Month: August 2024
U.S. law enforcement has arrested two suspected admins of the WWH-Club stolen credit card marketplace after they went on a cash spending spree in Florida. The suspects are Russian national Pavel Kublitskii and Kazakhstan native Alexandr Khodyrev, who were arrested for their roles as administrators and moderators of the cybercrime platform WWH-Club. The two men have…
Read MoreMicrosoft has reminded customers that multiple editions of Windows 11 21H2 and 22H2 will reach the end of servicing in 60 days, on October 8, 2024. The announcement applies to Windows 11 22H2 Home, Pro, Pro Education, Pro for Workstations, and SE editions released on September 20, 2022. On the same day, Windows 11 21H2…
Read MoreAug 10, 2024Ravie LakshmananBrowser Security / Online Fraud An ongoing, widespread malware campaign has been observed installing rogue Google Chrome and Microsoft Edge extensions via a trojan distributed via fake websites masquerading as popular software. “The trojan malware contains different deliverables ranging from simple adware extensions that hijack searches to more sophisticated malicious scripts that…
Read MoreAug 10, 2024Ravie LakshmananVulnerability / Enterprise Security Microsoft has disclosed an unpatched zero-day in Office that, if successfully exploited, could result in unauthorized disclosure of sensitive information to malicious actors. The vulnerability, tracked as CVE-2024-38200 (CVSS score: 7.5), has been described as a spoofing flaw that affects the following versions of Office – Microsoft Office…
Read MoreDeploying low-level malware implants Once an attacker manages to execute malicious code inside the SMM they could potentially inject a persistent malware implant inside the UEFI, but this depends on the platform’s configuration, as UEFI can have additional protections such as AMD’s ROM Armor, which controls access to the SPI flash memory where UEFI is…
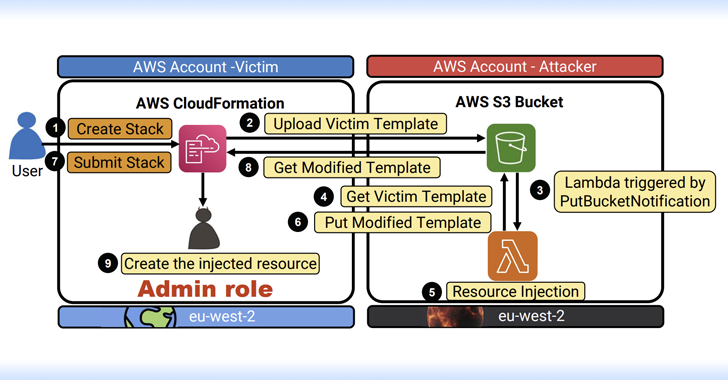
Read MoreAug 09, 2024Ravie LakshmananCloud Security / Data Protection Cybersecurity researchers have discovered multiple critical flaws in Amazon Web Services (AWS) offerings that, if successfully exploited, could result in serious consequences. “The impact of these vulnerabilities range between remote code execution (RCE), full-service user takeover (which might provide powerful administrative access), manipulation of AI modules, exposing…
Read MoreThe infosecurity world came together in Las Vegas this week for Black Hat USA 2024, offering presentations and product announcements that will give CISOs plenty to consider. Here are the top takeaways CISOs should keep in mind when adapting their cybersecurity strategies going forward. [For more Black Hat USA coverage, see “Black Hat: Latest news…
Read MoreFriday Squid Blogging: SQUID Is a New Computational Tool for Analyzing Genomic AI Yet another SQUID acronym: SQUID, short for Surrogate Quantitative Interpretability for Deepnets, is a computational tool created by Cold Spring Harbor Laboratory (CSHL) scientists. It’s designed to help interpret how AI models analyze the genome. Compared with other analysis tools, SQUID is…
Read MoreRussia’s telecommunications watchdog Roskomnadzor has restricted access to the Signal encrypted messaging service for what it describes as violations of Russian anti-terrorism and anti-extremism legislation. “User access to the messenger Signal is restricted due to violations of the requirements of the Russian legislation whose fulfillment is necessary to prevent the use of the messenger for…
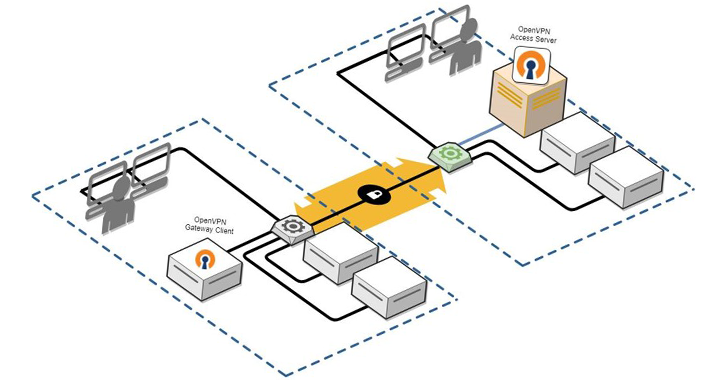
Read MoreAug 09, 2024Ravie LakshmananVulnerability / Network Security Microsoft on Thursday disclosed four medium-severity security flaws in the open-source OpenVPN software that could be chained to achieve remote code execution (RCE) and local privilege escalation (LPE). “This attack chain could enable attackers to gain full control over targeted endpoints, potentially resulting in data breaches, system compromise,…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA