Month: August 2024
Attackers are increasingly using new phishing toolkits (open-source, commercial, and criminal) to execute adversary-in-the-middle (AitM) attacks. AitM enables attackers to not just harvest credentials but steal live sessions, allowing them to bypass traditional phishing prevention controls such as MFA, EDR, and email content filtering. In this article, we’re going to look at what AitM phishing…
Read MoreU.S. cybersecurity and intelligence agencies have called out an Iranian hacking group for breaching multiple organizations across the country and coordinating with affiliates to deliver ransomware. The activity has been linked to a threat actor dubbed Pioneer Kitten, which is also known as Fox Kitten, Lemon Sandstorm (formerly Rubidium), Parisite, and UNC757, which it described…
Read MoreAngler employed advanced evasion techniques, including checking for virtual machines and sandbox environments to avoid detection by security researchers, leading to its popularity and significance in the cybersecurity community. Angler’s activities ceased abruptly in mid-2016, reportedly, due to law enforcement actions in Russia against cybercriminals allegedly linked to Angler. First charged in 2023 The Belarusian…
Read More2024 looks set to be the highest-grossing year yet for ransomware gangs, due – in no small part – to emboldened cybercriminals causing costly disruption at larger companies. Read more in my article on the Exponential-e blog. Source link lol
Read MoreHackers who seized control of the official Instagram account of McDonald’s claim that they managed to steal US $700,000 from unsuspecting investors by promoting a fake cryptocurrency. Earlier this month, hackers promoted a worthless cryptocurrency token they dubbed “GRIMACE” to the 5.1 million people following McDonald’s Instagram account. At the same time, tweets from the…
Read MoreIf you’ve been in cybersecurity for the past five to 10 years, you’ve probably heard the term “threat-informed defense.” Simply stated, a threat-informed defense focuses security teams, technologies, and budgets on those threats most likely to impact a particular organization, industry, geography, etc. The concept basically aligns with the famous (and often referenced) quote from…
Read MoreAug 29, 2024Ravie LakshmananOnline Crime / Privacy French prosecutors on Wednesday formally charged CEO Pavel Durov with facilitating a litany of criminal activity on the popular messaging platform and placed him under formal investigation following his arrest Saturday. Russian-born Durov, who is also a French citizen, has been charged with being complicit in the spread…
Read MoreThe cybersecurity vendor is finding ‘enduring trust’ from many customers in the wake of the massive Windows outage in July, CrowdStrike Co-founder and CEO George Kurtz said Wednesday. CrowdStrike CEO George Kurtz said Wednesday that the cybersecurity vendor has found “enduring trust” expressed by many customers in recent weeks, following the massive Microsoft Windows outage…
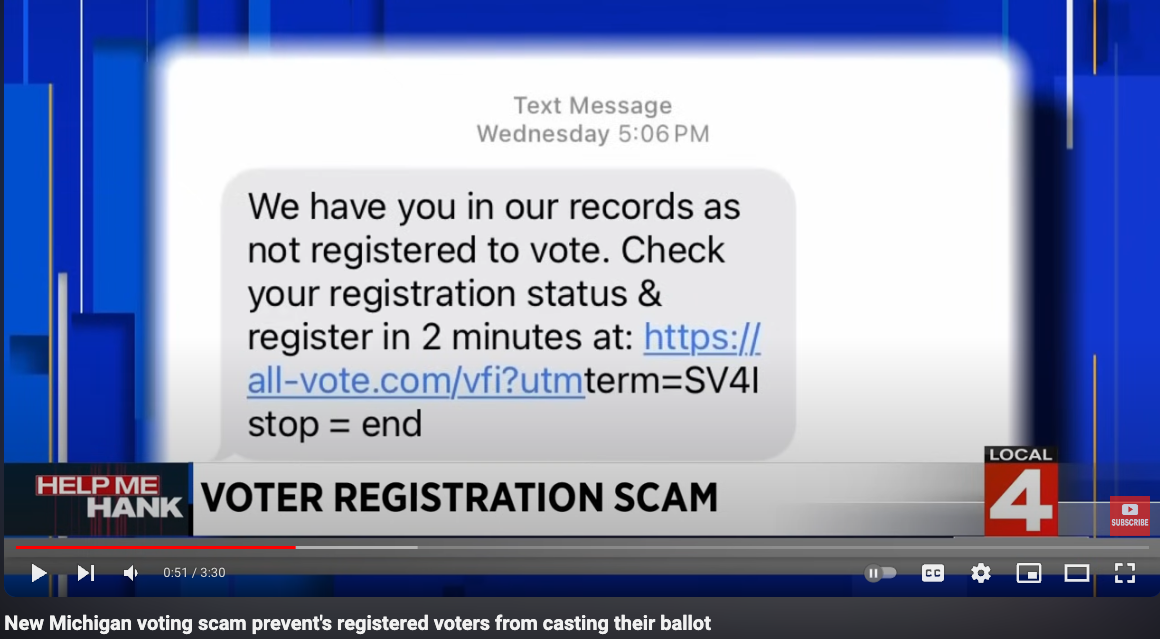
Read MoreMultiple media reports this week warned Americans to be on guard against a new phishing scam that arrives in a text message informing recipients they are not yet registered to vote. A bit of digging reveals the missives were sent by a California political consulting firm as part of a well-meaning but potentially counterproductive get-out-the-vote…
Read MoreFinally in April 2022, the group launched a major attack that crippled 27 Costa Rican government organizations causing disruptions in the country’s customs and taxes platforms, impacting foreign trade and payroll payments. In response, the US State Department put up a $10 million reward for information about the identity or location of Conti’s leaders, as…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm