Month: August 2024
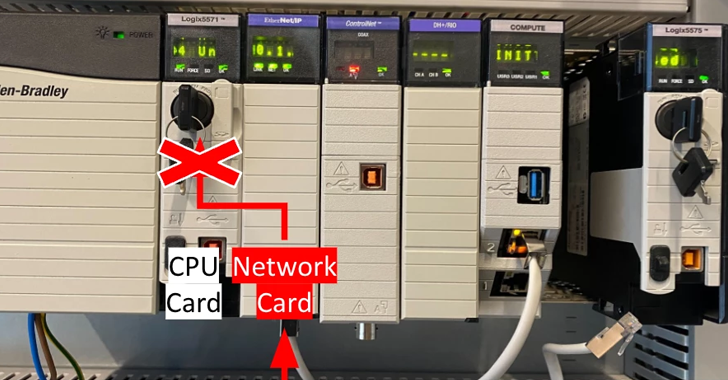
Aug 05, 2024Ravie LakshmananNetwork Security / Vulnerability A high-severity security bypass vulnerability has been disclosed in Rockwell Automation ControlLogix 1756 devices that could be exploited to execute common industrial protocol (CIP) programming and configuration commands. The flaw, which is assigned the CVE identifier CVE-2024-6242, carries a CVSS v3.1 score of 8.4. “A vulnerability exists in…
Read MoreAs organizations increasingly seek to support and secure more remote network connections, many are rethinking the traditional VPN. Many VPN alternatives exist to help secure remote access — mesh VPNs chief among them. Mesh virtual private networks (VPNs) use a peer-to-peer architecture that can theoretically be less expensive than traditional VPN approaches. VPNs, which are estimated…
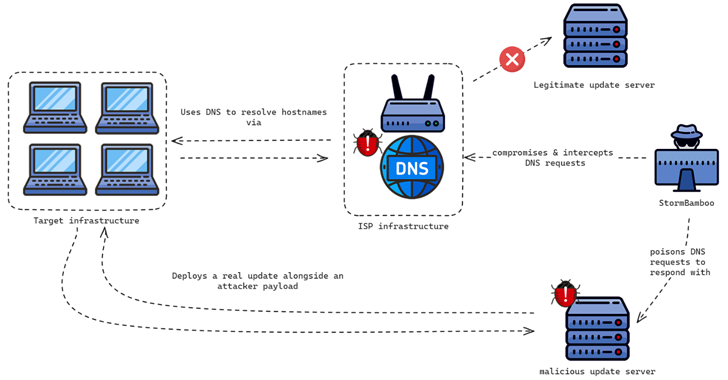
Read MoreAug 05, 2024Ravie LakshmananBrowser Security / Windows Security The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider (ISP) to push malicious software updates to target companies in mid-2023, highlighting a new level of sophistication associated with the group. Evasive Panda, also known by the names Bronze Highland, Daggerfly, and StormBamboo,…
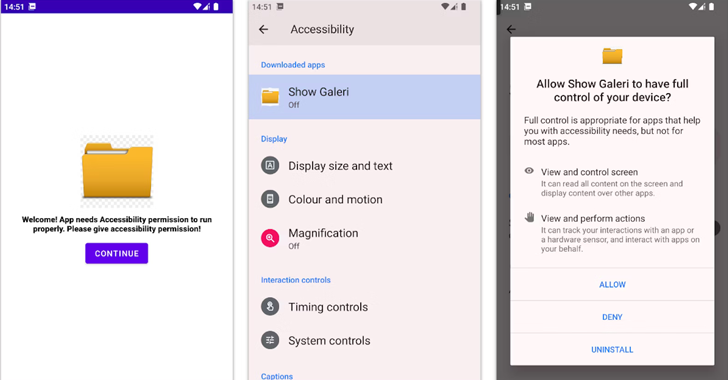
Read MoreAug 05, 2024Ravie LakshmananMobile Security / Financial Security Cybersecurity researchers have discovered a new Android banking trojan called BlankBot targeting Turkish users with an aim to steal financial information. “BlankBot features a range of malicious capabilities, which include customer injections, keylogging, screen recording and it communicates with a control server over a WebSocket connection,” Intel…
Read MoreA massive Magniber ransomware campaign is underway, encrypting home users’ devices worldwide and demanding thousand-dollar ransoms to receive a decryptor. Magniber launched in 2017 as a successor to the Cerber ransomware operation when it was spotted being distributed by the Magnitude exploit kit. Since then, the ransomware operation has seen bursts of activity over the…
Read MoreA Chinese hacking group tracked as StormBamboo has compromised an undisclosed internet service provider (ISP) to poison automatic software updates with malware. Also tracked as Evasive Panda, Daggerfly, and StormCloud, this cyber-espionage group has been active since at least 2012, targeting organizations across mainland China, Hong Kong, Macao, Nigeria, and various Southeast and East Asian countries. On…
Read MoreA novel Linux Kernel cross-cache attack named SLUBStick has a 99% success in converting a limited heap vulnerability into an arbitrary memory read-and-write capability, letting the researchers elevate privileges or escape containers. The discovery comes from a team of researchers from the Graz University of Technology who demonstrated the attack on Linux kernel versions 5.9 and 6.2 (latest) using…
Read MoreVideo Organizations that leveraged AI and automation in security prevention cut the cost of a data breach by US$2.22 million compared to those that didn’t deploy these technologies, according to IBM 02 Aug 2024 Organizations that leveraged the power of artificial intelligence (AI) and automation in security prevention cut the cost of a data breach…
Read MoreAug 03, 2024Ravie LakshmananPrivacy / Data Protection The U.S. Department of Justice (DoJ), along with the Federal Trade Commission (FTC), filed a lawsuit against popular video-sharing platform TikTok for “flagrantly violating” children’s privacy laws in the country. The agencies claimed the company knowingly permitted children to create TikTok accounts and to view and share short-form…
Read MoreAug 03, 2024Ravie LakshmananDDoS Attack / Server Security Cybersecurity researchers have disclosed details of a new distributed denial-of-service (DDoS) attack campaign targeting misconfigured Jupyter Notebooks. The activity, codenamed Panamorfi by cloud security firm Aqua, utilizes a Java-based tool called mineping to launch a TCP flood DDoS attack. Mineping is a DDoS package designed for Minecraft…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA