Month: August 2024
Introduction to Data Security Compliance Keeping data safe from cyberthreats is critical for a number of reasons. But one area that requires particularly close attention is ensuring firms are on the right side of the various data protection and privacy regulations in force around the world. This requires data security compliance. The term refers to…
Read More“AMD’s decision to exclude older processors from the ‘Sinkclose’ vulnerability patch risks damaging customer trust and brand loyalty,” said Arjun Chauhan, senior analyst at Everest Group. “Enterprises using these still-popular chips may feel neglected, leading to dissatisfaction and potentially driving them to consider competitors who offer longer support lifecycles.” Notably, AMD’s recently released Ryzen 9000…
Read MoreAug 12, 2024Ravie LakshmananCybersecurity / Network Security The maintainers of the FreeBSD Project have released security updates to address a high-severity flaw in OpenSSH that attackers could potentially exploit to execute arbitrary code remotely with elevated privileges. The vulnerability, tracked as CVE-2024-7589, carries a CVSS score of 7.4 out of a maximum of 10.0, indicating…
Read MoreAfter a good year of sustained exuberance, the hangover is finally here. It’s a gentle one (for now), as the market corrects the share price of the major players (like Nvidia, Microsoft, and Google), while other players reassess the market and adjust priorities. Gartner calls it the trough of disillusionment, when interest wanes and implementations…
Read MoreAug 12, 2024Ravie LakshmananCritical Infrastructure / Vulnerability Cybersecurity researchers have identified a number of security shortcomings in photovoltaic system management platforms operated by Chinese companies Solarman and Deye that could enable malicious actors to cause disruption and power blackouts. “If exploited, these vulnerabilities could allow an attacker to control inverter settings that could take parts…
Read MoreTaxonomy of Generative AI Misuse Interesting paper: “Generative AI Misuse: A Taxonomy of Tactics and Insights from Real-World Data“: Generative, multimodal artificial intelligence (GenAI) offers transformative potential across industries, but its misuse poses significant risks. Prior research has shed light on the potential of advanced AI systems to be exploited for malicious purposes. However, we…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/why-dcap-is-essential-for-modern-data-security-a-closer-look” on this server. Reference #18.ef7dead.1723457074.785a211 https://errors.edgesuite.net/18.ef7dead.1723457074.785a211 Source link lol
Read MoreA notorious ransomware group has demanded more than half a billion dollars from victims in less than two years. That staggering statistic has been made public in an update to a joint advisory issued by the US Cybersecurity and Infrastructure Agency (CISA) and the FBI, warning organisations about the threat posed by the BlackSuit gang.…
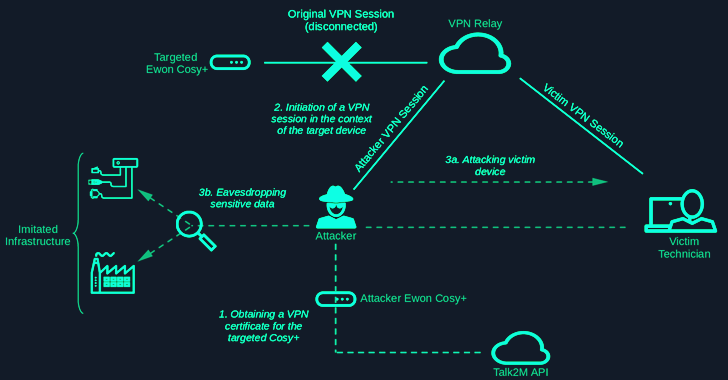
Read MoreAug 12, 2024Ravie LakshmananOperational Technology / Network Security Security vulnerabilities have been disclosed in the industrial remote access solution Ewon Cosy+ that could be abused to gain root privileges to the devices and stage follow-on attacks. The elevated access could then be weaponized to decrypt encrypted firmware files and encrypted data such as passwords in…
Read MoreBooker, a former CISO at UnitedHealth Group, says the attack also serves as a blaring reminder to healthcare organizations to “make sure you focus on the basics and essential security measures, like multifactor authentication, have them where you need them, which is everywhere, and have a way to know that what you’re doing is right,…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA