Month: August 2024
‘I don’t think we’re ever done when it comes to improving the platform. I think it can continue to get better year over year as we master automation with MSPs’ says Aharon Chernin, Rewst founder and CEO. Automation platform company Rewst has secured $45 million in funding to accelerate the pace of innovation in its…
Read MoreAmerican building security giant ADT confirmed it suffered a data breach after threat actors leaked allegedly stolen customer data on a popular hacking forum. ADT is a public American company that specializes in security and smart home solutions for residential and small business customers. The firm employs 14,300 people, has an annual revenue of $4.98…
Read MoreMoreover, such attacks could disrupt operations by compromising critical infrastructure, leading to downtime and financial losses. Industries with stringent compliance requirements, such as financial services, healthcare, and the public sector, are particularly vulnerable. A successful downgrade attack in these sectors could result in regulatory penalties and significant damage to an organization’s reputation and customer trust.”…
Read MoreAug 08, 2024The Hacker NewsCyber Threat Management The last few years have seen more than a few new categories of security solutions arise in hopes of stemming a never-ending tidal wave of risks. One of these categories is Automated Security Validation (ASV), which provides the attacker’s perspective of exposures and equips security teams to continuously…
Read MoreThe DPC also plans to refer the matter to the European Data Protection Board. Kaur noted that X, already with a history of GDPR non-compliance, now faces heightened pressure to improve data protection practices, enhance transparency, and restore user trust, particularly in Europe. The DPC’s actions also underscore a broader trend of stringent data protection…
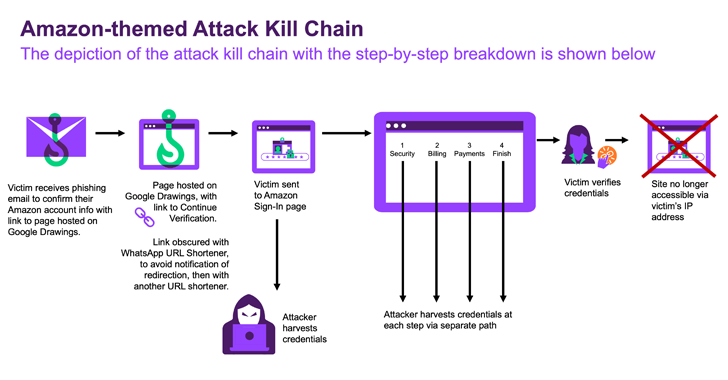
Read MoreAug 08, 2024Ravie LakshmananNetwork Security / Cloud Security Cybersecurity researchers have discovered a novel phishing campaign that leverages Google Drawings and shortened links generated via WhatsApp to evade detection and trick users into clicking on bogus links designed to steal sensitive information. “The attackers chose a group of the best-known websites in computing to craft…
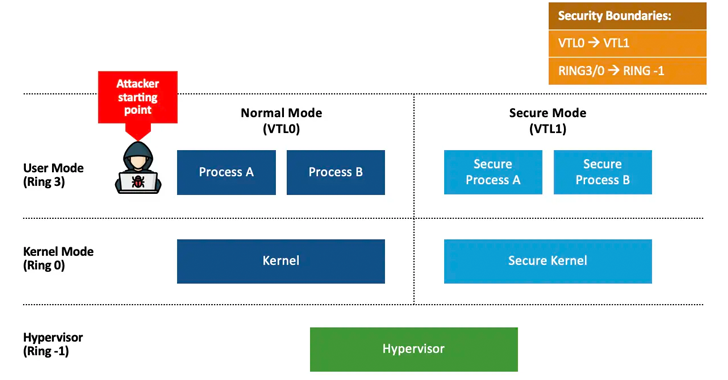
Read MoreAug 08, 2024Ravie LakshmananWindows Security / Vulnerability Microsoft said it is developing security updates to address two loopholes that it said could be abused to stage downgrade attacks against the Windows update architecture and replace current versions of the Windows files with older versions. The vulnerabilities are listed below – CVE-2024-38202 (CVSS score: 7.3) –…
Read MoreUnlock the Future of Cybersecurity: Exclusive, Next Era AI Insights and Cutting-Edge Training at SANS Network Security 2024
by nlqip
Aug 08, 2024The Hacker NewsArtificial Intelligence / Network Security The Immersive Experience Happening This September in Las Vegas! In an era of relentless cybersecurity threats and rapid technological advancement, staying ahead of the curve is not just a necessity, but critical. SANS Institute, the premier global authority in cybersecurity training, is thrilled to announce Network…
Read MoreAug 08, 2024Ravie LakshmananVulnerability / Network Security A critical security flaw impacting Progress Software WhatsUp Gold is seeing active exploitation attempts, making it essential that users move quickly to apply the latest. The vulnerability in question is CVE-2024-4885 (CVSS score: 9.8), an unauthenticated remote code execution bug impacting versions of the network monitoring application released…
Read MoreAug 08, 2024Ravie LakshmananCritical Infrastructure / Malware The ransomware strain known as BlackSuit has demanded as much as $500 million in ransoms to date, with one individual ransom demand hitting $60 million. That’s according to an updated advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI). “BlackSuit…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict