Month: August 2024
Aug 12, 2024Ravie LakshmananCloud Security / Malware The Russian government and IT organizations are the target of a new campaign that delivers a number of backdoors and trojans as part of a spear-phishing campaign codenamed EastWind. The attack chains are characterized by the use of RAR archive attachments containing a Windows shortcut (LNK) file that,…
Read MoreAlmost 2.7 billion records of personal information for people in the United States were leaked on a hacking forum, exposing names, social security numbers, all known physical addresses, and possible aliases. The data allegedly comes from National Public Data, a company that collects and sells access to personal data for use in background checks, to obtain criminal records,…
Read MoreX has always had a bot problem, but now scammers are utilizing the Ukraine war and earthquake warnings in Japan to entice users into clicking on fake content warnings and videos that lead to scam adult sites, malicious browser extensions, and shady affiliate sites. For months, X has been flooded with posts that contain what…
Read MoreA series of targeted cyberattacks that started at the end of July 2024, targeting dozens of systems used in Russian government organizations and IT companies, are linked to Chinese hackers of the APT31 and APT 27 groups. Kaspersky, who discovered the activity, dubbed the campaign “EastWind,” reporting that it employs an updated version of the…
Read MoreFor the 39th year, solution providers scored vendors across 27 technology categories based on their performance in product innovation, support, partnership, and managed and cloud services. Here’s a roundup of the companies with the highest overall scores. Making The Grade For the 39th year, CRN offered solution providers in North America the opportunity to grade…
Read MoreAug 11, 2024Ravie LakshmananSupply Chain / Software Security Cybersecurity researchers have discovered a new malicious package on the Python Package Index (PyPI) repository that masquerades as a library from the Solana blockchain platform but is actually designed to steal victims’ secrets. “The legitimate Solana Python API project is known as ‘solana-py’ on GitHub, but simply…
Read MoreCritical Infrastructure In this high-stakes year for democracy, the importance of robust election safeguards and national cybersecurity strategies cannot be understated 09 Aug 2024 • , 3 min. read The mention of election security, especially in a year where the majority of the world is destined to vote, brings to mind images of a voting…
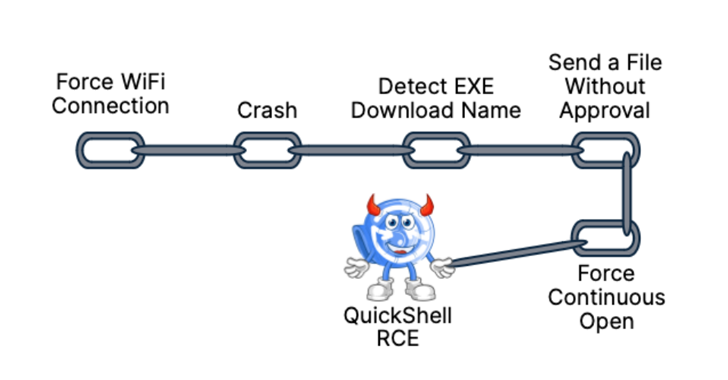
Read MoreAug 10, 2024Ravie LakshmananVulnerability / Mobile Security As many as 10 security flaws have been uncovered in Google’s Quick Share data transfer utility for Android and Windows that could be assembled to trigger remote code execution (RCE) chain on systems that have the software installed. “The Quick Share application implements its own specific application-layer communication…
Read MoreVideo Unsurprisingly, many discussions focused on the implications of the recent CrowdStrike outage, including the lessons it may have offered for bad actors 09 Aug 2024 This week was that time of the year when thousands of cybersecurity experts descended on Las Vegas to attend Black Hat USA, one of the world’s top cybersecurity conferences.…
Read MoreUpdate with further information from Microsoft. Microsoft has disclosed a high-severity vulnerability affecting Office 2016 that could expose NTLM hashes to a remote attacker. Tracked as CVE-2024-38200, this security flaw is caused by an information disclosure weakness that enables unauthorized actors to access protected information. The zero-day impacts multiple 32-bit and 64-bit Office versions, including Office…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA