Month: August 2024
Google says it is taking a privacy-minded approach to the integration of AI features on Android devices, implementing end-to-end protection to secure data in transit while keeping the most sensitive data locally on the device. The data that reaches Google’s cloud infrastructure for processing is protected by state-of-the-art encryption, access controls, and tight unauthorized access monitoring.…
Read MoreA critical vulnerability in SolarWinds’ Web Help Desk solution for customer support could be exploited to achieve remote code execution, the American business software developer warns in a security advisory today. The company has released a hotfix and says that the security issue, tracked as CVE-2024-28986, is a Java deserialization that would allow an attacker to run commands…
Read More‘What’s important about the channel is it’s a community. …This is where you have an opportunity to learn from your peers. All that knowledge is just sitting right here that can help you with some challenge you’re having,’ says Corey Kirkendoll, president and CEO of 5K Technical Services. When it’s time for an MSP to…
Read MoreTenable Recognized as the Top Performer in Cloud Security by CRN 2024 Annual Report Card Award
by nlqip
Tenable®, the exposure management company, today announced it was named the top performer in cloud security in the 2024 CRN Annual Report Card Award from CRN®, a brand of The Channel Company. This award honors technology vendors for providing best-in-class products, partner program resources, partner support and managed and cloud services. “It is a great…
Read MoreAug 14, 2024The Hacker NewsPassword Security / Cyber Security Simply relying on traditional password security measures is no longer sufficient. When it comes to protecting your organization from credential-based attacks, it is essential to lock down the basics first. Securing your Active Directory should be a priority – it is like making sure a house…
Read MoreA coalition of law enforcement agencies coordinated by the U.K. National Crime Agency (NCA) has led to the arrest and extradition of a Belarussian and Ukrainian dual-national believed to be associated with Russian-speaking cybercrime groups. Maksim Silnikau (aka Maksym Silnikov), 38, went by the online monikers J.P. Morgan, xxx, and lansky. He was extradited to…
Read MoreScams Your phone number is more than just a way to contact you – scammers can use it to target you with malicious messages and even exploit it to gain access to your bank account or steal corporate data 13 Aug 2024 • , 5 min. read Last month, we looked at how scammers can…
Read MoreTwo critical vulnerabilities Of the two critical vulnerabilities addressed in the patch day, the more severe is an authentication bypass flaw (CVE-2024-41730) with a CVSS score of 9.8/10 affecting SAP’s BusinessObjects business intelligence platform, while the other is a server-side request forgery (SSRF) vulnerability in applications built with SAP Build Apps. CVE-2024-41730, as described by…
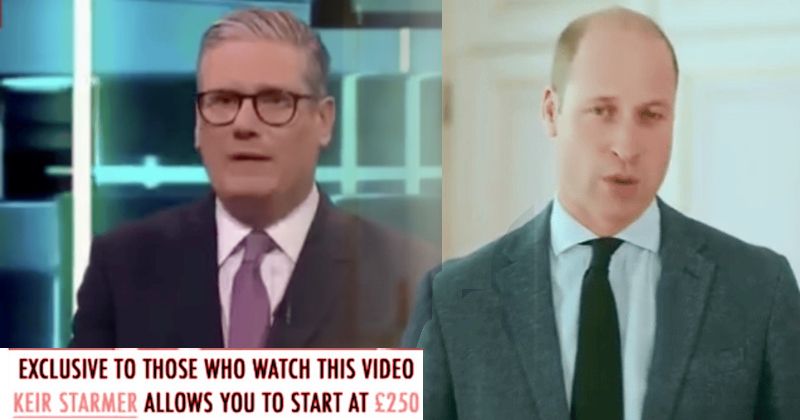
Read MoreScammers are once again using deepfake technology to dupe unwary internet Facebook and Instagram users into making unwise cryptocurrency investments. AI-generated videos promoting fraudulent cryptocurrency trading platform Immediate Edge have used deepfake footage of British Prime Minister Sir Keir Starmer and His Royal Highness Prince William to reach an estimated 890,000 people via Meta’s social…
Read MoreIvanti released a patch for a critical severity authentication bypass vulnerability and a warning that exploit code is publicly available Background On August 13, Ivanti released a security advisory to address a critical severity authentication bypass vulnerability in its Virtual Traffic Manager (vTM) product, a software-based application delivery controller (ADC). CVE Description CVSSv3 CVE-2024-7593 Ivanti…
Read MoreRecent Posts
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption
- Stellar Startup Data Center Tech Vendors To Know In 2024