Month: August 2024
On the Voynich Manuscript Really interesting article on the ancient-manuscript scholars who are applying their techniques to the Voynich Manuscript. No one has been able to understand the writing yet, but there are some new understandings: Davis presented her findings at the medieval-studies conference and published them in 2020 in the journal Manuscript Studies. She…
Read MoreThe U.S. Federal Bureau of Investigation (FBI) on Monday announced the disruption of online infrastructure associated with a nascent ransomware group called Dispossessor (aka Radar). The effort saw the dismantling of three U.S. servers, three United Kingdom servers, 18 German servers, eight U.S.-based criminal domains, and one German-based criminal domain. Dispossessor is said to be…
Read MoreMoreover, under a 2023 AI safety and security White House executive order, NIST released last week three final guidance documents and a draft guidance document from the newly created US AI Safety Institute, all intended to help mitigate AI risks. NIST also re-released a test platform called Dioptra for assessing AI’s “trustworthy” characteristics, namely AI…
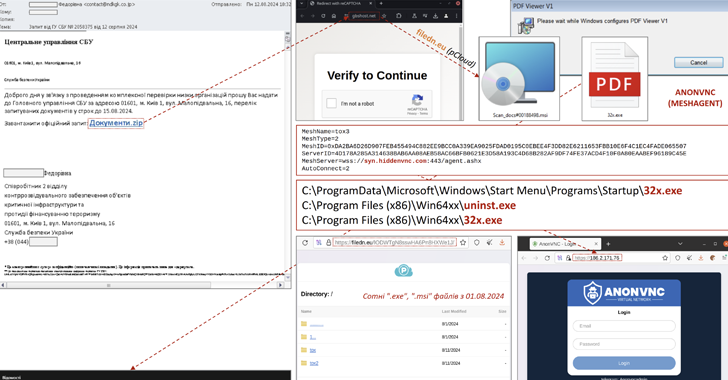
Read MoreAug 13, 2024Ravie LakshmananThreat Intelligence / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign that masquerades as the Security Service of Ukraine to distribute malware capable of remote desktop access. The agency is tracking the activity under the name UAC-0198. More than 100 computers are estimated to…
Read MoreEuropean privacy advocate NOYB (None of Your Business) has filed nine GDPR complaints about X using the personal data from over 60 million users in Europe to train “Grok,” the social media company’s large language model. According to NOYB, X did not inform its users that their data was being used to train AI and did…
Read MoreThe FBI announced on Monday that it seized the servers and websites of the Radar/Dispossessor ransomware operation following a joint international investigation. The joint operation was carried out in collaboration with the U.K.’s National Crime Agency, the Bamberg Public Prosecutor’s Office, and the Bavarian State Criminal Police Office (BLKA). Law enforcement seized three U.S. servers,…
Read MoreOnline privacy is the protection of personal data and control over what information is shared while using the internet. Despite the efforts of companies and governments, achieving complete privacy is nearly impossible due to the pervasive collection and trade of personal data. The internet tracks and collects various personal details, which can be bought, sold,…
Read MoreSouth Korea’s ruling party, People Power Party (PPP), claims that North Korean hackers have stolen crucial information about K2 tanks, the country’s main battle tank, as well as its “Baekdu” and “Geumgang” spy planes. PPP fears that DPRK will use this information to evade military surveillance and gain an advantage on the battlefield, so it’s…
Read MoreMicrosoft announced that the Paint 3D graphics app will be discontinued later this year and removed from the Microsoft Store in November. The 3D graphics program was first unveiled as a replacement for the Paint application eight years ago, in November 2016, with the release of Windows 10 Insider Build 14971. The company advises users to…
Read More“Switching to shorter life cycles of certificates significantly reduces these risks and is a necessary step.” Venafi chief innovation officer Kevin Bocek said. However, he admits that “the introduction of 90-day certificates means that companies have to renew their certificates five times more frequently than before. This is a five-fold increase in effort.” Challenges caused…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA