft A previously unknown threat actor has been attributed to a spate of attacks targeting Azerbaijan and Israel with an aim to steal sensitive data. The attack campaign, detected by NSFOCUS on July 1, 2024, leveraged spear-phishing emails to single out Azerbaijani and Israeli diplomats. The activity is…
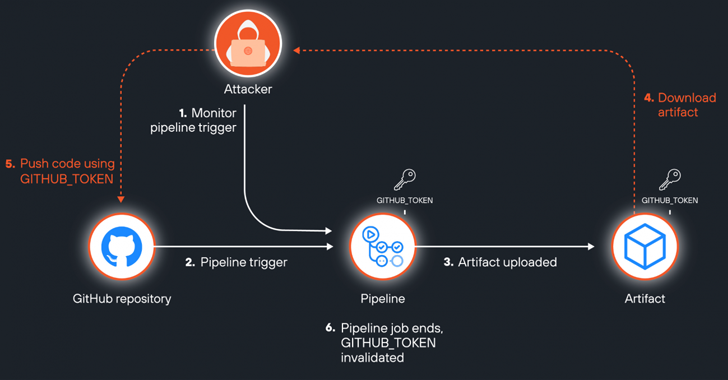
Read MoreAug 15, 2024Ravie LakshmananCloud Security / DevOps A newly discovered attack vector in GitHub Actions artifacts dubbed ArtiPACKED could be exploited to take over repositories and gain access to organizations’ cloud environments. “A combination of misconfigurations and security flaws can make artifacts leak tokens, both of third party cloud services and GitHub tokens, making them…
Read More